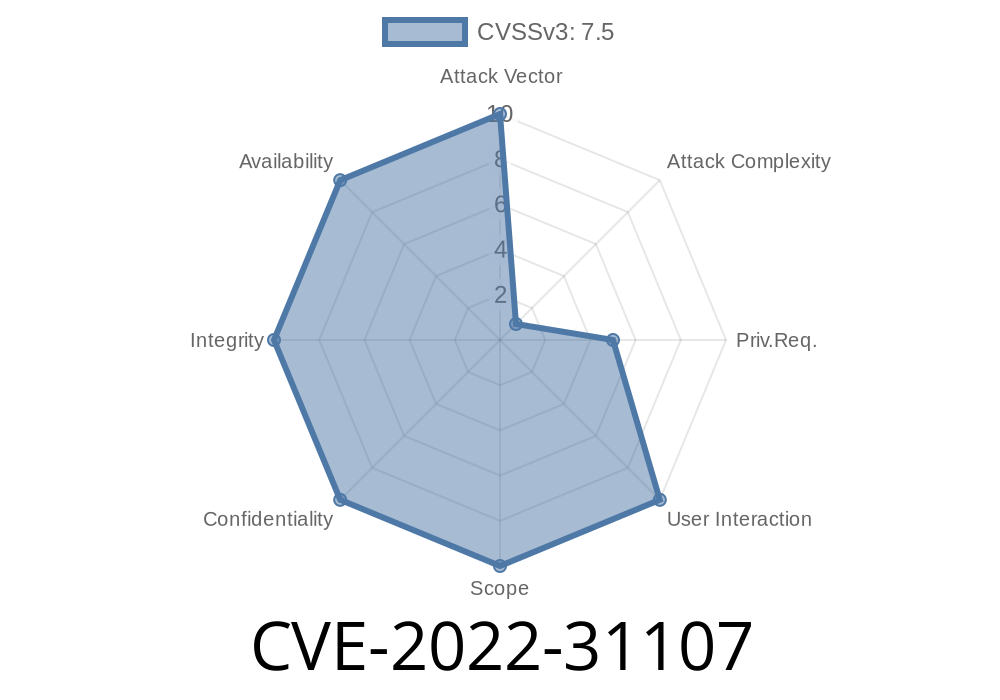
as that user. This allows the malicious user to gain access to all of the Grafana data for the target user's account and see that user's dashboards and data, even if that data is marked as private. This issue does not affect access to the Grafana web user interface and does not allow the malicious user to send data to external systems. It is only possible to perform this attack if the user has authorized the malicious user to access the OAuth IdP. This issue has been fixed in version 9.0.4. If a user is using an OAuth IdP that is not configured with the email address of the Grafana server, and the user's external user id is not already associated with an account in the Grafana server, the user will have to log in to the Grafana server via that OAuth IdP and their external user id, then log in to the Grafana server using their configured username and password. This issue does not affect access to the Grafana web user interface or the ability for the malicious user to send data to external systems. It is only possible to perform this attack if the user has authorized the malicious user to access the OAuth IdP.
CVE-2022-31108
If the malicious user has already logged in to the Grafana server via an authorized OAuth IdP and they have access to the data of other users, they can alter that data. For example, if the malicious user only has access to the data of one other user on their account, they could add a second device with a different name and connect it to their account. This issue does not affect access to the Grafana web user interface or the ability for the malicious user to send data to external systems. It is only possible to perform this attack if the user has authorized the malicious user to access an OAuth IdP that is not configured with email address of Grafana server.
References
- https://www.grafanadotcom/blog/CVE-2022-31107
- https://support.grafanadotcom/hc/en-us/articles/36000177697
Users must authorize the malicious user to access their OAuth IdP
The malicious user must have authorization from the target user to access their OAuth IdP.
Summary
A flaw in the Grafana front-end allowed a malicious user to gain access to all of the Grafana data for the target user's account and see that user's dashboards and data, even if that data is marked as private. This issue does not affect access to the Grafana web user interface or send data to external systems. It only affects if a user is using an OAuth IdP that is not configured with the email address of the Grafana server. If a user's external user id is not already associated with an account in the Grafana server, they will have to log in to the Grafana server via that OAuth IdP and their external user id, then log in using their configured username and password.
Timeline
Published on: 07/15/2022 13:15:00 UTC
Last modified on: 07/22/2022 16:58:00 UTC
References
- https://grafana.com/docs/grafana/next/release-notes/release-notes-8-4-10/
- https://grafana.com/docs/grafana/next/release-notes/release-notes-9-0-3/
- https://github.com/grafana/grafana/security/advisories/GHSA-mx47-6497-3fv2
- https://grafana.com/docs/grafana/next/release-notes/release-notes-8-5-9/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-31107