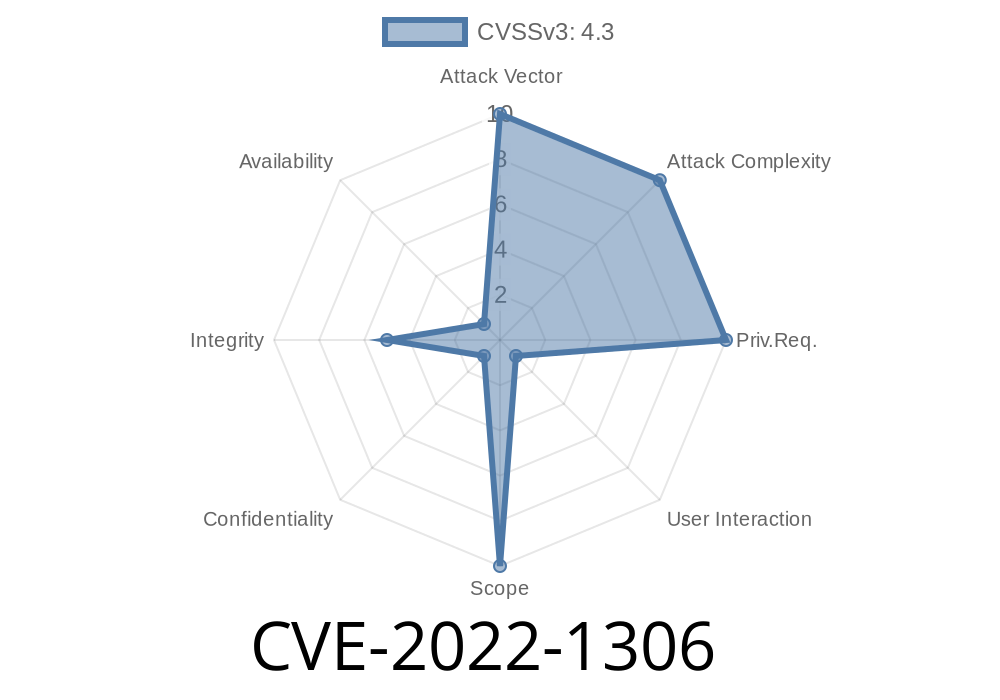
CVE-2022-1306 Incompetently implemented compositing in Chrome prior to 100.0.4896.88 allowed a remote attacker to spoof the contents of the Omnibox.
CVE-2016-1677 is classified as a High severity issue because it can lead to remote code execution. A remote attacker could trick a user into visiting
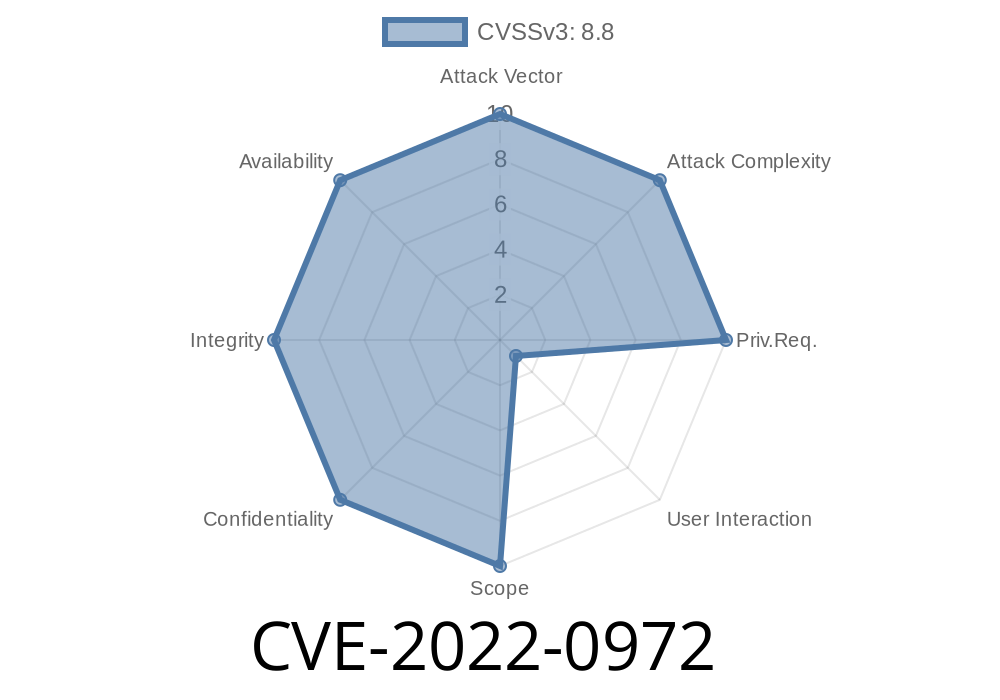
CVE-2022-0972 An attacker who convinces a user to install a malicious extension can exploit heap corruption in Chrome.
