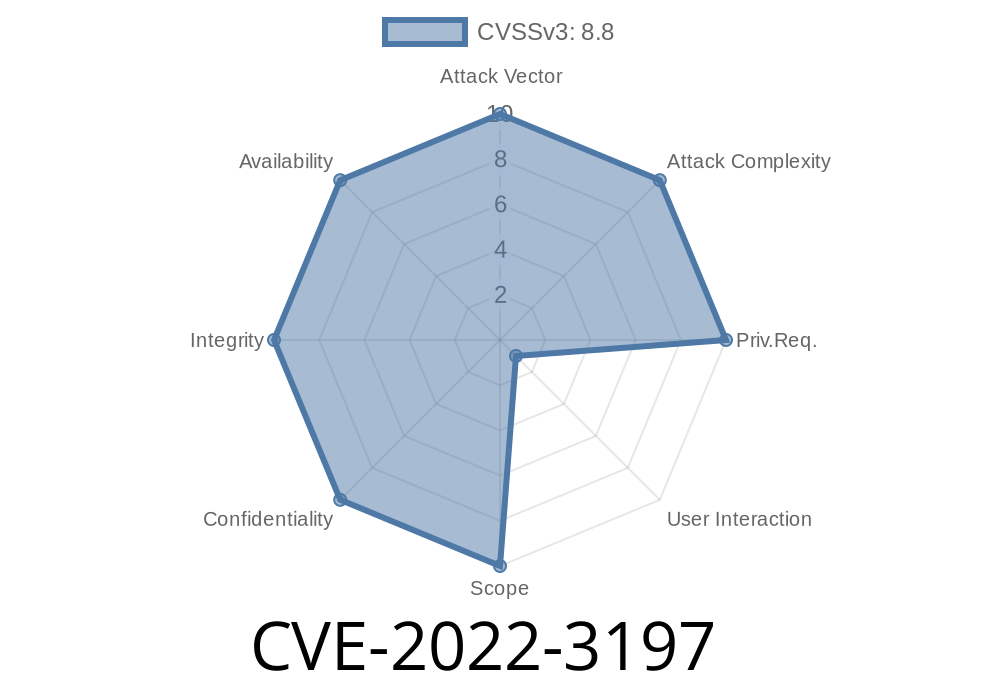
CVE-2022-3197 An after free vulnerability in Google Chrome could be exploited to cause heap corruption.
CVE-2018-6050 was assigned this issue. As of writing this advisory, it is still unclear whether this issue can be exploited to achieve remote code execution.
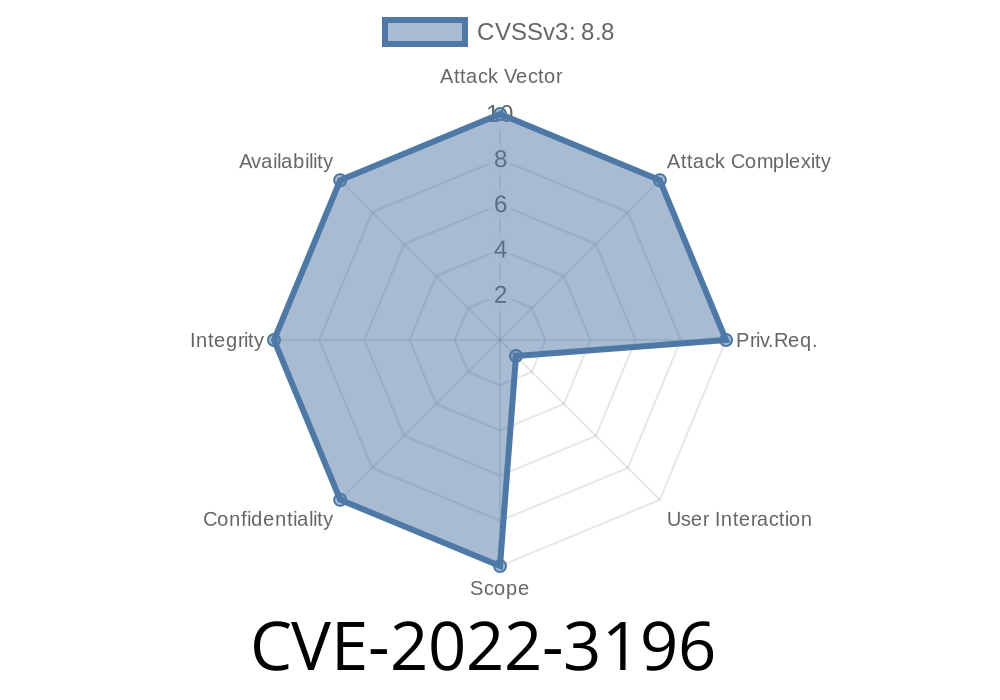
CVE-2022-3196 An after free vulnerability in Google Chrome could be exploited to cause heap corruption.
