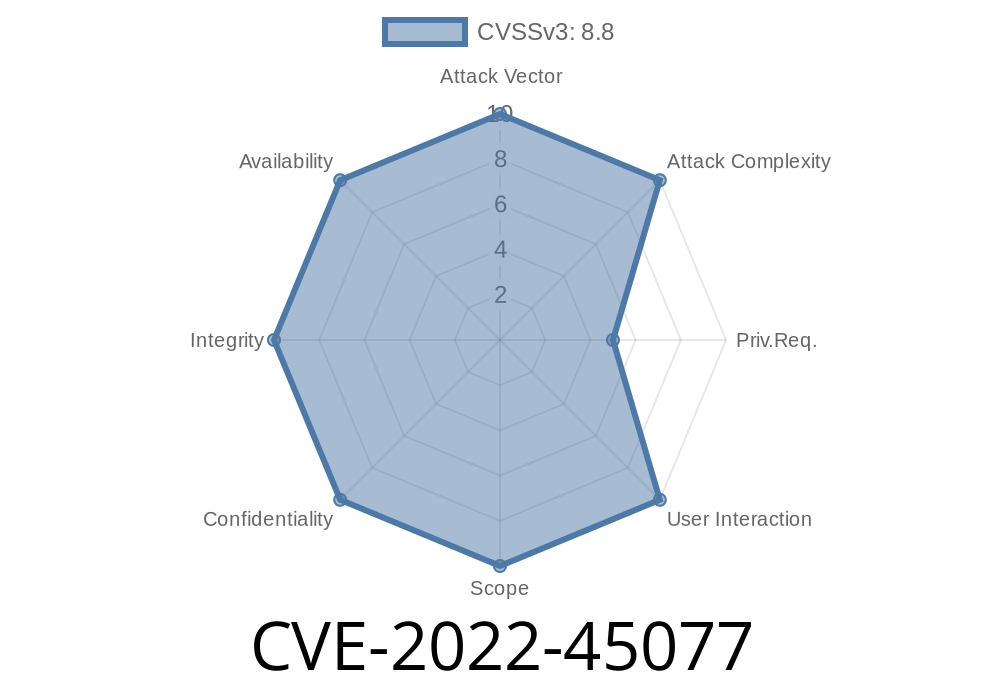
CVE-2022-45077 Auth. (subscriber+) PHP Object Injection vulnerability in Betheme theme <= 26.5.1.4 on WordPress.
This vulnerability is rated as critical severity, due to the fact that it can be exploited by hackers to gain remote access to the target’
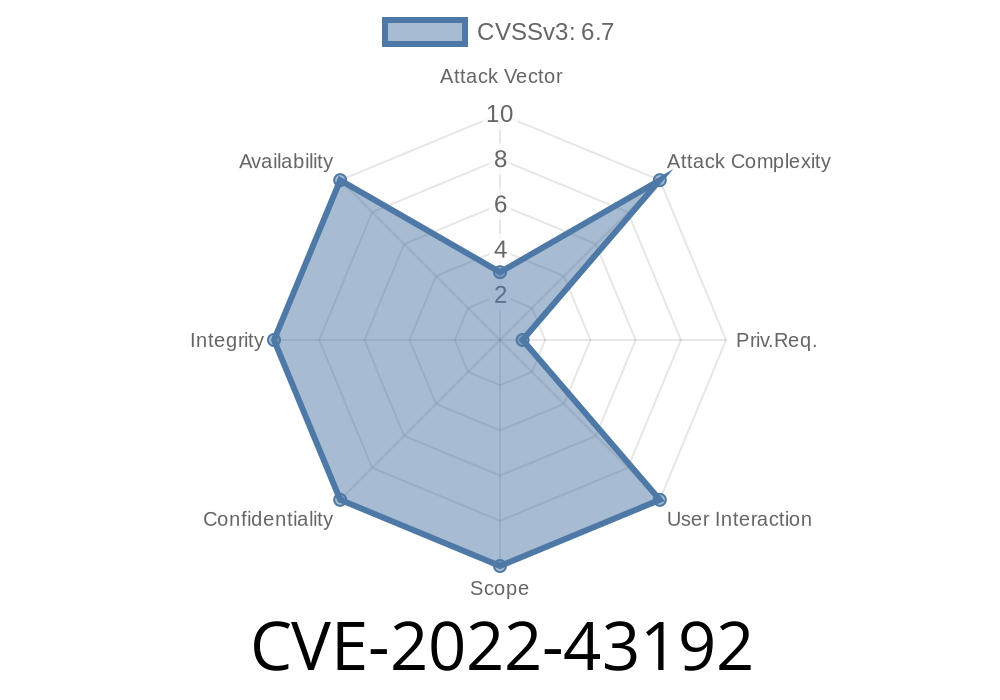
CVE-2022-43192 An upload control component of Dedecms v5.7.101 is vulnerable to an arbitrary code execution attack.
