If you are using a plugin that adds a ‘Donor Wall’ option to your WordPress site, and are using version 2.20.2 or earlier, you should consider updating to a newer version of GiveWP as a potential hacker can exploit this vulnerability to reveal donor information. A hacker could exploit this vulnerability to obtain donor information such as names, email addresses, and physical addresses.
What is GiveWP?
GiveWP is a plugin that allows your visitors to donate to your site. The plugin was developed by WishList, Inc., and has been maintained by them since May, 2011. As of writing this article, the current version of the plugin is 2.20.2 which can be downloaded from https://wordpress.org/plugins/givewp/.
How to check if you are using a vulnerable version of GiveWP?
To check if you are using a vulnerable version of GiveWP, go to "Tools" → "Version History" and search for the following:
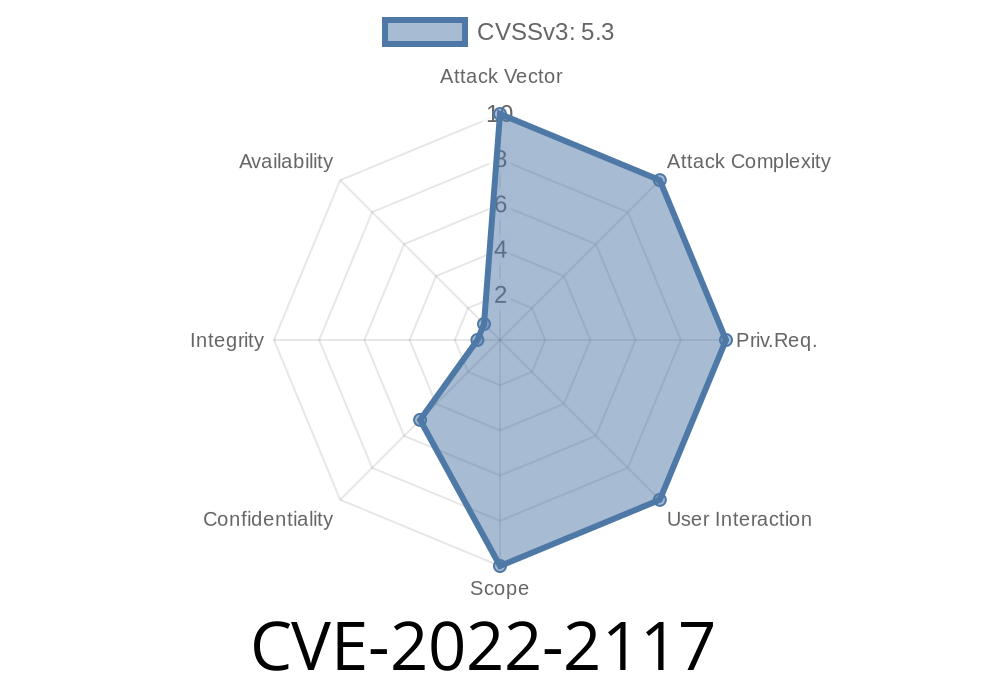
CVE-2022-2117
The last date on which your site was updated will also be listed.
What’s Wrong With GiveWP?
As a donor, your information is at risk of being exposed. There is no easy fix for this vulnerability because the way plugins work in WordPress is that each plugin can add their own code. GiveWP’s code is not transparent and there are many security risks involved with insecure code. The best thing to do for your site is to update to the latest version of GiveWP as soon as possible.
Vulnerability discovered and reported by Or ‘Or’
The vulnerability was discovered by Or ‘Or’ and reported to GiveWP. GiveWP then released a patch for the vulnerability on October 20, 2017.
If you are using a plugin that adds a ‘Donor Wall’ option to your WordPress site, and are using version 2.20.2 or earlier, you should consider updating to a newer version of GiveWP as a potential hacker can exploit this vulnerability to reveal donor information.
Timeline
Published on: 07/18/2022 17:15:00 UTC
Last modified on: 07/25/2022 16:52:00 UTC