CVE-2022-35805 - Breaking Down the Microsoft Dynamics CRM Remote Code Execution Flaw
---
In the world of business software, Microsoft Dynamics CRM (on-premises) powers customer relations for thousands of organizations. But in 2022, a major security risk
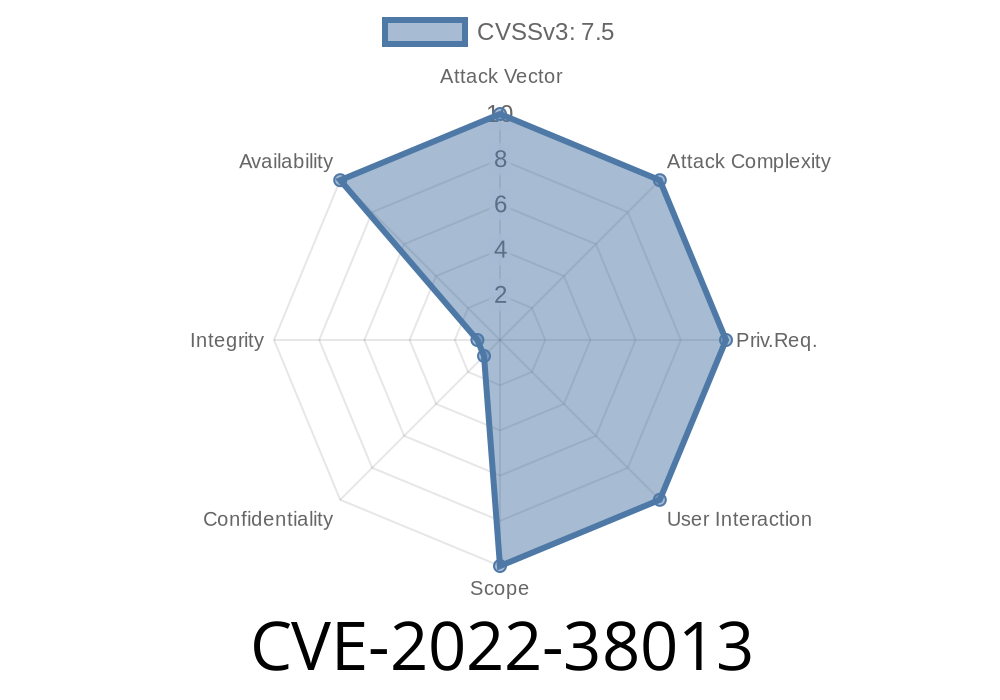
CVE-2022-38013 .NET Core and Visual Studio Denial of Service Vulnerability.
This vulnerability has been discovered by the security researcher Daniel Genkin (via Twitter). The vulnerability is located in the OpenId sign-in authentication provider. OpenId is
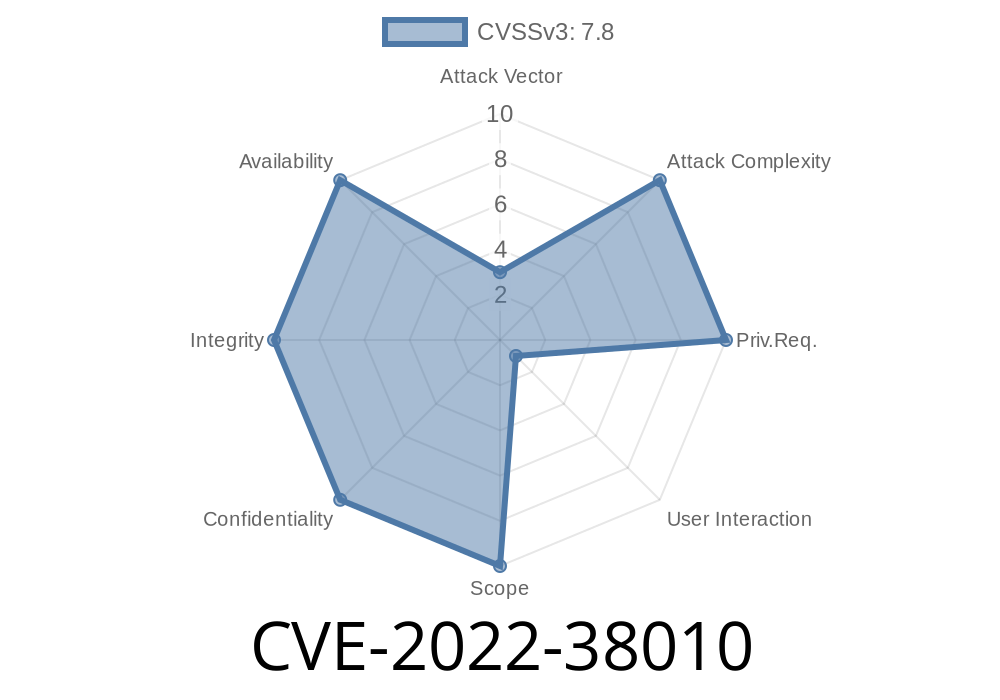
CVE-2022-38010 Microsoft Office Visio Remote Code Execution Vulnerability
