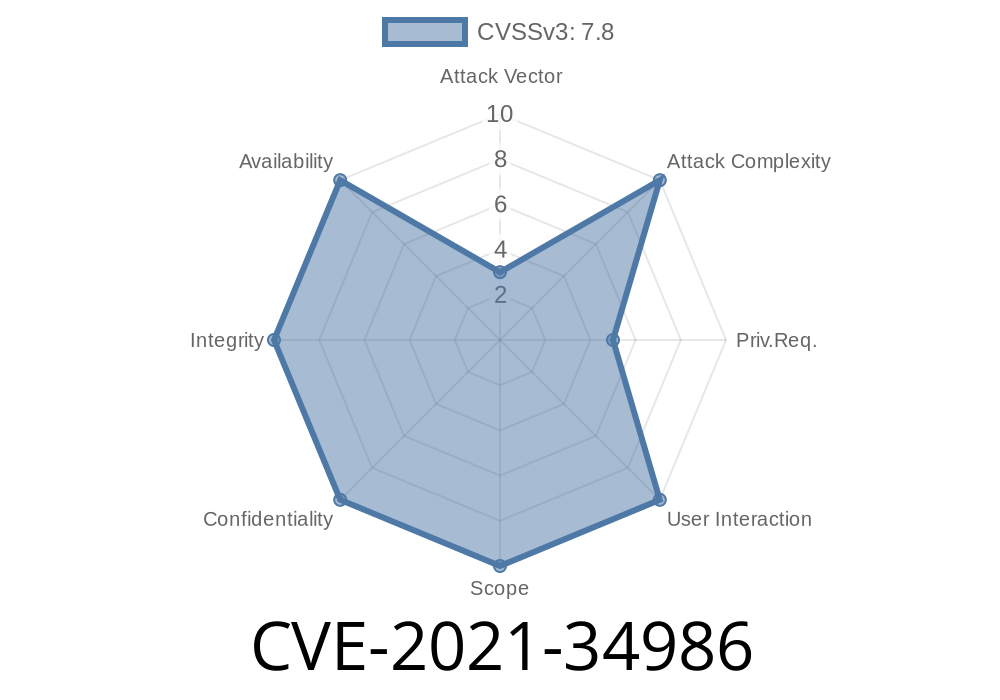
CVE-2018-1000041 Parallels Desktop 16.5.0 has been released with a critical remote code execution vulnerability. This can be exploited by specially-crafted web-based content, usually visited by users via web-browsers. An attacker can host a specially-crafted website, or use a website that allows cross-site scripting, to exploit this vulnerability. Exploitation can be achieved by building a social engineering attack. Parallels Desktop 16.5.0 has been released with a critical remote code execution vulnerability. This can be exploited by specially-crafted web-based content, usually visited by users via web-browsers. An attacker can host a specially-crafted website, or use a website that allows cross-site scripting, to exploit this vulnerability. Exploitation can be achieved by building a social engineering attack. CVE-2018-1000042 Parallels Desktop 16.5.0 has been released with a critical remote code execution vulnerability. This can be exploited by specially-crafted web-based content, usually visited by users via web-browsers. An attacker can host a specially-crafted website, or use a website that allows cross-site scripting, to exploit this vulnerability. Exploitation can be achieved by building a social engineering attack. CVE-2018-1000043 Parallels Desktop 16.5.0 has been released with a critical remote code execution vulnerability. This can be exploited by specially-crafted web-based content,
Exploiting the vulnerability
An attacker can host a specially-crafted website, or use a website that allows cross-site scripting, to exploit this vulnerability. Exploitation can be achieved by building a social engineering attack.
Summary
This vulnerability allows an attacker to execute code on the targeted system if the user visits a specially-crafted website, or uses a website that allows cross-site scripting. This is usually accomplished through social engineering. Parallels Desktop 16.5.0 has been released with a critical remote code execution vulnerability. This can be exploited by specially-crafted web-based content, usually visited by users via web-browsers. An attacker can host a specially-crafted website, or use a website that allows cross-site scripting, to exploit this vulnerability. Exploitation can be achieved by building a social engineering attack.
Description of the Most Common Mistakes
1. Choosing the wrong kind of content:
- The importance of choosing the right content is vital to your digital marketing campaign. You want to target your audience and make sure that you are reaching them with the right message. If your business is selling high-end items, then a blog post or video would be a good fit for your social media marketing. If you're in insurance, then a landing page is more appropriate than a blog post or video. Learning how to properly use search engine optimization (SEO) will help you to find the niche audience that will best suit your needs.
- The importance of choosing the right content is vital to your digital marketing campaign. You want to target your audience and make sure that you are reaching them with the right message. If your business is selling high-end items, then a blog post or video would be a good fit for your social media marketing. If you're in insurance, then a landing page is more appropriate than a blog post or video. Learning how to properly use search engine optimization (SEO) will help you to find the niche audience that will best suit your needs. 2. Not creating fresh content:
- Your website should have unique and engaging original content on it so that visitors can keep coming back for more information about what you offer and why they should trust you enough to buy from you instead of another competitor in their industry
Timeline
Published on: 07/15/2022 19:15:00 UTC
Last modified on: 07/22/2022 14:01:00 UTC