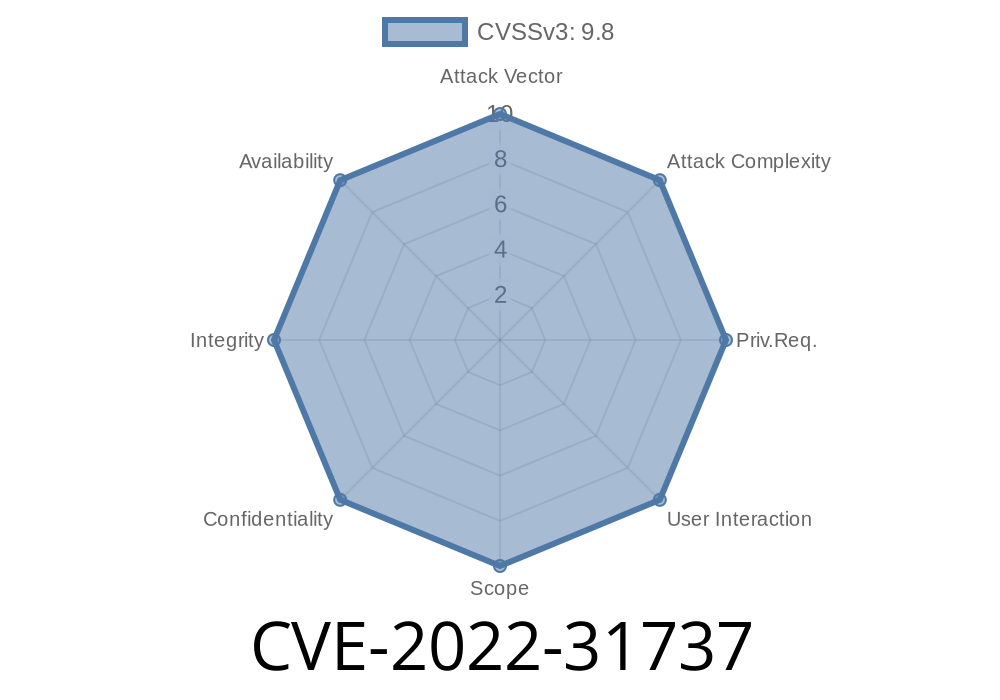
CVE-2022-31737 An attacker wrote code outside of WebGL memory, which could lead to memory corruption and a crash.
A malicious website could cause a user to inadvertently click a malicous link, leading to code execution. This vulnerability affects Thunderbird 91.10, Firefox 101,
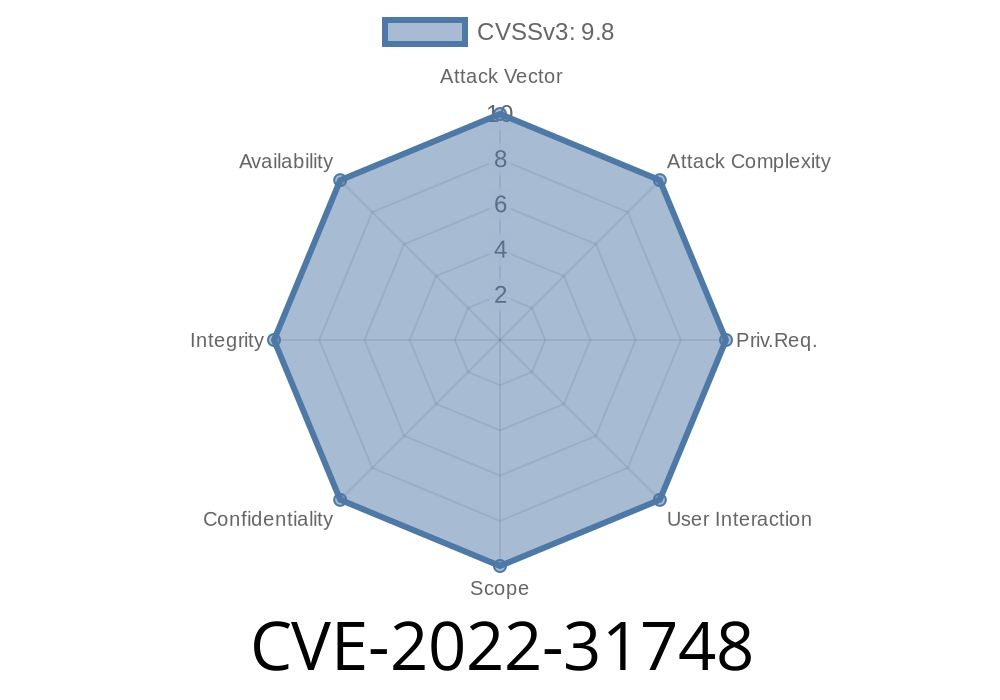
CVE-2022-31748 Gabriele Svelto, Timothy Nikkel, Randell Jesup, and the Mozilla Fuzzing Team found memory safety bugs in Firefox 100.
