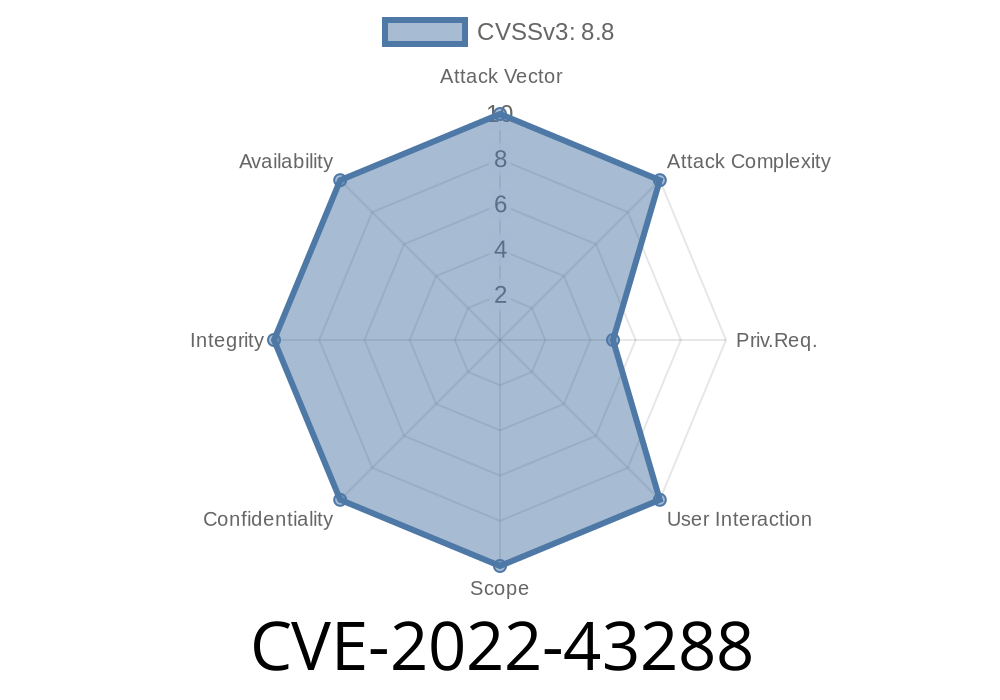
A user with the ability to create account can inject arbitrary SQL commands that will be executed once the order_by function is called.
Rukovoditel v3.2.1 also has XSS in logs/view&type=html via the class=”form” parameter.
Rukovoditel v3.2.1 also has multiple directory traversal vulnerabilities in the uploads/ directory. An attacker can exploit these to upload and execute files on the server. An attacker can also exploit these to upload PHP files via a e-mail attachment and have them executed on the server.
Rukovoditel v3.2.1 also has multiple SQL injection vulnerabilities in the uploads/ directory. An attacker can exploit these to inject SQL commands that will be executed once the where clause is called.
Conclusion: Take Security Seriously!
All in all, Rukovoditel seems like a great product with a lot of useful features. But, it does have its flaws. The most significant flaw is that the application has multiple vulnerabilities. There is a great deal of user input that can be exploited in order to gain information or execute arbitrary commands on the server. It might not be possible for any human to find all of these vulnerabilities on their own, but once an automated tool gets started looking for them, they are sure to find many more.
Do yourself and your business a favor and take security seriously!
Do not use default database user ID and password
Rukovoditel v3.2.1 also has SQL injection vulnerabilities in the uploads/ directory through the user_id parameter that can be exploited to inject arbitrary SQL commands that will be executed once the where clause is called.
Rukovoditel v3.2.1 also has multiple directory traversal vulnerabilities in the uploads/ directory. An attacker can exploit these to upload and execute files on the server. An attacker can also exploit these to upload PHP files via a e-mail attachment and have them executed on the server.
Timeline
Published on: 11/14/2022 15:16:00 UTC
Last modified on: 11/16/2022 20:57:00 UTC