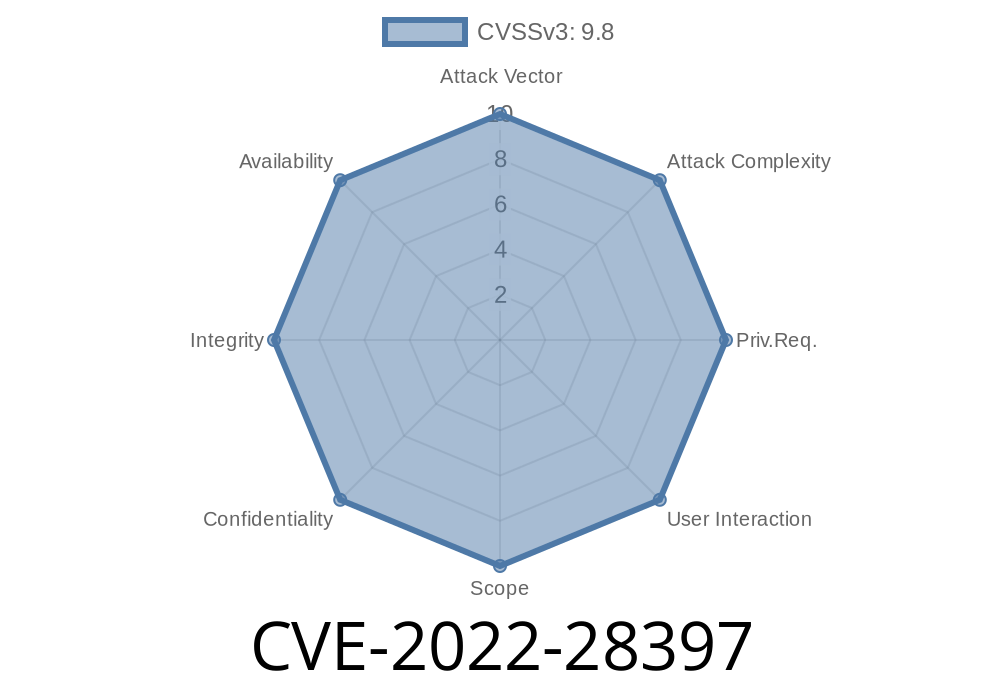
CVE-2022-28397 - **DISPUTED** Arbitrary File Upload in Ghost CMS v4.42.—What You Need to Know
---
Overview
A security advisory surfaced about CVE-2022-28397, which raises concerns about an arbitrary file upload vulnerability in the well-known Ghost CMS—specifically version 4.
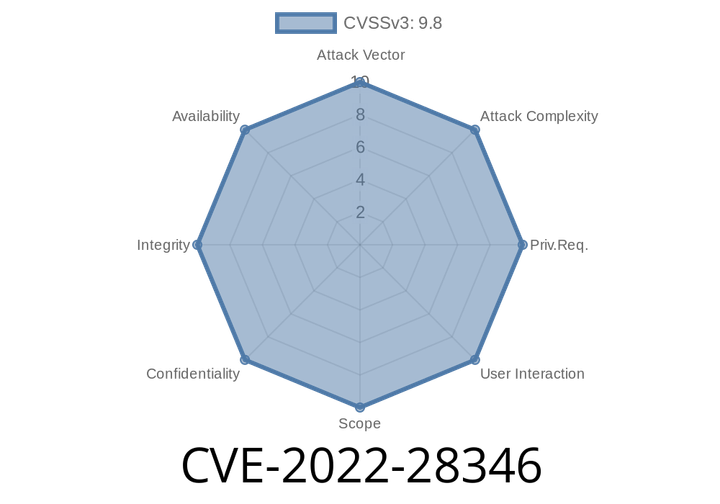
CVE-2022-28346 - How Dictionary Expansion Opened Django to SQL Injection
Django, the famous Python web framework, is known for its robust protection against SQL injection. But in 2022, a serious vulnerability—CVE-2022-28346—was discovered that
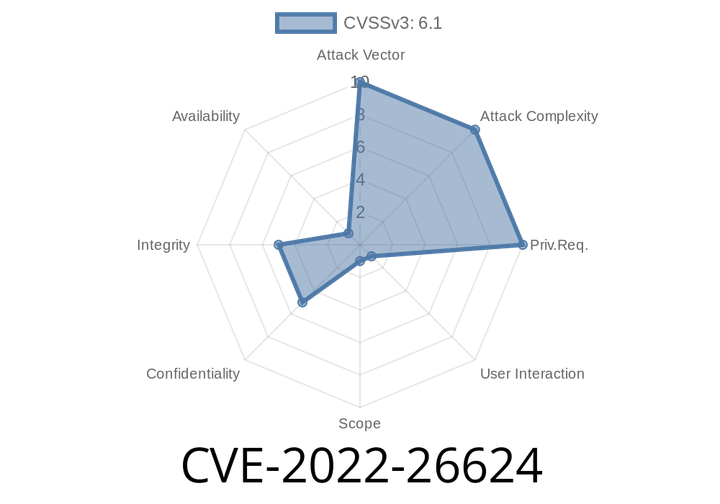
CVE-2022-26624 - Exploiting XSS in Bootstrap v3.1.11 and v3.3.7 via the Title Parameter in /vendor/views/add_product.php
