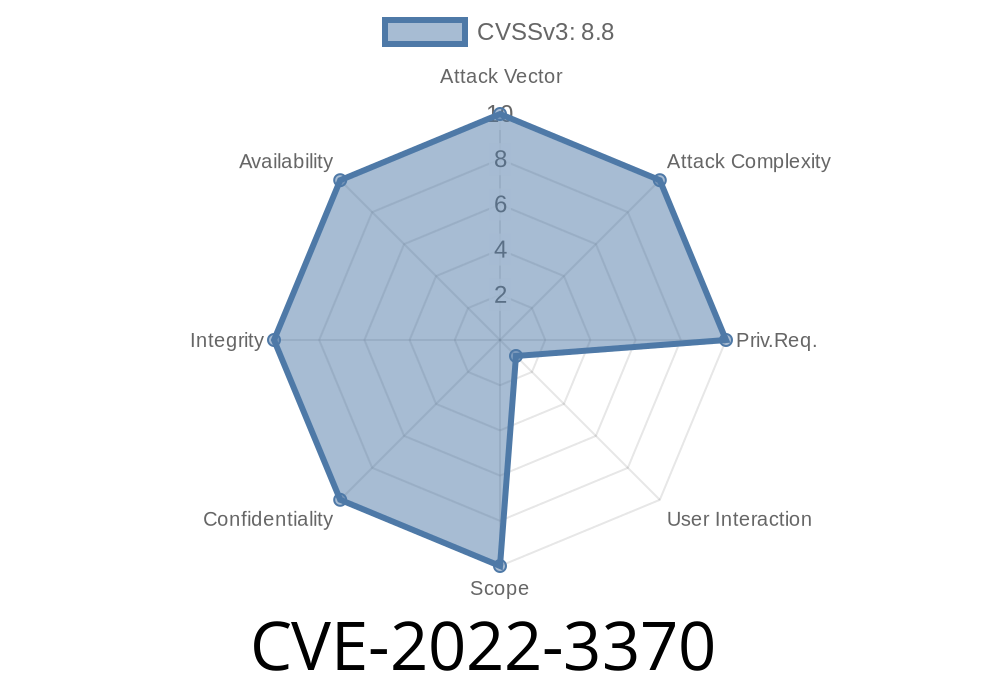
A recently disclosed vulnerability, CVE-2022-3370, has been identified within Google Chrome, with this high severity issue potentially allowing remote attackers to exploit heap corruption and gain control over their target's machine. This vulnerability can be found in Chrome versions prior to 106..5249.91 and involves the use of custom elements in the browser.
In this blog post, we will delve deeper into this security flaw, examine the relevant code snippets, and explore how attackers can exploit it to their advantage. Moreover, we will provide you with links for further references and resources to thoroughly understand the issue and how it can be fixed.
Background
CVE-2022-3370 is a high severity "use-after-free" vulnerability affecting Chrome's custom elements implementation, which may be exploited via a specifically designed HTML page. "Use-after-free" refers to the situation where a program continues to use memory after it has been freed, which can lead to unexpected behavior, crashes, or even execution of arbitrary code.
The official Chromium bug report can be found here: https://bugs.chromium.org/p/chromium/issues/detail?id=1301896
Code Analysis
Although the full details of CVE-2022-3370 have yet to be publicly disclosed in the Chromium project, we can still gather some basic understanding from the limited available resources. The vulnerability affects the part of the code that handles custom elements in Google Chrome, specifically regarding how they are created and destroyed.
Based on similar vulnerabilities reported in the past, we can speculate that the issue might be related to the misuse of pointers or references between elements or to an incorrect cleanup process after the destruction of an element. A typical example of a use-after-free scenario in C++ is as follows:
#include <iostream>
#include <memory>
class VulnerableClass {
public:
void print() { std::cout << "This is a vulnerable class" << std::endl; }
};
int main() {
std::unique_ptr<VulnerableClass> obj = std::make_unique<VulnerableClass>();
VulnerableClass* pointer_to_obj = obj.get();
obj.reset();
// Use-after-free
pointer_to_obj->print(); // This is undefined behavior!
}
In this example, the VulnerableClass object is created using a unique_ptr smart pointer, which is then reset, effectively freeing the associated memory. However, a raw pointer (pointer_to_obj) still holds the memory address, and attempting to access the memory through that pointer will result in undefined behavior, exemplifying a use-after-free vulnerability.
Exploit Details
Attackers could create a malicious HTML page with a specially crafted structure of elements that contain custom elements, manipulated in such a way that triggers the use-after-free vulnerability when rendered by a vulnerable version of the Chrome browser. When the targeted user visits the malicious HTML page, the attacker could execute arbitrary code and potentially compromise the user's machine.
Mitigations
Google has released an update for Chrome (version 106..5249.91), which contains a patch addressing the CVE-2022-3370 vulnerability. It is highly recommended to update to this version or later as soon as possible to protect against potential exploits. The official Chrome release blog post can be found here: https://chromereleases.googleblog.com/2023/02/stable-channel-update-for-desktop_28.html
Conclusion
CVE-2022-3370 is a critical use-after-free vulnerability in Google Chrome that potentially allows remote attackers to exploit heap corruption and compromise the targeted machine. It is essential to update Chrome to the latest patched version (106..5249.91) and be cautious when visiting untrusted websites.
Stay tuned for more details to emerge as this vulnerability is further analyzed and documented by the security community, and keep an eye on the Chromium project's issue tracker for updates on this and other related vulnerabilities.
Timeline
Published on: 11/01/2022 03:15:00 UTC
Last modified on: 12/03/2022 02:35:00 UTC