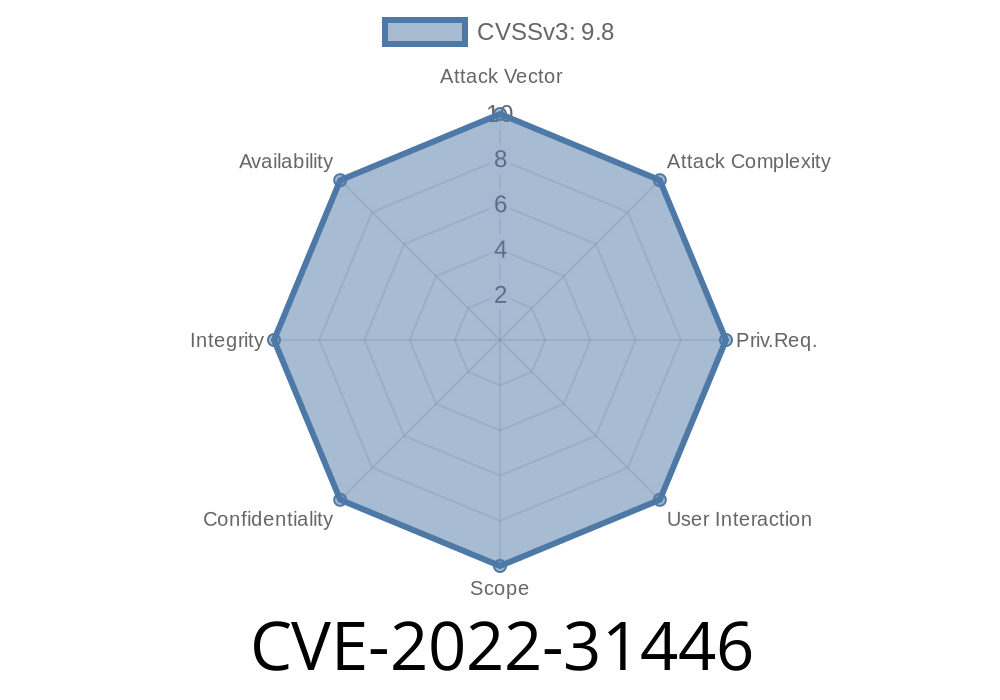
This issue could be exploited by an unauthenticated attacker to execute arbitrary code on the device. An attacker could exploit this vulnerability by enticing a user to click on a malicious link or email message in a social networking site or by convincing a user to open a malicious file sent via email. It is recommended that users update Tenda AC18 firmware to the latest version as soon as possible.
In addition to the Mac parameter, Tenda AC18 firmware also contains the following remote code execution vulnerabilities via HTTP. These issues could be exploited by an unauthenticated attacker to execute arbitrary code on the device. An attacker could exploit these issues by persuading a user to open a malicious file sent via email. It is recommended that users update Tenda AC18 firmware to the latest version as soon as possible.
1. Remote code execution vulnerability via HTTP at ip/goform/WriteFacHttp.
2. Remote code execution vulnerability via HTTP at ip/goform/WriteFacHttp.
3. Remote code execution vulnerability via HTTP at ip/goform/WriteFacHttp.
4. Remote code execution vulnerability via HTTP at ip/goform/WriteFacHttp.
Tenda AC8 Firmware Update
Tenda has released a firmware update for their AC18 line of units. This release fixes the following vulnerabilities: 1) Remote code execution vulnerability via HTTP at ip/goform/WriteFacHttp. 2) Remote code execution vulnerability via HTTP at ip/goform/WriteFacHttp. 3) Remote code execution vulnerability via HTTP at ip/goform/WriteFacHttp. 4) Remote code execution vulnerability via HTTP at ip/goform/WriteFacHttp
Timeline
Published on: 06/14/2022 03:15:00 UTC
Last modified on: 06/18/2022 03:18:00 UTC