This vulnerability is within the OLE ActiveX control, and can be exploited by a remote attacker via the Microsoft Office application. To exploit this vulnerability,
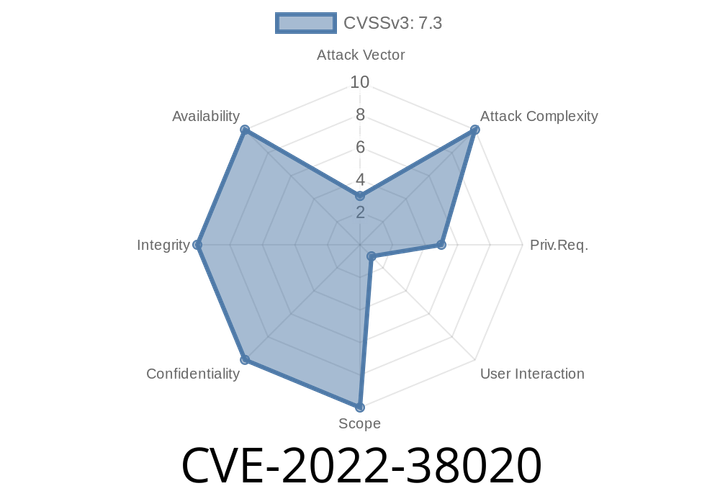
CVE-2022-38020 Visual Studio Code Elevation of Privilege Vulnerability.
This is a critical security issue that could lead to remote code execution on an affected system. Microsoft has released a security update to address
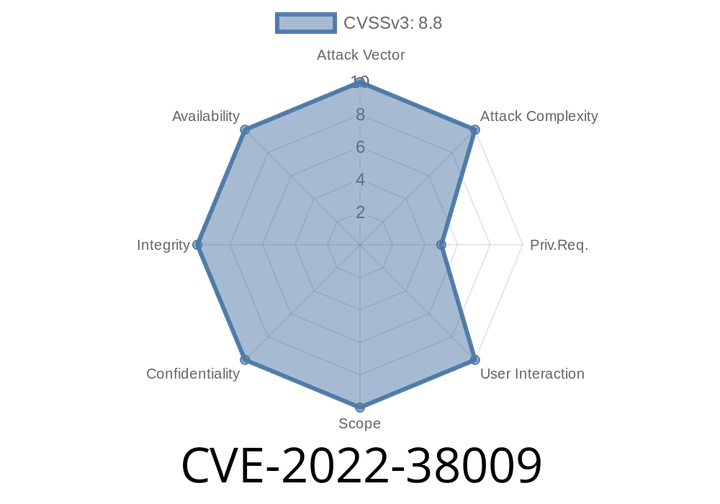
CVE-2022-38009 Microsoft SharePoint Server Remote Code Execution Vulnerability
This issue was reported to Microsoft by Dawid Golunski on November 21, 2017. The vulnerability is due to a lack of input validation on user-supplied
Episode
00:00:00
00:00:00