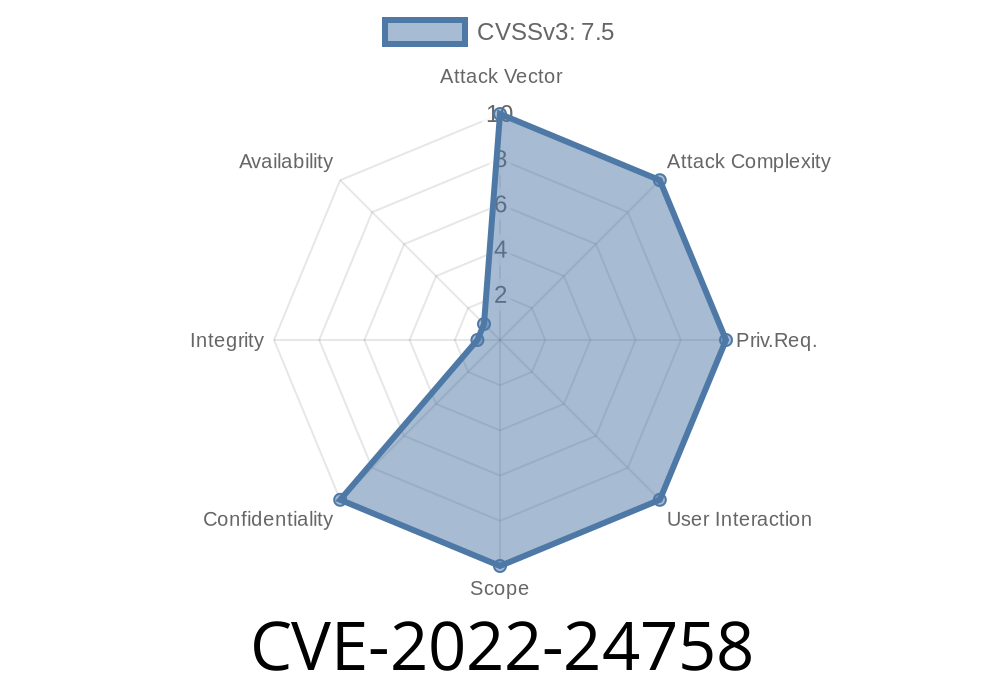
CVE-2022-24758 - How Jupyter Notebook Leaked Sensitive Data in Server Logs
Jupyter Notebook is a powerful, web-based notebook environment used by data scientists, researchers, and students all over the world. It allows users to create and
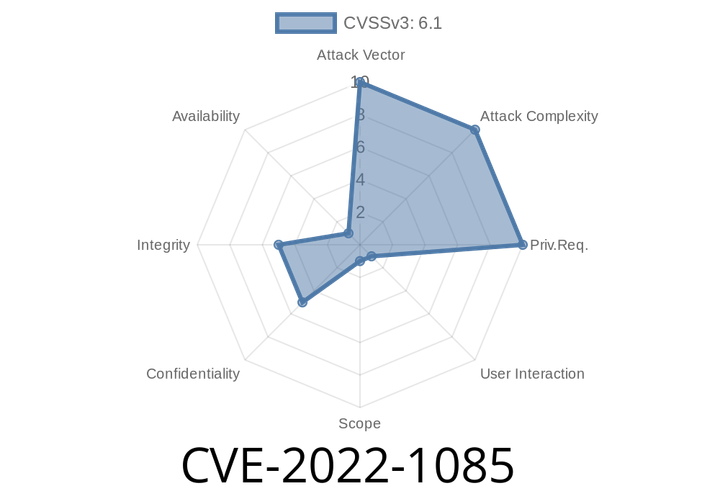
CVE-2022-1085 - Uncovering a XSS Vulnerability in CLTPHP ≤6. – How It Works, Exploit Example, and How to Fix It
In early 2022, a serious vulnerability was found in the popular CLTPHP content management system, affecting versions up to 6.. Tracked as CVE-2022-1085, this flaw
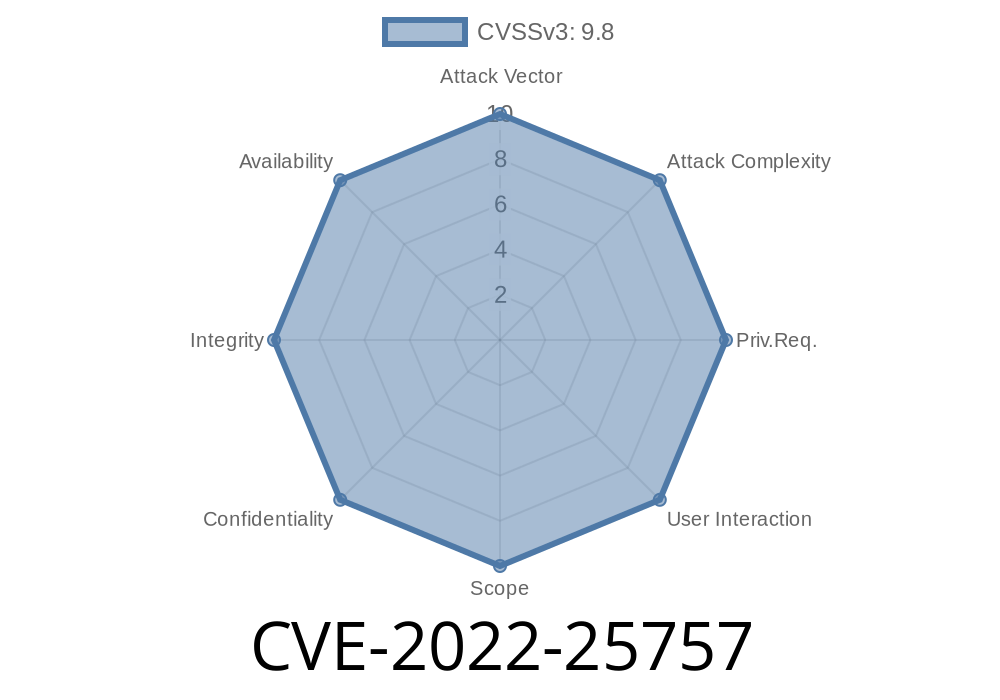
CVE-2022-25757 Lua-cjson picks the last key as the result when decoding JSON with duplicate keys.
