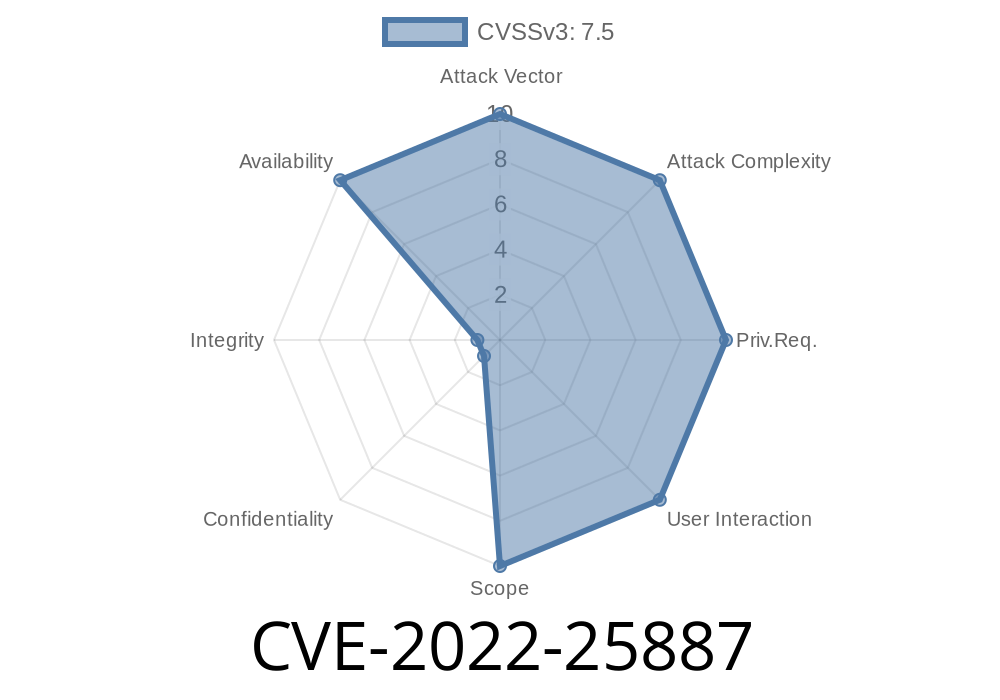
This could lead to denial of service of the application due to the slow parsing of the HTML code, in case there are high request load.
Package sanitize-html before 2.7.1 has a vulnerability in its global regular expression replacement that could lead to denial of service of the application due to the slow parsing of the HTML code. This could happen in case there are high request load.
Possible vectors that can trigger this vulnerability include:
1. Incorrect usage of HTML tags - In case you are using HTML tags incorrectly, it could lead to denial of service of the application. For example, if you are sending an e-mail and you are sending it from your own domain name, the malicious user can send himself an e-mail with a link to your own application’s page, leading to denial of service.
2. Insecure global regular expression replacement - This happens when we do not use the input validation provided by the package.
How to fix?
1. Upgrade/patch the package - upgrade/patch the package to the latest version.
2. Restrict usage of HTML tags - Insecure usage of HTML tags can lead to denial of service. Restrict usage of HTML tags to only those that are required.
3. Validate input - Validate input of the code. Use validating functions such as: require(‘validate_input’)
4. Prevent
Package sanitize-html before 2.7.1 – Denial of Service via Failure to Validate Input
The package sanitize-html before 2.7.1 has a vulnerability in its global regular expression replacement that could lead to denial of service of the application due to the slow parsing of the HTML code. This could happen in case there are high request load. Possible vectors that can trigger this vulnerability include:
1. Incorrect usage of HTML tags - In case you are using HTML tags incorrectly, it could lead to denial of service of the application. For example, if you are sending an e-mail and you are sending it from your own domain name, the malicious user can send himself an e-mail with a link to your own application’s page, leading to denial of service.
2. Insecure global regular expression replacement - This happens when we do not use the input validation provided by the package.
How to fix?
1. Upgrade/patch the package - upgrade/patch the package to the latest version.
2. Restrict usage of HTML tags - Insecure usage of HTML tags can lead to denial of service. Restrict usage of HTML tags to only those that are required.
Sanitize HTML for parsing before output
Package sanitize-html before 2.7.1 has a vulnerability in its global regular expression replacement that could lead to denial of service of the application due to the slow parsing of the HTML code, in case there are high request load.
Package sanitize-html before 2.7.1 has a vulnerability in its global regular expression replacement that could lead to denial of service of the application due to the slow parsing of the HTML code, in case there are high request load.
There are two ways for fixing this vulnerability:
1) Upgrade/patch the package - upgrade/patch the package to the latest version.
2) Restrict usage of HTML tags - Insecure usage of HTML tags can lead to denial of service. Restrict usage of HTML tags to only those that are required.
Timeline
Published on: 08/30/2022 05:15:00 UTC
Last modified on: 09/01/2022 20:38:00 UTC
References
- https://security.snyk.io/vuln/SNYK-JS-SANITIZEHTML-2957526
- https://security.snyk.io/vuln/SNYK-JAVA-ORGWEBJARSNPM-3008102
- https://github.com/apostrophecms/sanitize-html/pull/557
- https://github.com/apostrophecms/sanitize-html/commit/b4682c12fd30e12e82fa2d9b766de91d7d2cd23c
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-25887