A stack-based buffer overflow exists in the component /dede/file_manage_control.php of Dedecms v5.7.101, which allows remote attackers to execute arbitrary
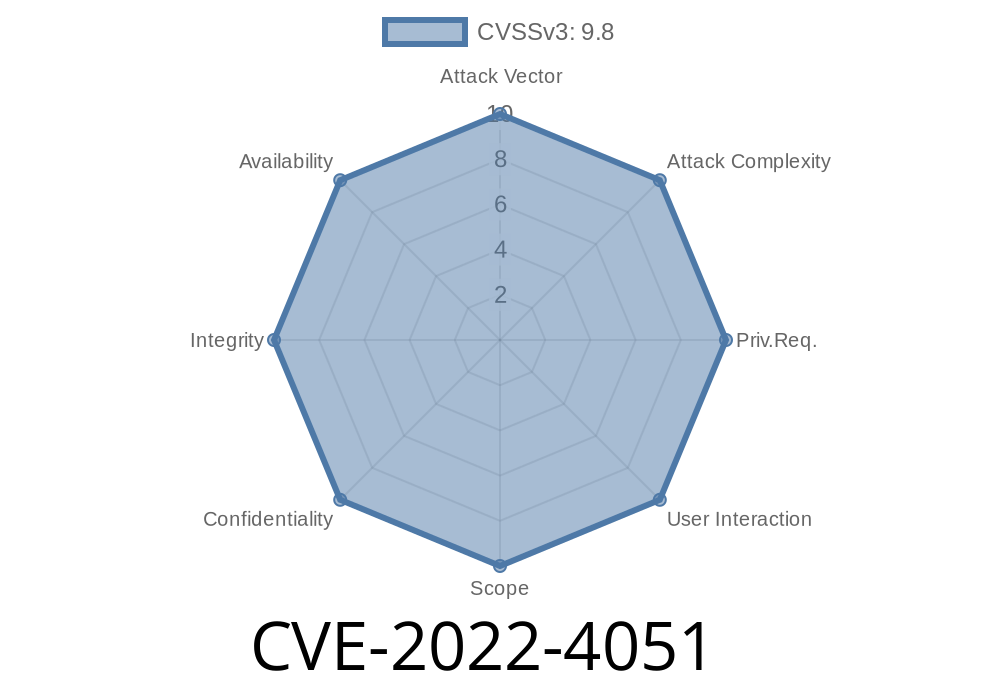
CVE-2022-4051 Hostel Searching Project has a critical vulnerability involving unknown code. The manipulation of the argument property_id leads to sql injection.
