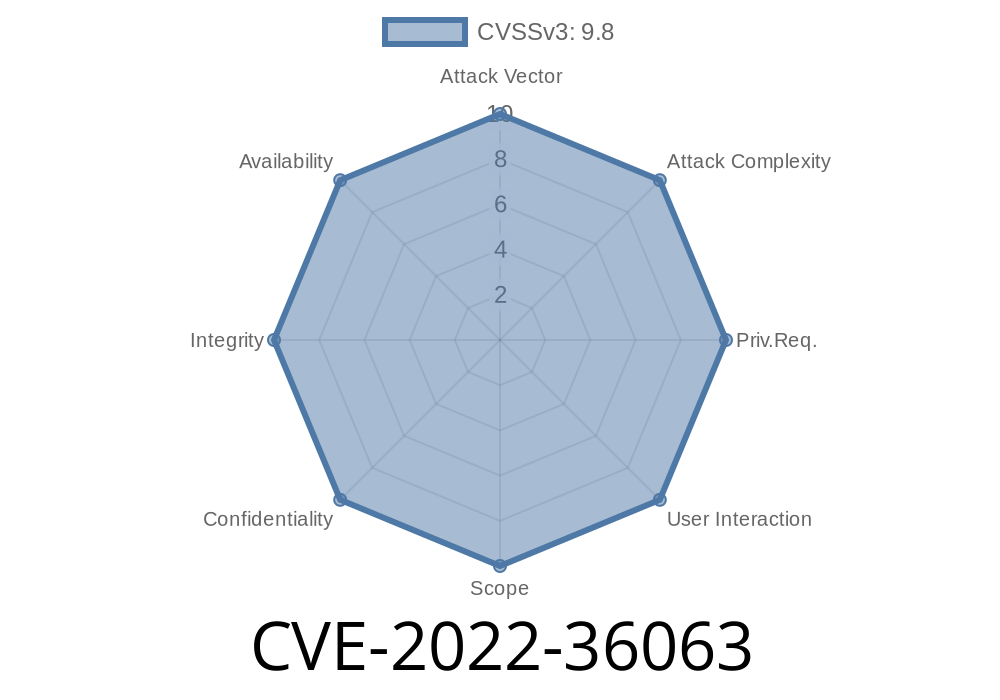
CVE-2022-36063 Azure RTOS USBx is a USB host, device and OTG embedded stack with Azure RTOS ThreadX support.
Azure RTOS USBx implementation of host support for uploading and downloading files including code and data, via FTDI and UART, may be potentially exploited to
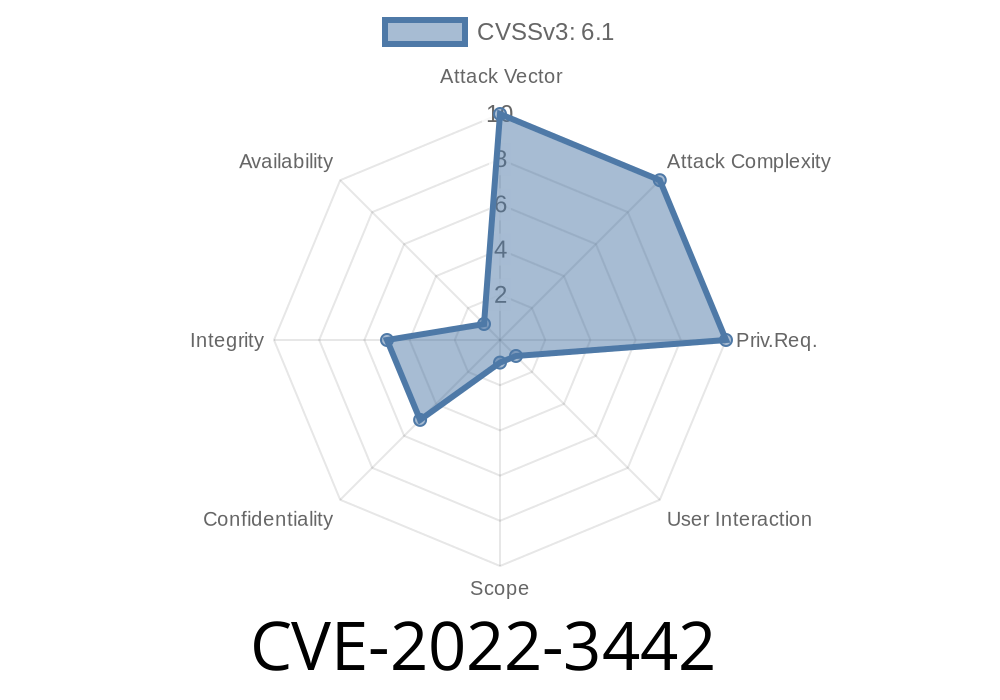
CVE-2022-3442 Crealogix EBICS 7.0 has a vulnerability that leads to cross site scripting.
It is worth noting that this issue was discovered by security researchers of TippingPoint. It has been classified as critical. The discovery was made public.