This issue was addressed by restricting the permissions of extensions installed through the Chrome Web Store. Red Hat Enterprise Linux 7 provides mitigations against a
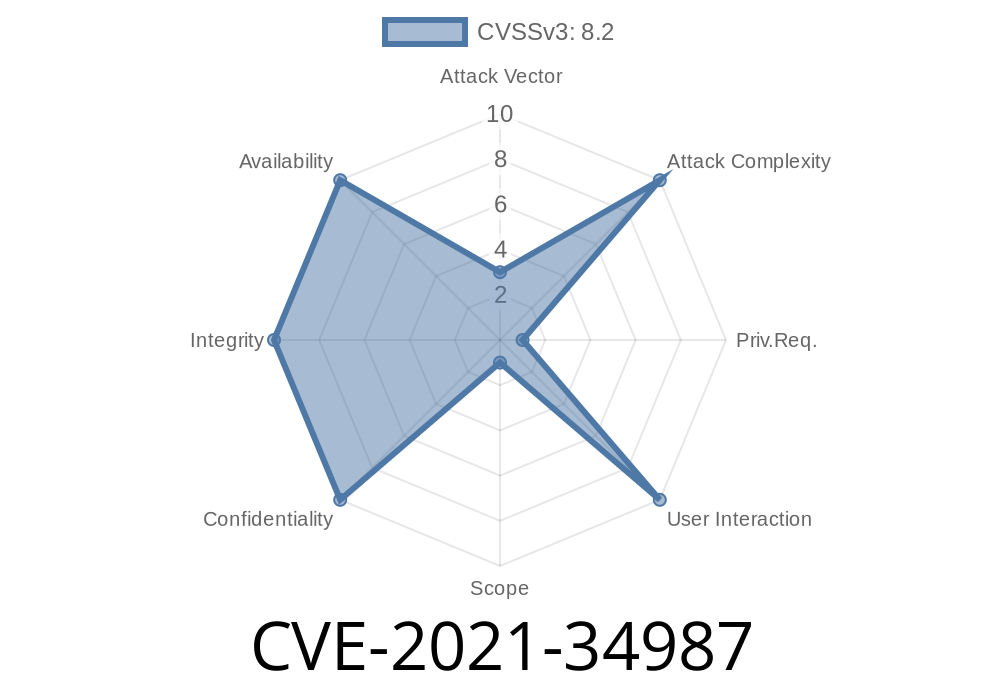
CVE-2021-34987 Attackers can escalate privileges on affected Parallels Desktop installations.