It is likely that some of these issues were discovered by automated tools. For example, it is possible to use the Google fuzzing framework to
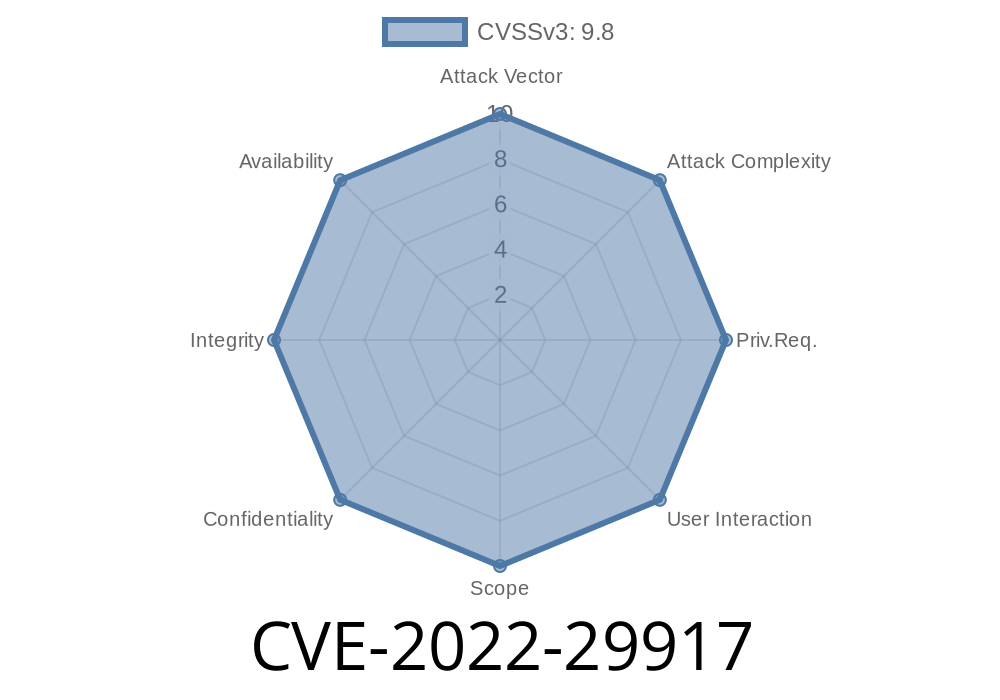
CVE-2022-29917 Mozilla developers found memory safety bugs in Firefox 99 and Firefox ESR 91.8.
This issue was fixed in Thunderbird 24.3.0.1, ESR 24.3.0.1, and Firefox 27.0.1. If you are running any
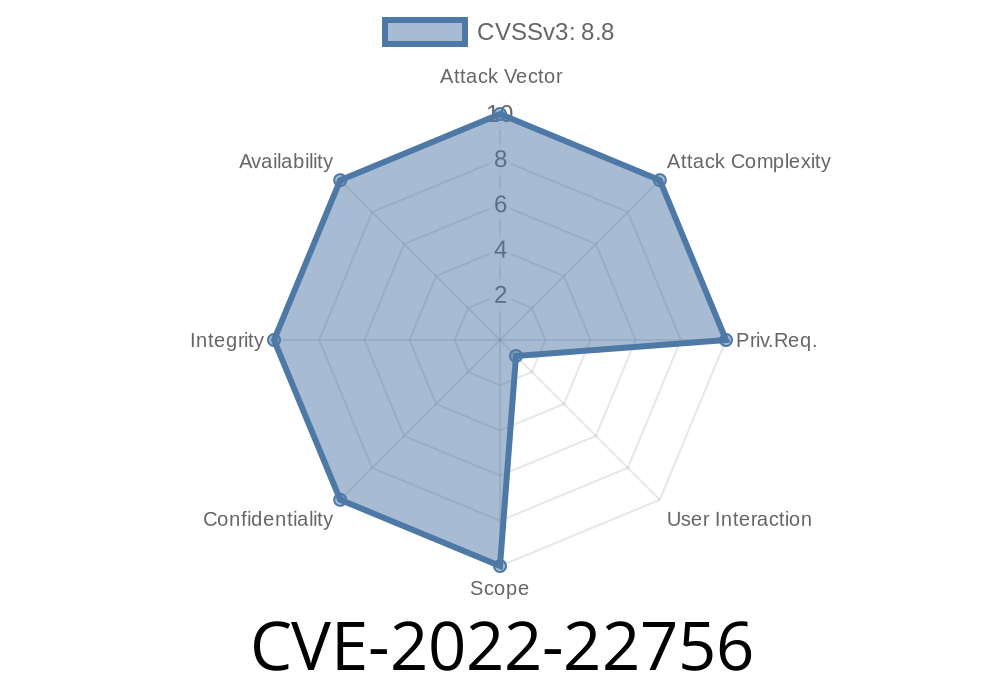
CVE-2022-22756 Drag and drop of an image could lead to file being changed to run arbitrary code after user clicks.
Mozilla was aware of the issue since late 2015 and issued an advisory with the details. However, the browser’s default setting did not prompt
CVE-2022-22743 An attacker-controlled tab could make the browser unable to leave fullscreen mode.
Firefox users that are relying on Google Chrome or Microsoft Edge to view sites that have been changed to require full-screen mode are advised to
Episode
00:00:00
00:00:00