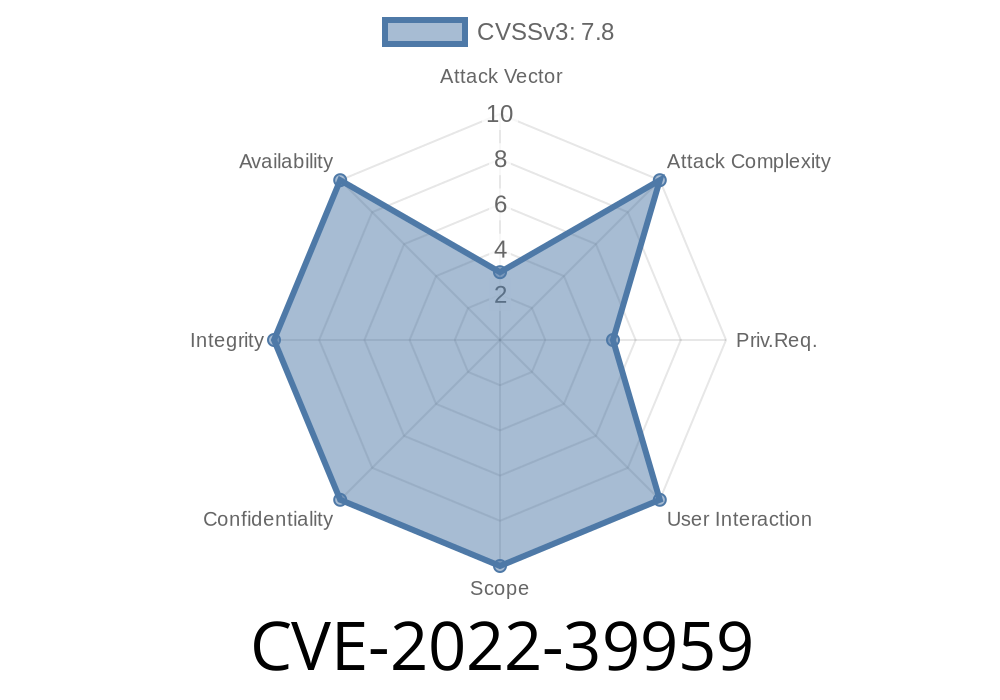
CVE-2022-39959 An unprivileged user can create a file named Everest.exe in the Programdata\Panini folder.
This issue was reported by the researcher Mohamed Diaby from Cybersecurity for the Masses. In order to exploit the issue, a user must be tricked
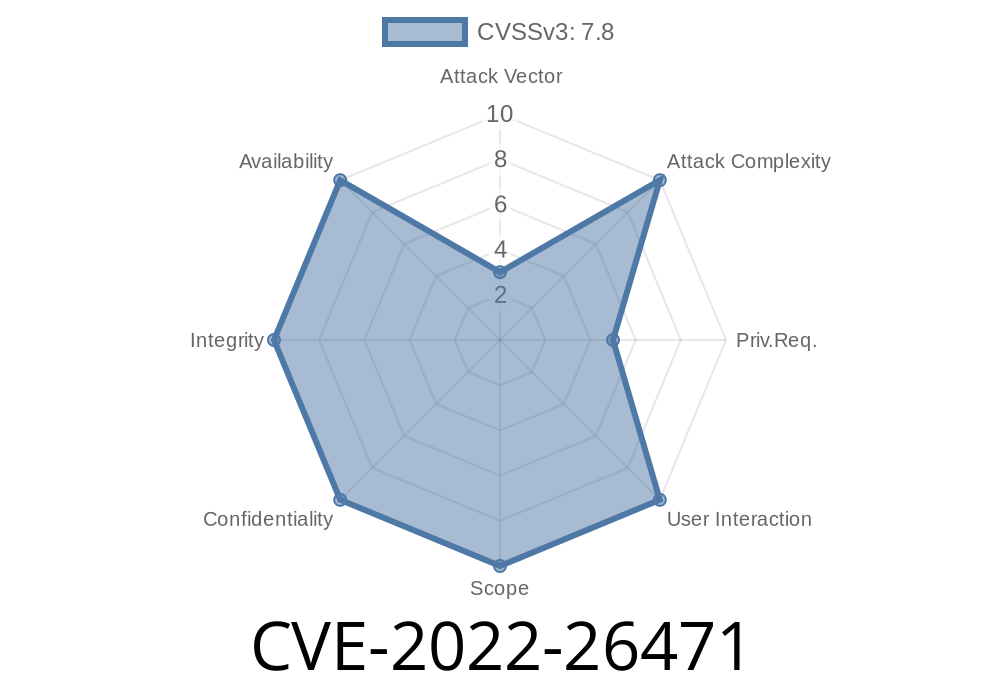
CVE-2022-26471 In telephony, a parcel format mismatch could lead to privilege escalation with no user interaction needed.
In some circumstances, there is a possible local escalation of privilege with no additional privileges needed. This could occur when a local application is running
CVE-2022-32593 In Vowe, there is a possible out of bounds write, which could lead to local escalation of privilege with System execution privileges. User interaction is not needed for exploitation.
An attacker could launch a Red Team engagement and leverage this vulnerability. The attacker could convince a system administrator to open a malicious email attachment
Episode
00:00:00
00:00:00