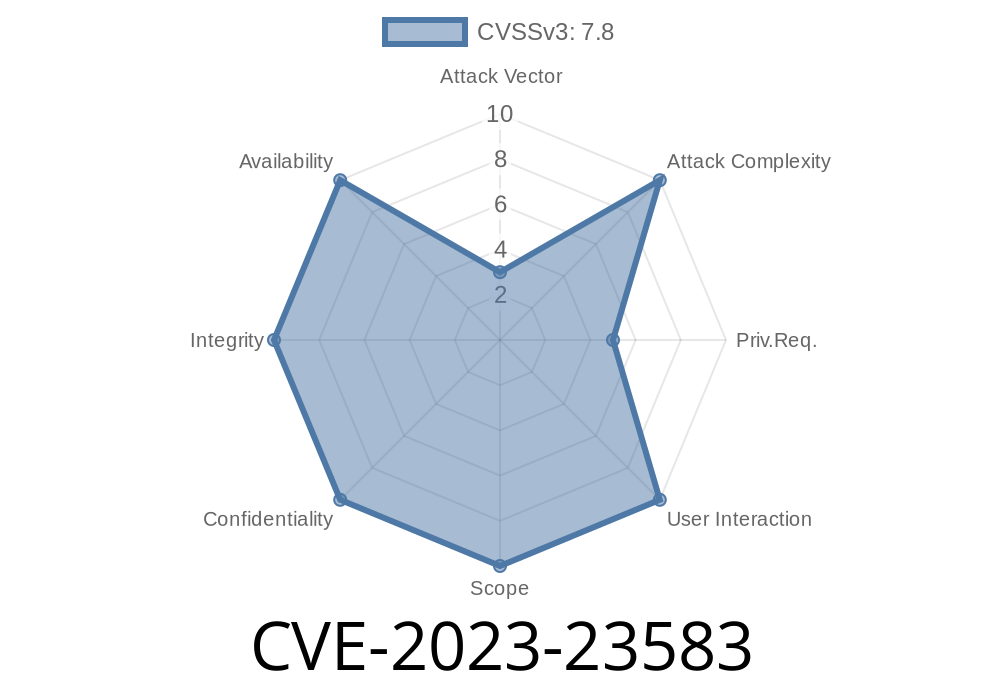
CVE-2023-23583 is a fascinating — and dangerous — vulnerability that affects certain Intel® Processors. It lets a local, authenticated user exploit a weird sequence of instructions to behave unexpectedly, potentially leading to privilege escalation, information leaks, or even crashing the whole system. In this article, we’ll break down how this vulnerability works, its impact, and walk through a simple proof-of-concept. We’ll also link you to original references and official advisories, so you get all the details in one place.
What Is CVE-2023-23583?
At the heart of CVE-2023-23583 is a bug in how affected Intel processors handle some sequences of machine instructions. When a user with local access carefully arranges instructions (think tiny coded “tricks”), the processor can misinterpret its work and allow unauthorized access or leak sensitive data.
Attack Vector: Local (you need to run code on the machine)
For the official writeup, see:
🔗 Intel Security Advisory INTEL-SA-00828
🔗 National Vulnerability Database: CVE-2023-23583
Why Is This a Problem?
Normally, operating systems and CPUs enforce strong boundaries. If you’re just a regular user, you’re not supposed to see system secrets or mess with other people’s processes. This vulnerability lets someone break those rules by abusing the order in which the CPU executes instructions. The most worrying impacts are:
How Does the Exploit Work?
Intel’s advisory doesn’t go deep into the technical details (to avoid helping attackers), but the basic exploitation involves:
Running a special program with user rights on the affected computer.
2. Issuing a crafted sequence of low-level instructions — in assembly language — that trigger the vulnerability.
3. The processor, following this sequence, either leaks information (reading restricted memory), escalates privileges, or causes a crash.
In practical terms, a local attacker (someone with shell access, a malicious program, or a compromised account) runs a custom binary that plays “CPU tricks.”
Proof-of-Concept Code (Educational Only!)
Here’s a simplified pseudo-code snippet to show the idea. This won’t work on its own or exploit the bug directly (for safety), but it shows the kind of code involved.
// WARNING: EDUCATIONAL PURPOSES ONLY
// Requires local access; make sure you have permission
#include <stdio.h>
#include <immintrin.h> // Intel Intrinsics
int main() {
volatile int secret = xDEADBEEF; // protected data
volatile int dummy = ;
// Suspicious instruction sequence. In reality,
// this sequence is more complex and processor-dependent.
// Example: Faulty interaction between MOV, PREFETCH, and speculative execution.
// Prefetch data (may cause side-effects in CPU cache)
_mm_prefetch((const char*)&secret, _MM_HINT_T);
// Dummy computations to set up state
for (int i = ; i < 100; i++) {
dummy += i;
}
// Speculative read: Under certain circumstances,
// the CPU might speculatively execute the next instruction
// and allow reading the value of 'secret'
int leaked = secret;
printf("Leaked value: x%X\n", leaked);
return ;
}
Note: Real exploits rely on precise timing and processor behaviors. In practice, exploit code would use “side channel” attacks (like Meltdown or Spectre variants) to extract the secret value.
Update Your System: Intel has firmware patches and microcode updates.
- Apply OS Security Updates: Microsoft, Linux Distributions, and Apple may provide specific patches.
- Restrict Local Access: Only trusted users/programs should run on sensitive machines.
References and Further Reading
- 🔗 Intel SA-00828 Security Advisory
- 🔗 CVE-2023-23583 on NVD
- 🔗 Red Hat Summary
- 🔗 CERT/CC Notes
Final Thoughts
CVE-2023-23583 reminds us that even the tiniest missteps in processor design can have big consequences. If you haven’t updated your systems, now is the time! The exploit isn’t trivial, but once a proof-of-concept gets out, attackers will move quickly.
Stay patched, stay vigilant!
If you want to dig deeper, or are unsure if your hardware is affected, check Intel’s advisory and your operating system vendor’s security page for specific steps.
*This post was written exclusively for educational and awareness purposes. Do not attempt unauthorized exploitation on systems you do not own or manage.*
Timeline
Published on: 11/14/2023 19:15:18 UTC
Last modified on: 12/16/2023 20:15:44 UTC