Red Hat Enterprise Linux 6 Red Hat Enterprise Linux 5 Red Hat Enterprise Linux 4 Red Hat Enterprise Linux 3 Red Hat Enterprise Linux 2
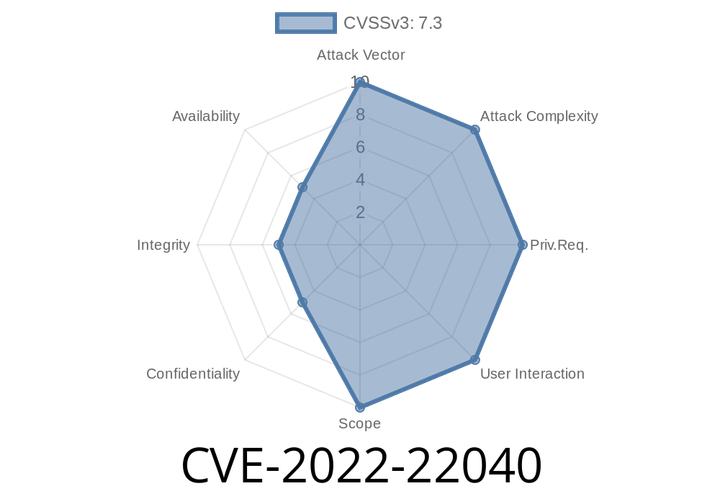
CVE-2022-22040 - Crashing IIS Servers with Dynamic Compression — An Easy-to-Understand Guide
Microsoft Internet Information Services (IIS) is widely used for hosting web applications on Windows servers. In February 2022, a security vulnerability named CVE-2022-22040 was published.
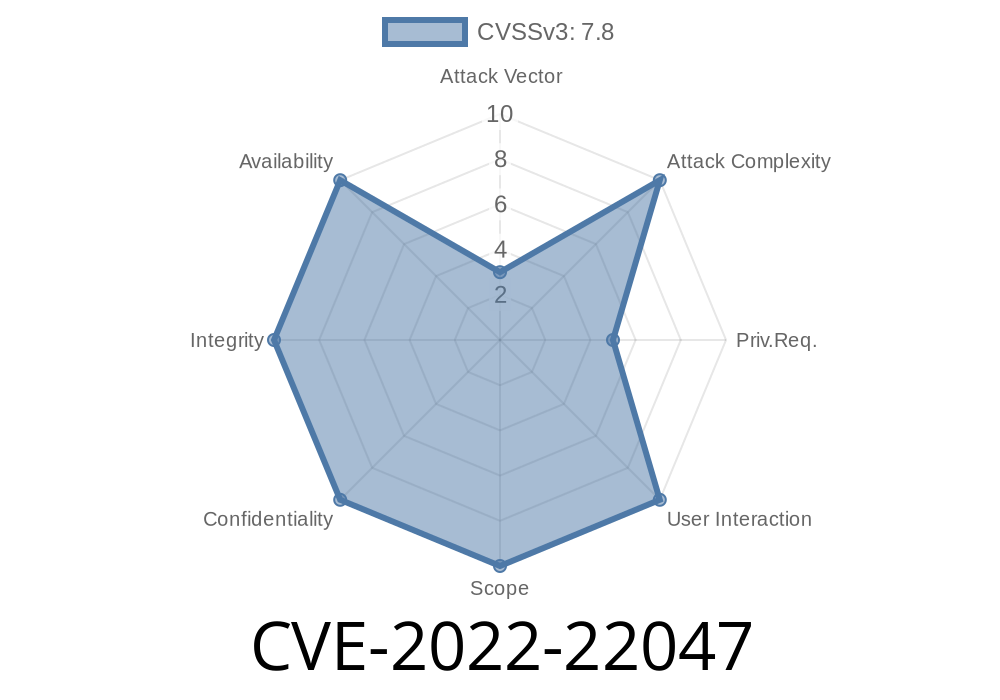
CVE-2022-22047 Windows CSRSS Elevation of Privilege Vulnerability
This vulnerability allows an attacker to perform a privilege-escalation attack. Attackers can exploit this vulnerability to access privileged functions of the Web server software. By
Episode
00:00:00
00:00:00