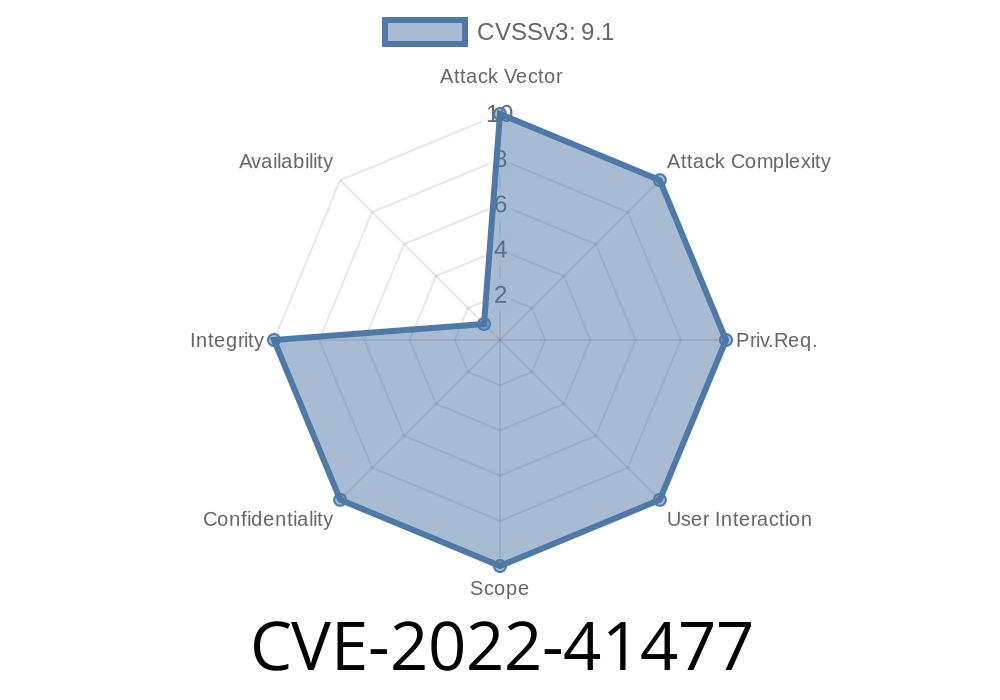
This issue is rated as critical due to the fact that server-side requests can be exploited to completely bypass authentication and obtain unauthorized access to the server’s file system, resulting in potential data breaches. We recommend upgrading to the latest version of WeBid as soon as possible. If you’re using version 1.2.2 or earlier, you should consider blocking access to the admin/theme.php file by inputting “Deny” into the “For” field of your server’s security configuration, for example: “Forbidden /wp-admin/admin-ajax.php”. For more information, please reference the upgrade instructions We have released a patch for WeBid 1.2.3 which addresses this issue. We recommend all users update to this latest version as soon as possible. If you’re using WeBid 1.2.2 or earlier, you should consider blocking access to the admin/theme.php file by inputting “Deny” into the “For” field of your server’s security configuration, for example: “Forbidden /wp-admin/admin-ajax.php”. For more information, please reference the upgrade instructions here
WeBid Vulnerability Summary
The latest version of WeBid is not vulnerable to CVE-2022-41477. You can upgrade to the latest version at your earliest convenience. If you’re using version 1.2.2 or earlier, you should consider blocking access to the admin/theme.php file by inputting “Deny” into the “For” field of your server’s security configuration, for example: “Forbidden /wp-admin/admin-ajax.php”. For more information, please reference the upgrade instructions here .
Description of the Issue
In WeBid 1.2.3, a critical vulnerability was discovered which allows server-side requests to be exploited to obtain unauthorized access to the server’s file system, resulting in potential data breaches.
Timeline
Published on: 10/14/2022 19:15:00 UTC
Last modified on: 10/20/2022 14:01:00 UTC