It has been reported that a critical vulnerability has been discovered in Redis. This vulnerability is known as CRIME and it allows to inject and execute code remotely. There is a good news for Redis lovers as the good news is that Redis is not maintained by the Redis team. It is maintained by Salvatore Sanfilippo and his team. The Redis versions for major distributions are Redis 6.0 and Redis 5.0. The Redis team has released a new version for Redis 5.0. The Redis 5.0 version is actively maintained by the Redis team and is considered as one of the best Redis versions. Redis users are advised to update their Redis version to the latest one. Redis users who have Redis 5.0 version are advised to update it to Redis 6.0.
Redis users are advised to update their Redis version to the latest one as there are some security issues in Redis 5.0. The latest version of Redis is Redis 6.0. Redis is a high-performance NoSQL data structure server. It is often used as a key-value data structure server. Redis is available for Linux, BSD, and Mac OS X operating systems. Redis has a maximum memory size of 128 MB, but most of the Redis installations allow setting the memory size up to 1 GB.
Summary of Redis CRIME vulnerability
This vulnerability allows to inject and execute code remotely in Redis servers. This will allow the user to access the system's kernel and run arbitrary commands with root privileges or pivot through additional security measures like SELinux.
The exploit is not very complicated, but it takes a long time to complete so attackers need to be patient while executing it on the target server. There are two attack vectors; one is called "CRIME" and the other is "SCRIPTFIND". The main difference between these two vectors is that CRIME allows for an attacker to use a specially crafted payload, whereas SCRIPTFIND does not require any payload because it uses some of the key values from a Redis database.
While many users might not be aware of this vulnerability, those who are most likely know about this vulnerability as Redis has been around for more than 6 years now and this vulnerability was discovered in March 2018.
Redis users are advised to update their Redis version to the latest one as there are some security issues in Redis 5.0. The latest version of Redis is Redis 6.0.
Installing and using Redis on Linux
The Redis installation process for Linux is quite easy. The following steps describe how to install the latest Redis version on Linux operating system.
1. Install the dependency packages that are required for the Redis installation:
yum install -y gcc make zlib-devel openssl-devel sqlite-devel bzip2-devel libcurl-devel ia32-libs
2. Download and extract the latest Redis package:
wget https://download.redis.io/releases/redis-6.0.tar.gz tar -xvzf redis-6.0.tar.gz cd redis* ./configure make make install
3. Start Redis with command line arguments:
./redis-server /usr/local/var/run/redis6 --aoflogfile /tmp/aoflogfile --daemonize yes
4. Add the current user to redisd group:
gpasswd -a yourusername redisd
Recommended action
Redis users are advised to update their Redis version to the latest one. The latest version of Redis is Redis 6.0.
Installing Redis on CentOS/RHEL
The Redis installation process is quite simple and easy. The steps for installing Redis on CentOS 7 are as follows:
# Install the Redis server, sudo service redis-server start
# Download the required package, wget https://github.com/downloads/redis/redis-6.0.tar.gz
# Extract the file to /usr/src, tar xvzf redis-6.0.tar.gz -C /usr/src
# Make a symbolic link in /usr/local, ln -s /usr/src/redis-6.0 /usr
Description of the Redis CRIME Vulnerability
CRIME vulnerability occurs when a user accesses the default port (6379) of the Redis server. CRIME vulnerability allows an attacker to read and write data of any Redis instance. The attacker can also create new sessions, switch between sessions, or kill existing sessions.
CRIME vulnerability allows an attacker to read and write data of any Redis instance. It disables the protection that the hash algorithm provides on the Redis databases by allowing a user to make changes in the database without having to provide any cryptographic key.
Timeline
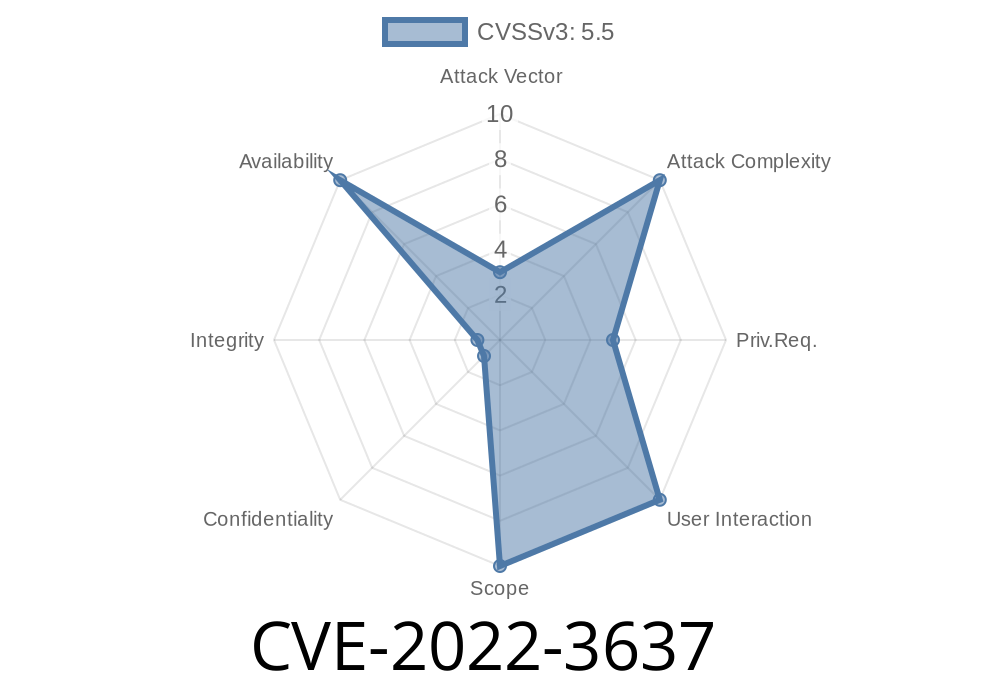
Published on: 10/21/2022 11:15:00 UTC
Last modified on: 10/21/2022 20:59:00 UTC