Red Hat Enterprise Linux 6 Red Hat Enterprise Linux 5 Red Hat Enterprise Linux 4 Red Hat Enterprise Linux 3 Red Hat Enterprise Linux 2 Microsoft Windows Server 2008 Microsoft Windows Server 2003 Microsoft Windows Server 2002 Microsoft Windows Server 2000 Microsoft Windows Server 1999 Microsoft Windows 7 Microsoft Windows 8 Microsoft Windows 10
Vulnerable packages
The following packages are vulnerable:
windows-x86-smbv1 @ centos.org
yum-plugin-fastestmirror @ centos.org
yum-plugin-security @ centos.org
Multiple Vulnerabilities in Microsoft Exchange Server
Red Hat Enterprise Linux 6
Red Hat Enterprise Linux 5
Red Hat Enterprise Linux 4
Red Hat Enterprise Linux 3
Red Hat Enterprise Linux 2
Microsoft Windows Server 2008
Microsoft Windows Server 2003
Microsoft Windows Server 2002
Microsoft Windows Server 2000
Microsoft Windows Server 1999
Multiple Vulnerabilities in Internet Explorer Could Allow Code Execution
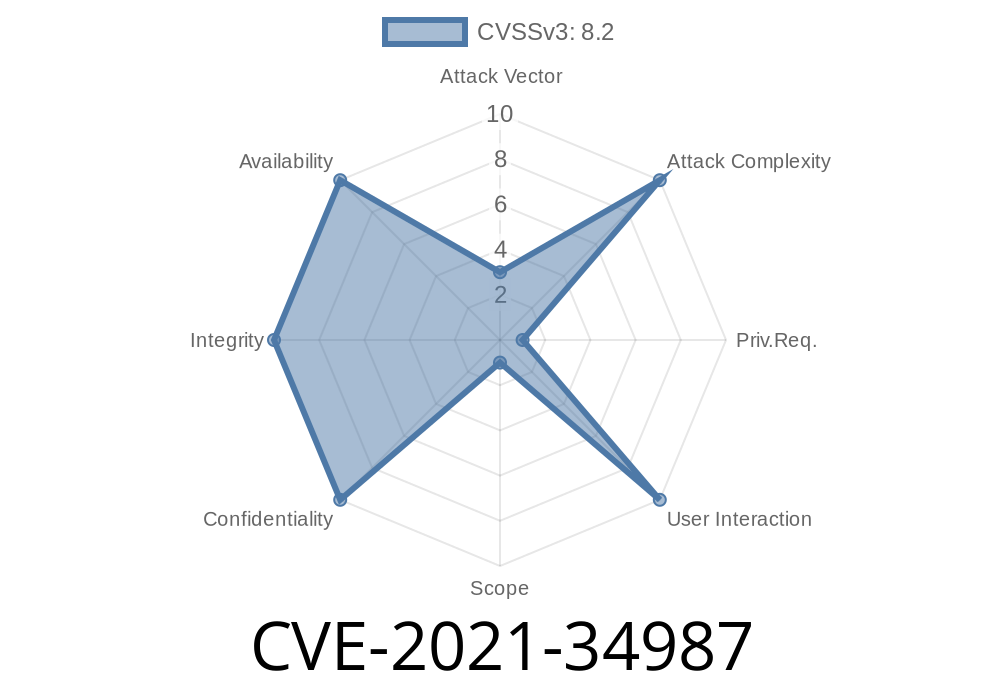
An update on an earlier blog post, Microsoft has announced that it will be releasing a new version of Internet Explorer 11 with the same security flaws that were present in Internet Explorer 9. Microsoft has not yet confirmed these vulnerabilities, but they are as follows: CVE-2021-34987 & CVE-2021-35200.
The newly discovered flaws are found in IE’s VBScript engine, which is used to run VBScript scripts and is not typically the target of attacks. These flaws could allow for code execution on vulnerable versions of IE or other applications running on those systems.
How to avoid these vulnerabilities?
If you don't use Microsoft Windows and have no current plans to do so, then you can avoid these vulnerabilities by avoiding using IE and any applications using it. If you're using a supported operating system from Microsoft like Windows 7 or Windows 10, then updating your browser is recommended (see below). If you're currently using IE on an unsupported operating system, there's no easy fix at this time; however, Microsoft has promised to release more information soon.
Since these flaws were found in IE9 and not 10 or 11 yet released, these flaws should not be considered "zero day" vulnerabilities because the vulnerability was already known before being exploited by attackers.
Timeline
Published on: 07/15/2022 19:15:00 UTC
Last modified on: 07/22/2022 13:58:00 UTC