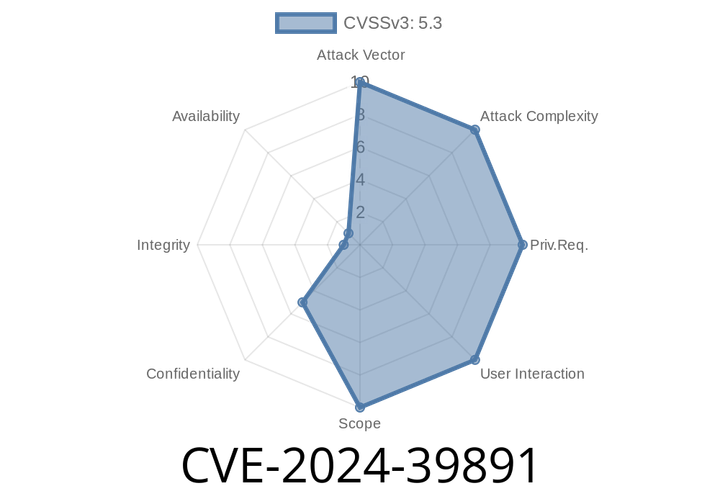
CVE-2024-39891 - Exposed Authy Phone Number Lookup — How Twilio’s API Leaked User Data
In June 2024, security researchers spotted a worrying flaw in the Twilio Authy API—used by millions for secure two-factor authentication. This vulnerability, logged as
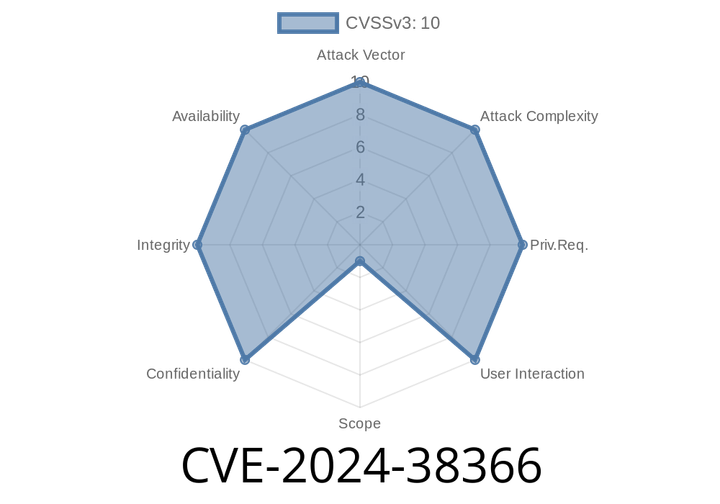
CVE-2024-38366 - Remote Code Execution Vulnerability in trunk.cocoapods.org via MX Lookup
A critical vulnerability (CVE-2024-38366) in the trunk.cocoapods.org, the authentication server behind the CocoaPods package manager, exposed the entire infrastructure to Remote Code Execution
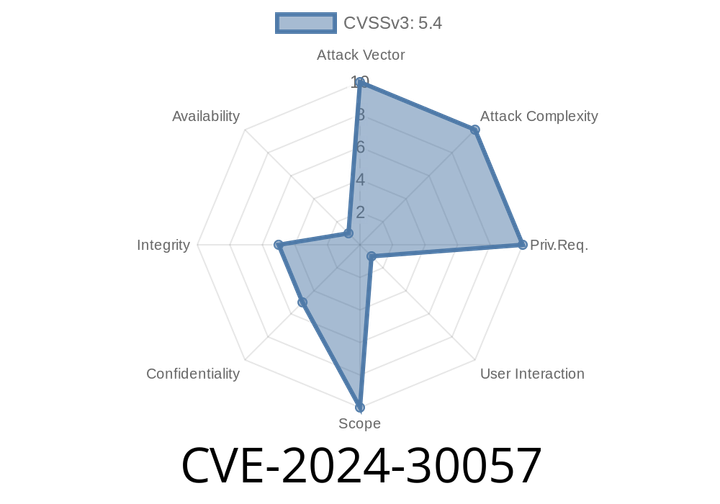
CVE-2024-30057 - Microsoft Edge for iOS Spoofing Vulnerability Explained
On June 2024, a new vulnerability was disclosed in Microsoft Edge for iOS — tracked as CVE-2024-30057. While Edge is known for its security features, this
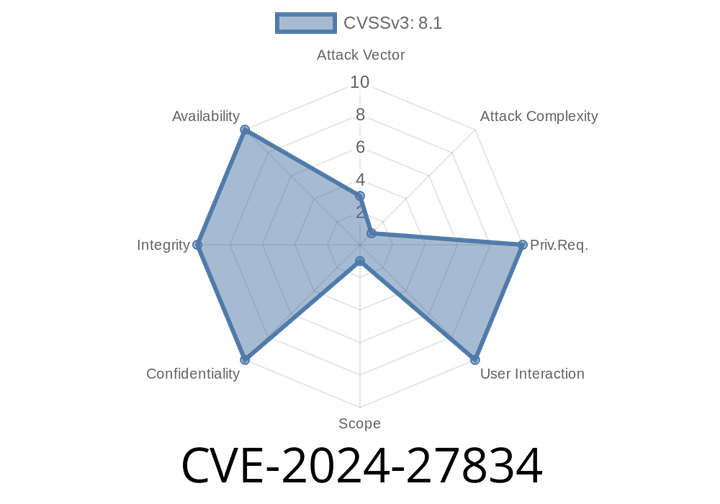
CVE-2024-27834 - Understanding and Exploiting the Apple Pointer Authentication Bypass
Apple security vulnerabilities don’t make big headlines every day. But when one lets attackers bypass memory protections put in place to stop hacking at
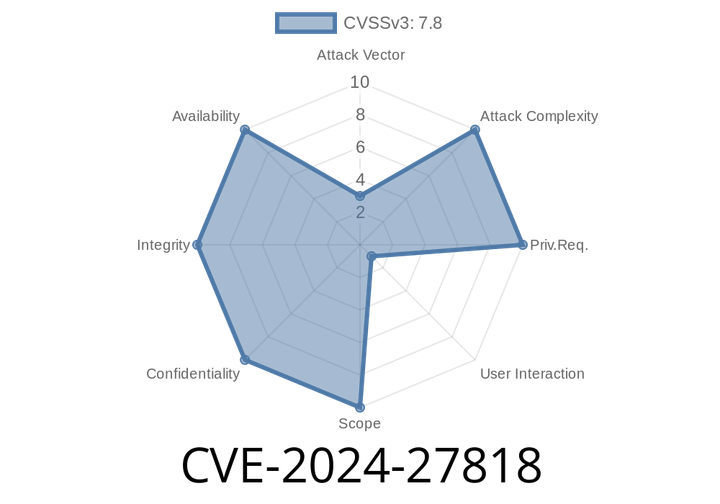
CVE-2024-27818 - Apple’s Memory Handling Bug That Led to Code Execution on iOS, iPadOS, and macOS
CVE-2024-27818 is a memory handling vulnerability that could let attackers crash apps or even run their own code on iPhones, iPads, and Macs. Fixed in
Episode
00:00:00
00:00:00