CVE-2018-6050 was assigned this issue. As of writing this advisory, it is still unclear whether this issue can be exploited to achieve remote code execution.
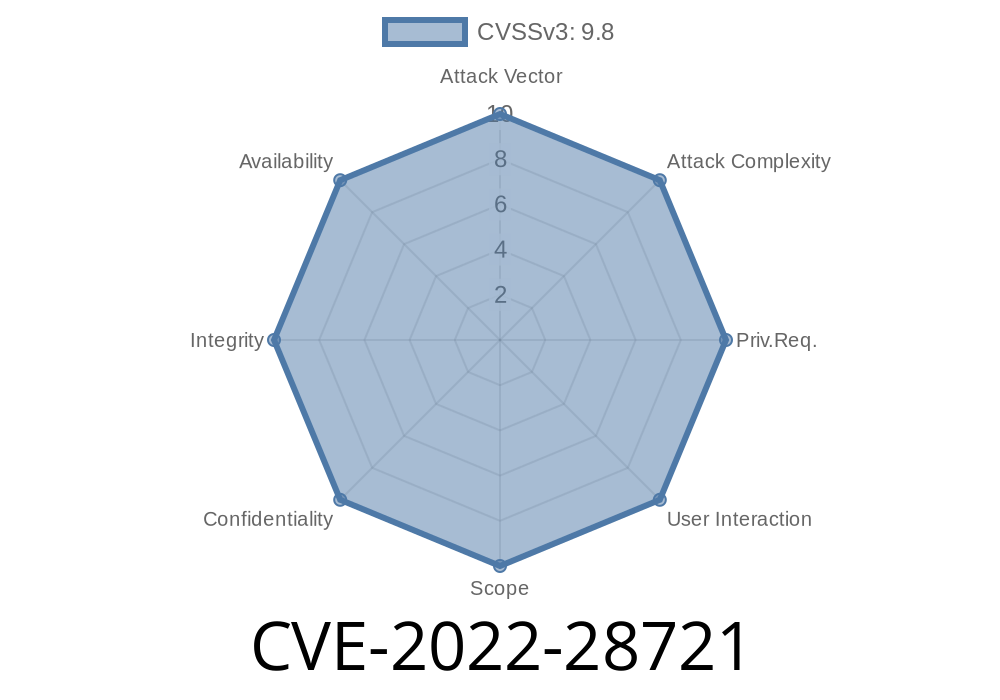
CVE-2022-28721 Certain HP Print Products are potentially vulnerable to Remote Code Execution.
