A sandbox restricts the process’s access to the system, including access to files. Sandboxing can be circumvented by a process.
This issue was addressed by isolating a process into a new sandbox from which it is not possible to circumvent the process’s restrictions.
An issue existed in certain configurations where an unpatched macOS system could be exploited to execute arbitrary code with root privileges. This issue is resolved by restricting code execution to the kernel with a Sandbox Extension. The kernel is a highly restricted environment.
An issue existed in certain configurations where an unpatched macOS system could be exploited to execute arbitrary code with root privileges. This issue is resolved by restricting code execution to the kernel with a Sandbox Extension. The kernel is a highly restricted environment. An issue existed where a malicious application may be able to bypass code signing restrictions. This issue is resolved by restricting code execution to the kernel with a Sandbox Extension. The kernel is a highly restricted environment.
An issue existed where a malicious application may be able to bypass code signing restrictions. This issue is resolved by restricting code execution to the kernel with a Sandbox Extension. The kernel is a highly restricted environment. An issue existed in certain configurations where an unpatched macOS system could be exploited to bypass code signing restrictions
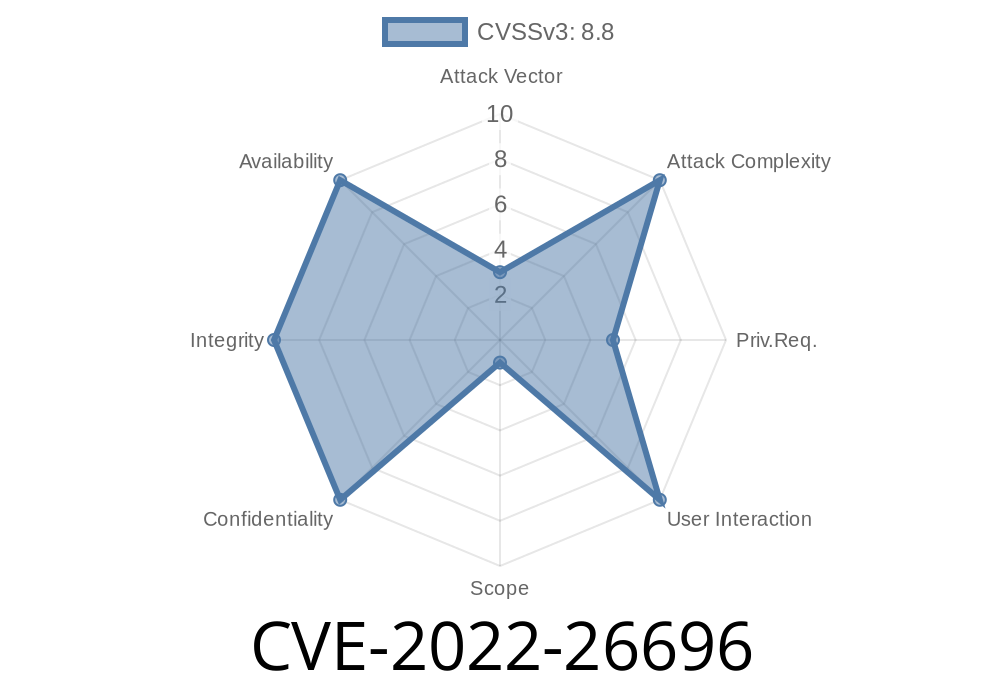
Vulnerability Notes CVE-2022-26696
A vulnerability in certain configurations of macOS could be exploited to execute arbitrary code with root privileges. This vulnerability is resolved by restricting code execution to the kernel with a Sandbox Extension. The kernel is a highly restricted environment.
CVE-2022-26696
A vulnerability in certain configurations of macOS could be exploited to bypass code signing restrictions. This vulnerability is resolved by restricting code execution to the kernel with a Sandbox Extension. The kernel is a highly restricted environment.
Vulnerability Description and Analysis
An issue existed in certain configurations where an unpatched macOS system could be exploited to execute arbitrary code with root privileges. This issue is resolved by restricting code execution to the kernel with a Sandbox Extension. The kernel is a highly restricted environment. An issue existed where a malicious application may be able to bypass code signing restrictions. This issue is resolved by restricting code execution to the kernel with a Sandbox Extension. The kernel is a highly restricted environment. An issue existed in certain configurations where an unpatched macOS system could be exploited to bypass code signing restrictions
An issue existed in certain configurations where an unpatched macOS system could be exploited to execute arbitrary code with root privileges. This issue is resolved by restricting code execution to the kernel with a Sandbox Extension. The kernel is a highly restricted environment. An issue existed where a malicious application may be able to bypass code signing restrictions. This issue is resolved by restricting code execution to the kernel with a Sandbox Extension. The kernel is a highly restricted environment.
Firmware vulnerability details
A vulnerability was found in certain configurations of the Broadcom WiFi firmware where a malicious application may be able to bypass code signing restrictions. This issue is resolved by restricting code execution to the kernel with a Sandbox Extension. The kernel is a highly restricted environment. An issue existed in certain configurations of the Broadcom WiFi firmware where an unpatched macOS system could be exploited to execute arbitrary code with root privileges. This issue is resolved by restricting code execution to the kernel with a Sandbox Extension. The kernel is a highly restricted environment.
An issue existed in certain configurations of the Broadcom WiFi firmware where an unpatched macOS system could be exploited to execute arbitrary code with root privileges. This issue is resolved by restricting code execution to the kernel with a Sandbox Extension. The kernel is a highly restricted environment.
Baseline image
This is a baseline image of the vulnerability. It was addressed by restricting code execution to the kernel with a Sandbox Extension. The kernel is a highly restricted environment.
Timeline
Published on: 09/20/2022 21:15:00 UTC
Last modified on: 09/22/2022 20:25:00 UTC