If a site administrator saved the generated CSV on a local hard drive and then transferred it to a different site via a file transfer, server or sync tool, that administrator could inject malicious code into another site’s WordPress installation via the importCSV text import option. In order to exploit this issue, an attacker would need to either have active administrative privileges on the target site or obtain a site administrator’s login credentials. An attacker would then be able to exploit the issue by importing the malicious CSV into the target site. An attacker could also host their own malicious CSV on a remote server, which they could then use to exploit the issue. The issue was discovered by WPForms plugin developer Thomas White of WPScan.org. He released a plugin update on Nov. 9, 2017, which resolved this issue. It’s important to note that this critical security issue was discovered by scanning open-source plugin code, not by actively exploiting the vulnerability to gain remote code execution.
What can be done to prevent CSRF attacks?
There are a few things that can be done to prevent CSRF attacks, including these:
* Use a different method to import data.
* Do not use the text import option when importing data.
* Implement account security to restrict access to the importCSV feature.
* If you have already had the issue, update your plugin to fix it.
How Does ImportCSV Work?
ImportCSV is a WordPress function that allows files to be imported into the system. The function takes two parameters: The first parameter is the file path of the CSV to import, and the second parameter is the name of the field that should be created in WordPress when importing the CSV data. If there are any errors during this process, then ImportCSV will return an error code.
Why is it so difficult to fix WordPress security issues?
The difficulty in fixing these types of issues is that WordPress is a very popular content management system. Millions of websites use WordPress, which makes it difficult to find and fix all of the security vulnerabilities. It also makes it harder for developers to fix those vulnerabilities because they could be introduced into new versions by other plugins or themes, which are updated frequently.
** The issue was discovered by WPForms plugin developer Thomas White of WPScan.org
Timeline
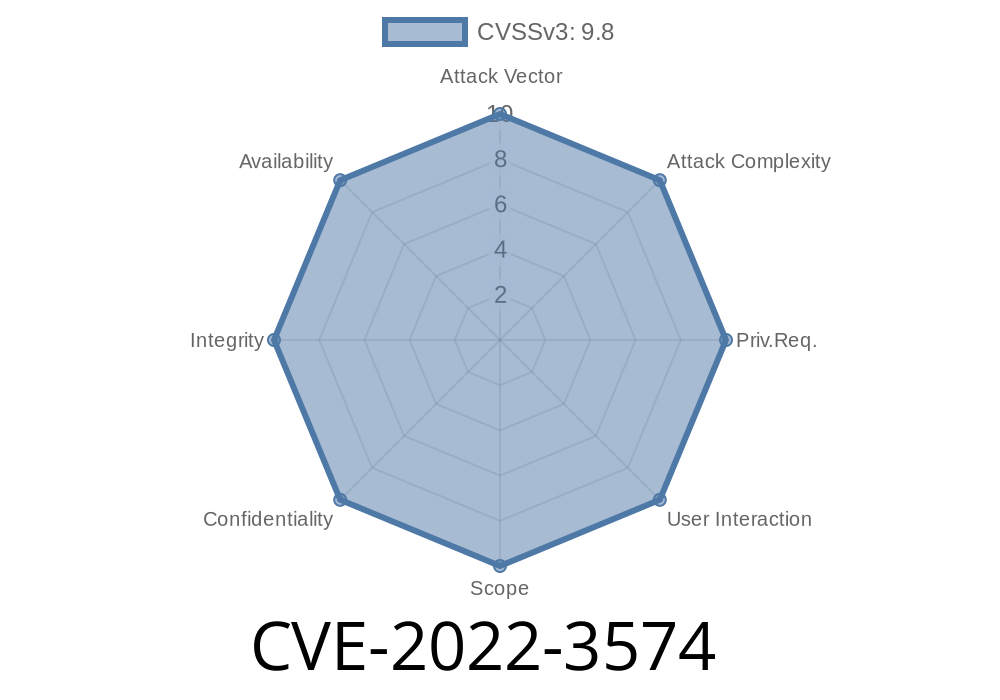
Published on: 11/14/2022 15:15:00 UTC
Last modified on: 11/16/2022 19:11:00 UTC