This occurs when a hacker gains access to a computer through a vulnerable software application and then uses that access to run malicious code on
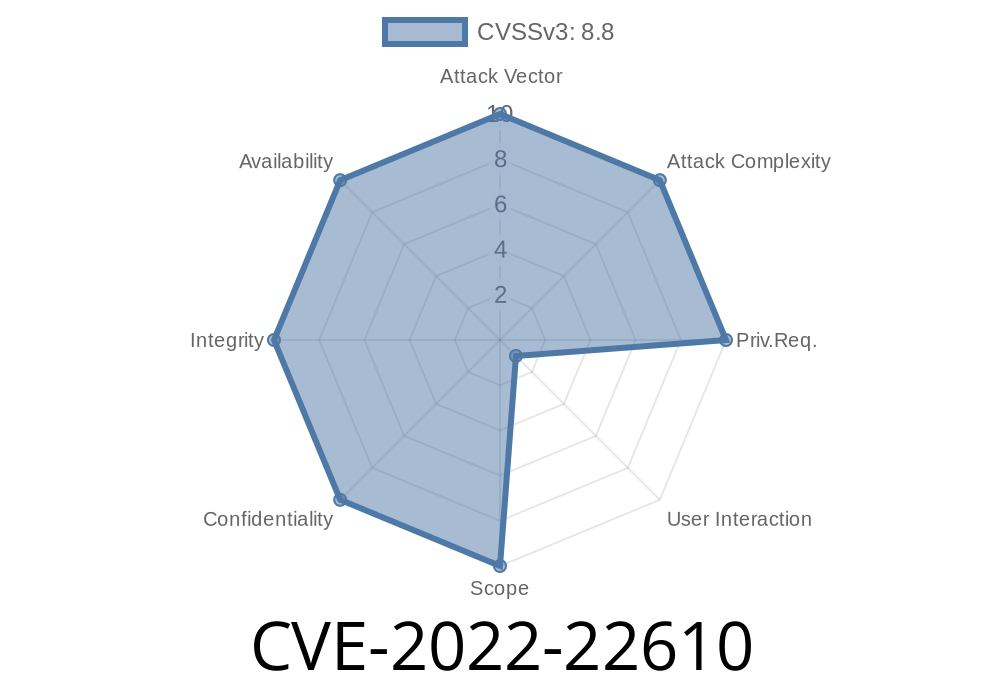
CVE-2022-22610 - How a Memory Corruption Bug in WebKit Put Apple Users at Risk
CVE-2022-22610 might not sound like a major headline, but for millions of Apple users, this security flaw had the potential to become a digital disaster.
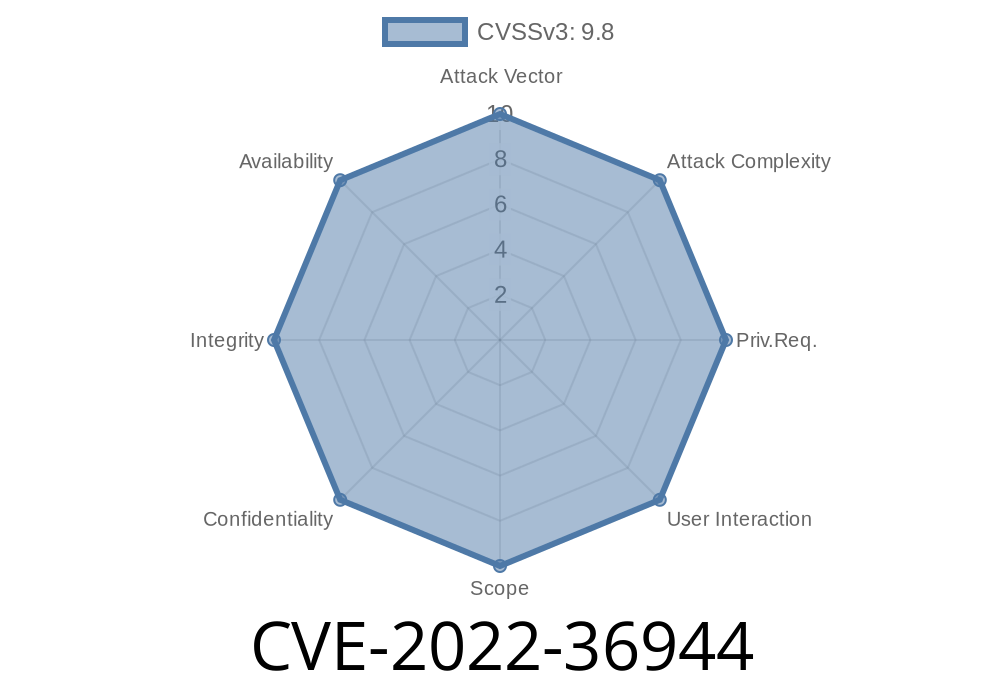
CVE-2022-36944 Scala 2.13.x has a Java deserialization chain in its JAR file. This risk is only present when LazyList deserialization is present in an application.
This issue was fixed in 2.13.10 release. This issue was discovered by Sergey Kovalev from VSEPR team in Google.
JAR files are widely
Episode
00:00:00
00:00:00