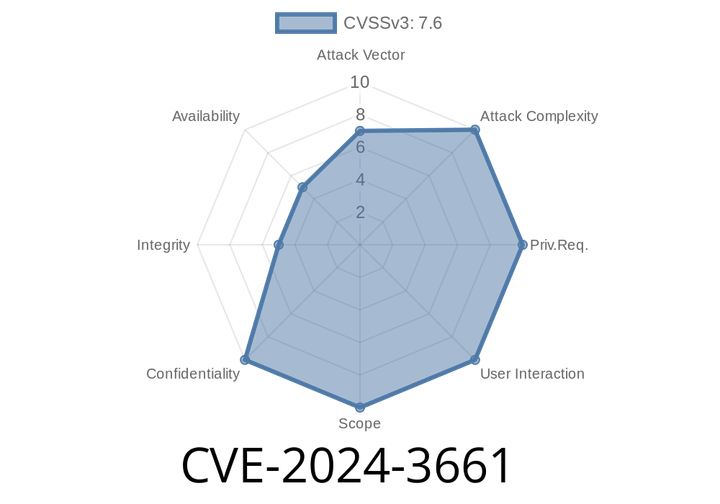
CVE-2024-3661 - How DHCP Route Injection Exposes VPN Traffic to Attackers (With Exploit Example)
Summary:
A new vulnerability, CVE-2024-3661, exposes a flaw in how VPNs rely on routing rules for security. By abusing DHCP’s _classless static route option_
CVE-2024-34447 - How Bouncy Castle’s Java APIs Let DNS Poisoning Slip Through — Details, Code, and Exploitation
If you use Java for SSL communication, chances are you've bumped into Bouncy Castle, a popular library for cryptographic functions. But until version
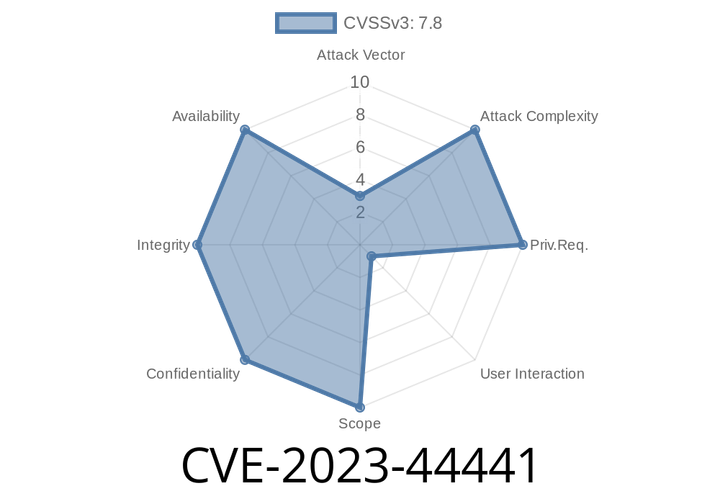
CVE-2023-44441 - Remote Code Execution in GIMP via DDS File Parsing (Heap-based Buffer Overflow)
Summary:
A critical vulnerability, tracked as CVE-2023-44441 (also ZDI-CAN-22093), was discovered in GIMP (GNU Image Manipulation Program). This bug allows attackers to execute arbitrary code
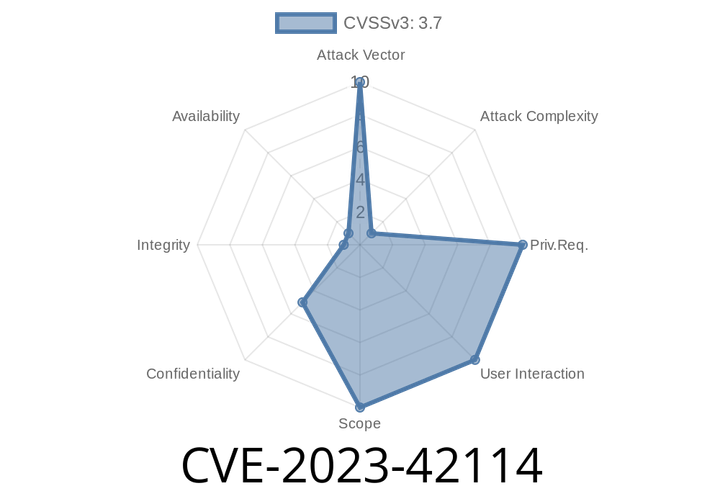
CVE-2023-42114 - Exim NTLM Challenge Out-Of-Bounds Read – How Attackers Can Leak Your Data (with Exploit Example)
Exim is one of the most popular mail transport agents used on Unix-like systems—so any security issue can have big effects. In September 2023,
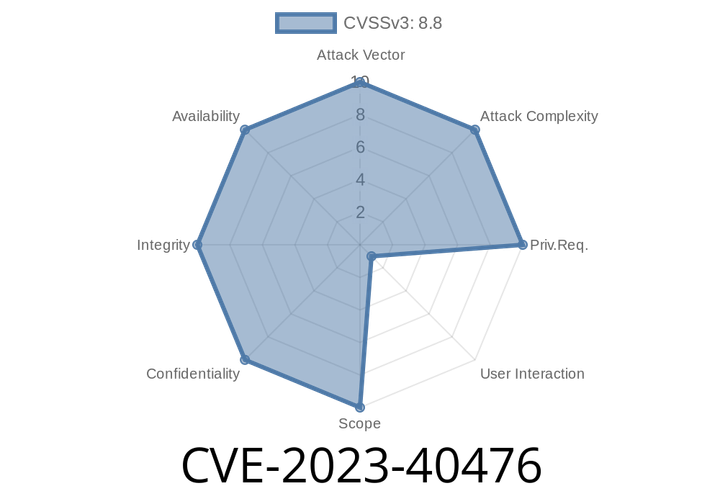
CVE-2023-40476 - GStreamer H265 Parsing Stack Overflow Leads to Remote Code Execution
GStreamer is a widely-used open source multimedia framework that powers video and audio streaming in many Linux desktop environments and media applications. In August 2023,
Episode
00:00:00
00:00:00