Apache APISIX has been found to have a race condition in the processing of unvalidated input. If input is validated and then unvalidated, a race
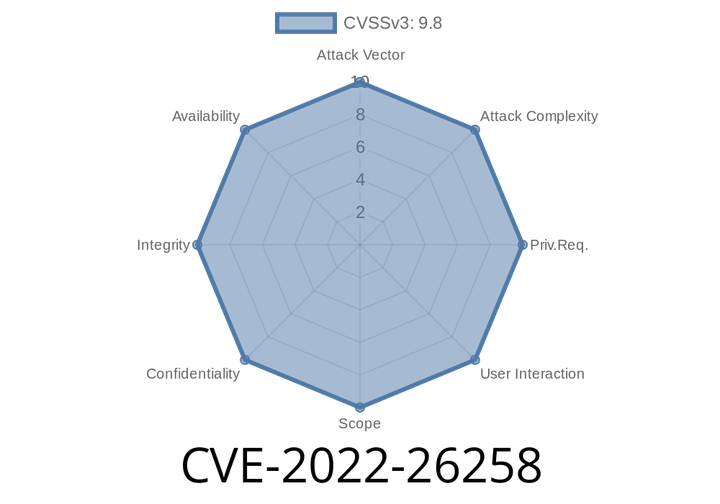
CVE-2022-26258 - Remote Command Execution in D-Link DIR-820L (Firmware 1.05B03) via /lan.asp
The D-Link DIR-820L is a popular wireless router used by many for its affordable price and ease of setup. However, in early 2022, security researchers
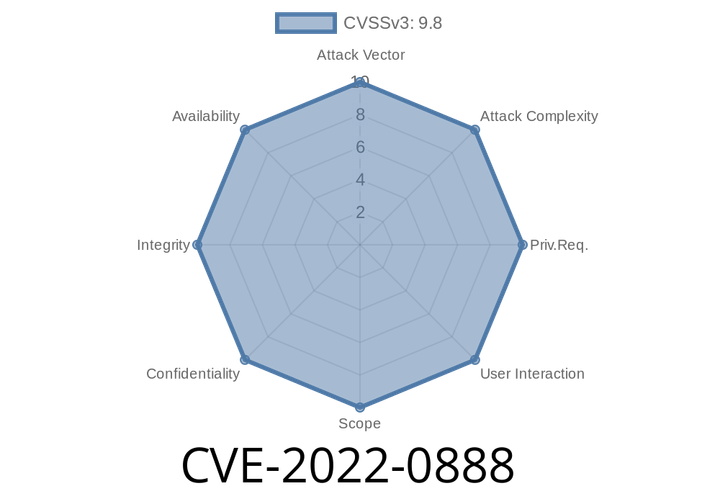
CVE-2022-0888 - Deep Dive into the Ninja Forms File Uploads Extension Vulnerability (Unauthenticated RCE in WordPress)
In early 2022, a critical vulnerability shook the WordPress ecosystem, affecting websites using the popular Ninja Forms - File Uploads Extension plugin. Labeled as CVE-2022-0888,
Episode
00:00:00
00:00:00