CVE-2025-43515 - Unauthenticated Remote Code Execution Vulnerability in Apple Compressor (What Happened, How It Works, and How to Protect Your Mac)
---
Apple Compressor is a popular professional tool for encoding video and audio media. But like any complex software, sometimes critical bugs sneak through. In
CVE-2025-55177 - How WhatsApp’s Device Sync Flaw Exposed iOS and Mac Users to Remote Attacks
In June 2025, security researchers and WhatsApp themselves revealed a significant flaw affecting WhatsApp for iOS, WhatsApp Business for iOS, and WhatsApp for Mac. Tracked
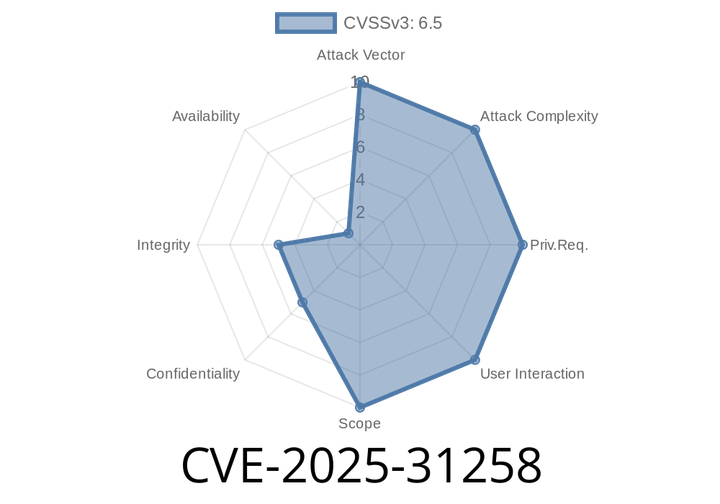
CVE-2025-31258 - How a macOS Sandbox Escape Was Fixed in Sequoia 15.5
In early 2025, Apple patched a serious security vulnerability impacting the macOS operating system. Tracked as CVE-2025-31258, this bug could have allowed a malicious app
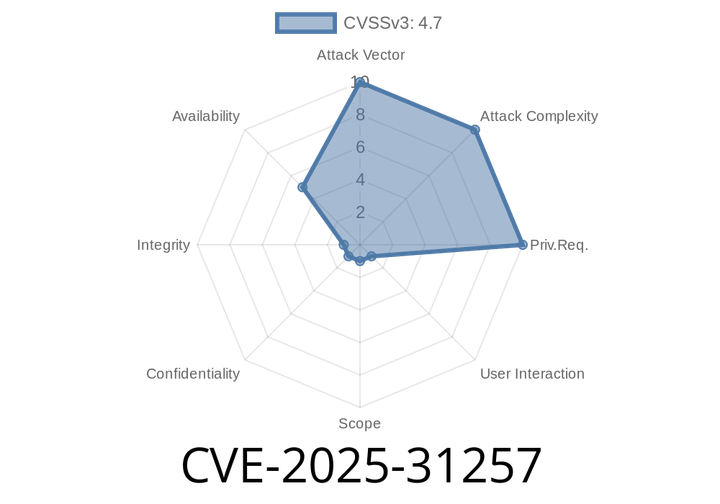
CVE-2025-31257 - Critical Safari Crash Bug Explained, Code Samples, Exploitation, and Fixes
CVE-2025-31257 is a recently disclosed security vulnerability affecting Apple's web browser, Safari, on multiple Apple platforms—iPhone, iPad, Mac, Apple TV, Apple Watch,
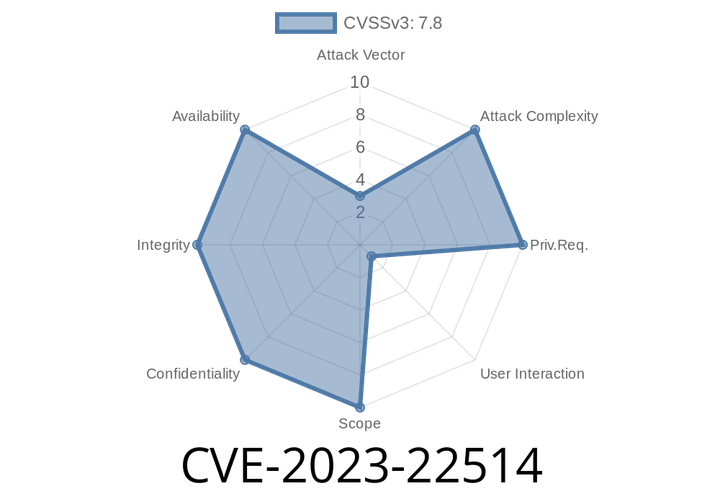
CVE-2023-22514 - A Deep Dive into the Remote Code Execution Vulnerability in Sourcetree
CVE-2023-22514 is a remote code execution (RCE) vulnerability rated as “High” severity, discovered in Sourcetree—the popular Git and Mercurial client for Mac and Windows,
Episode
00:00:00
00:00:00