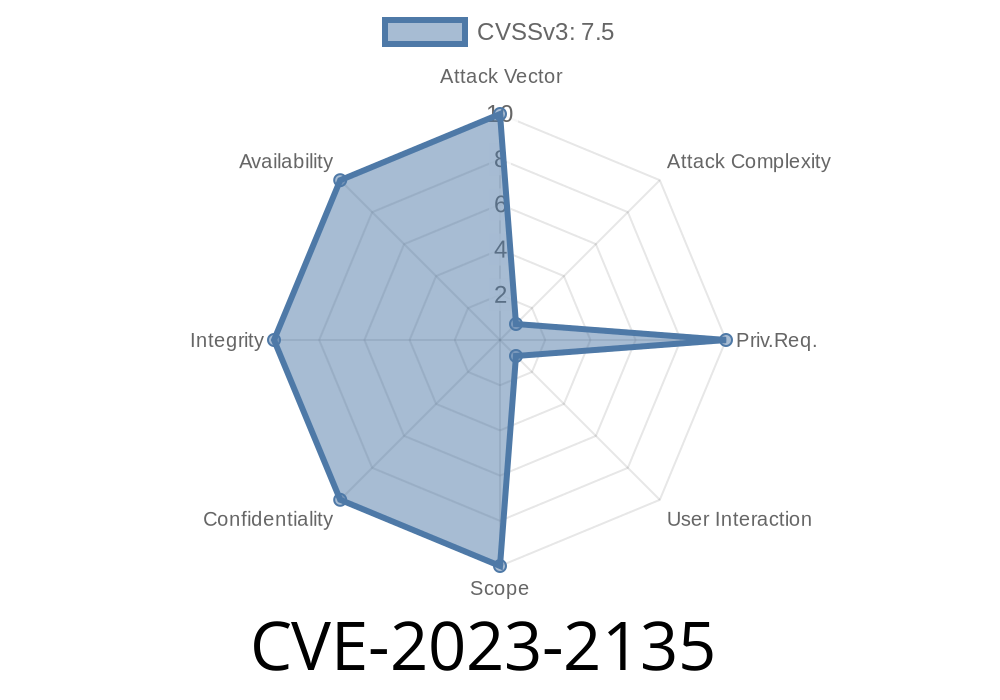
In April 2023, security researchers uncovered a high-severity vulnerability in Google Chrome's DevTools, tracked as CVE-2023-2135. This flaw is a classic use-after-free vulnerability, which—if exploited—could allow a remote attacker to corrupt the heap and potentially execute arbitrary code on a victim’s machine. This post provides a simplified explanation, showcases a code snippet example, and walks you through how such an exploit could be constructed. We also share links to original sources and practical advice for both users and developers.
Impact: Remote attacker can exploit heap memory corruption, leading to code execution.
- Precondition: Victim must perform certain actions, often enabling specific DevTools features or being lured into opening a crafted page while DevTools is active.
Technical Overview
A use-after-free (UAF) occurs when a program continues to use a pointer after the memory it references has been freed. In Chrome, some objects used by DevTools were not properly released or handled, opening the doors for potential exploits when users interacted with malicious web pages.
Let’s break it down
- Attacker’s Goal: Trick the victim into opening Developer Tools and then viewing a specially-crafted HTML file.
- Result: If successful, the attacker can control some part of Chrome’s memory, possibly leading to code execution.
How Does the Exploit Work?
Imagine you open DevTools on a trusted website. Now, by social engineering, an attacker convinces you to visit a malicious page without closing DevTools. The malicious page takes advantage of the flaw, potentially triggering a use-after-free condition.
The victim opens DevTools and then visits (or is redirected to) the malicious page.
3. The malware triggers the UAF by causing Chrome to free a specific object, then forces Chrome to use that freed memory slot, potentially running attacker code.
Example Code Snippet
While Google has patched this bug, a simplified proof-of-concept might look like this pseudocode, demonstrating the logic behind the UAF:
<!-- EXAMPLE: Highly Simplified UAF Trigger -->
<html>
<body>
<script>
// Step 1: Open DevTools (user action)
// Step 2: Trigger buggy DevTools code path via automation
function triggerUAF() {
// Allocate memory/resources in the DevTools context
let obj = new DevToolsResource();
// Free the object (simulate a bug)
obj.free();
// The use-after-free: Access the object again after free
// If vulnerable, Chrome could crash or execute arbitrary code
obj.doSomethingDangerous();
}
// Delay until user opens DevTools, or use a timing attack
setTimeout(triggerUAF, 300);
</script>
</body>
</html>
Note: The actual exploit is much more complex, involving JavaScript and browser internals, but this illustrates the core bug logic: use of an object after it’s freed.
Real Exploit Flow
1. Prerequisites: Attacker must convince the user to open DevTools (e.g., for "debugging" or "cheating" in a game).
Attack: Malicious page triggers the UAF in DevTools via a crafted event sequence.
4. Result: Attacker may inject or run arbitrary code in the Chrome process (browser sandbox applies).
NOTE: Browsers constantly sandbox and update security models, making real-world exploitation challenging but still possible in outdated or unpatched environments.
Responsible Disclosure and Patch
The Chromium team patched this issue in version 112..5615.137. If you're running an older Chrome version, you should update immediately.
- Patch commit: chromium.googlesource.com - Issue 1420371
- Official Advisory: Chromium Security Release Notes
- Common Vulnerabilities and Exposures (CVE) Record: CVE-2023-2135 at NIST
Cross-Platform: Affects Windows, Mac, and Linux Chrome installations.
- High Impact: Even though DevTools must be open, many power-users keep DevTools active all the time.
Conclusion
CVE-2023-2135 is a serious security issue, especially for those who frequently use Chrome DevTools. If you’re a developer, Chrome extension writer, or a curious user, be vigilant and ensure you’re always running the latest browser update. While this use-after-free was quickly patched, it serves as a reminder that browser internals can expose powerful attack vectors when not properly safeguarded.
References and Further Reading
- CVE detail: NIST - CVE-2023-2135
- Chrome Releases: Stable Channel Update for Desktop
- Chromium Issue Tracker: Issue 1420371
- Chromium Patch Commit
*Stay safe, code wisely, and always keep your browser updated!*
Timeline
Published on: 04/19/2023 04:15:00 UTC
Last modified on: 05/02/2023 03:15:00 UTC