The attacker needs to be in contact with the victim in order to exploit this vulnerability. The victim does not have to visit a specific
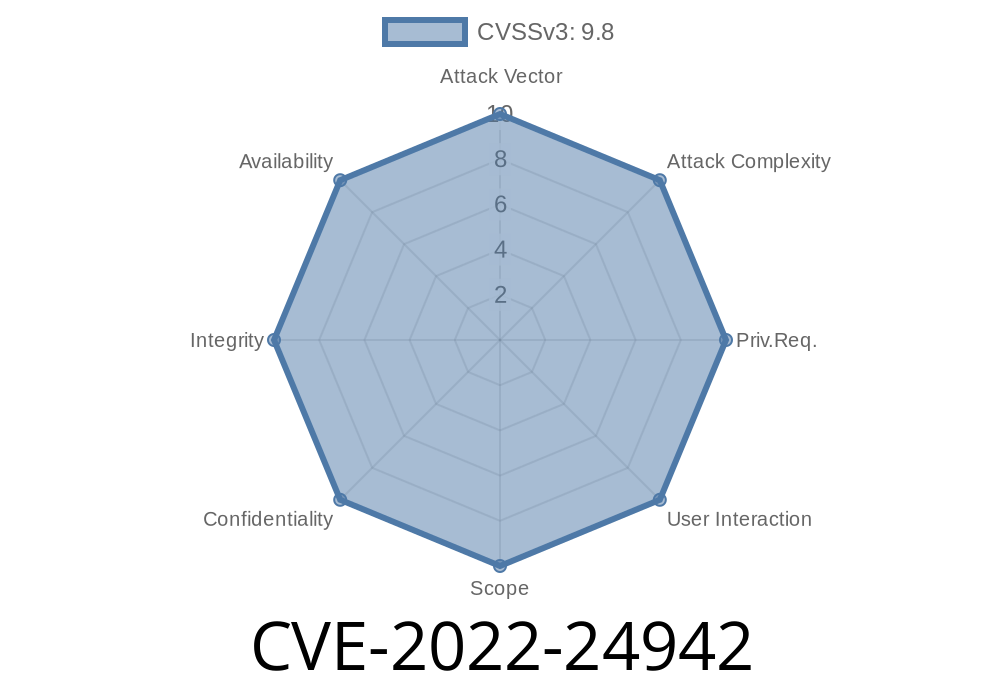
CVE-2022-24942 - Micrium uC-HTTP Heap Buffer Overflow — Exploit Deep Dive
CVE-2022-24942 is a critical heap-based buffer overflow vulnerability found in the HTTP server feature of Micrium uC-HTTP versions up to 3.01.01. Attackers can
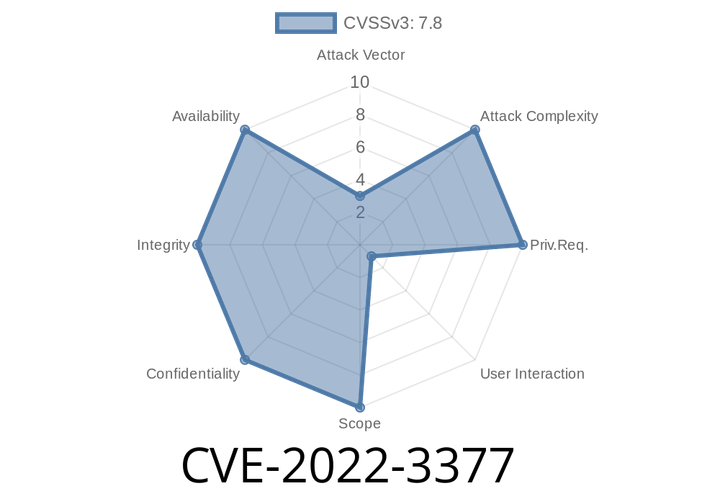
CVE-2022-3377 - Analyzing the FNT File Vulnerability in Horner Automation’s Cscape (RCE Risk Inside)
Horner Automation’s Cscape is an automation software suite commonly used for programming and configuring controllers in industrial environments. In late 2022, a significant vulnerability
Episode
00:00:00
00:00:00