---
Cross-Site Scripting (XSS) is still one of the most dangerous vulnerabilities that can appear in web apps. It lets attackers inject malicious scripts into
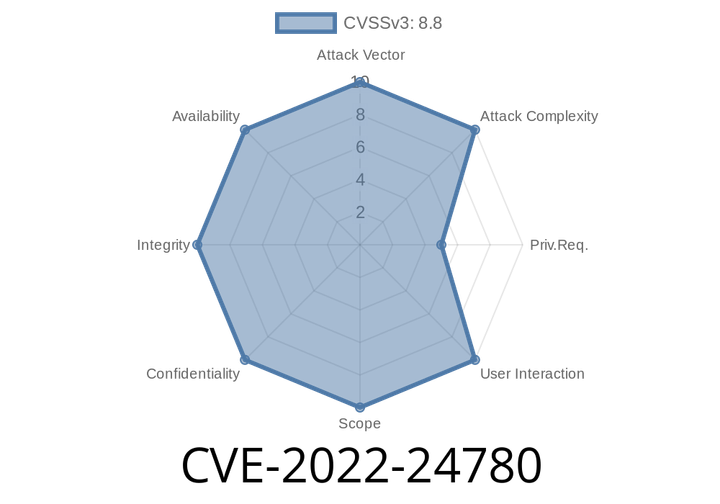
CVE-2022-24780 - Critical RCE in Combodo iTop User Portal Explained
Combodo iTop is a popular open-source web-based ITSM (IT Service Management) tool used globally by service desks and IT departments. In early 2022, a severe
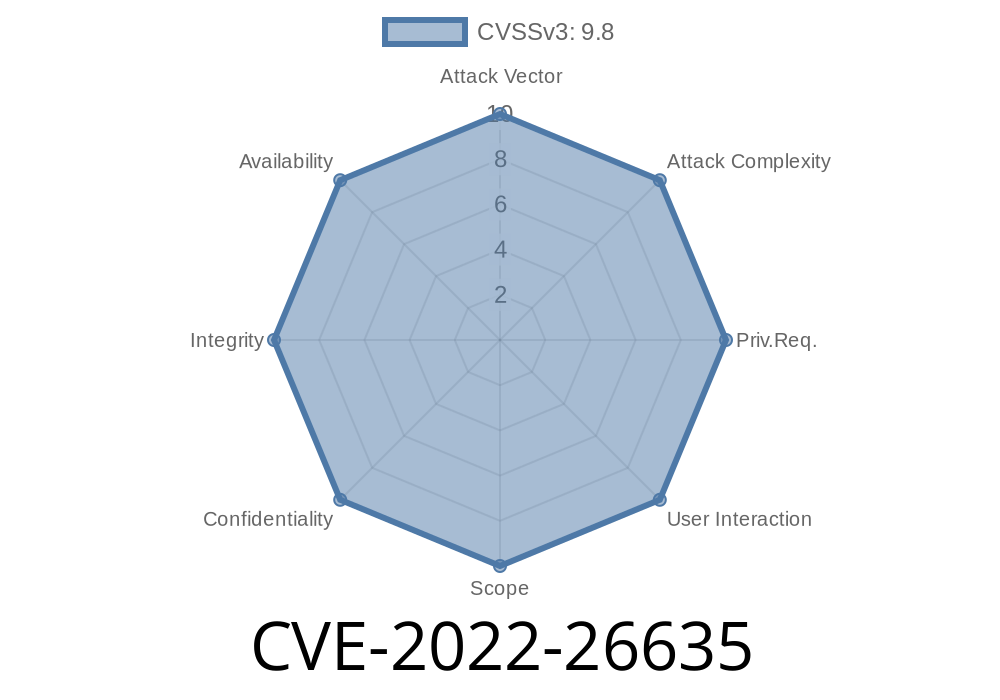
CVE-2022-26635 - CLRF Injection in PHP-Memcached (v2.2. and Below) — Explained with Exploit Details
A critical security risk was discovered in the PHP-Memcached extension up to version 2.2.. This vulnerability, assigned CVE-2022-26635, stems from improper NULL termination in
Episode
00:00:00
00:00:00