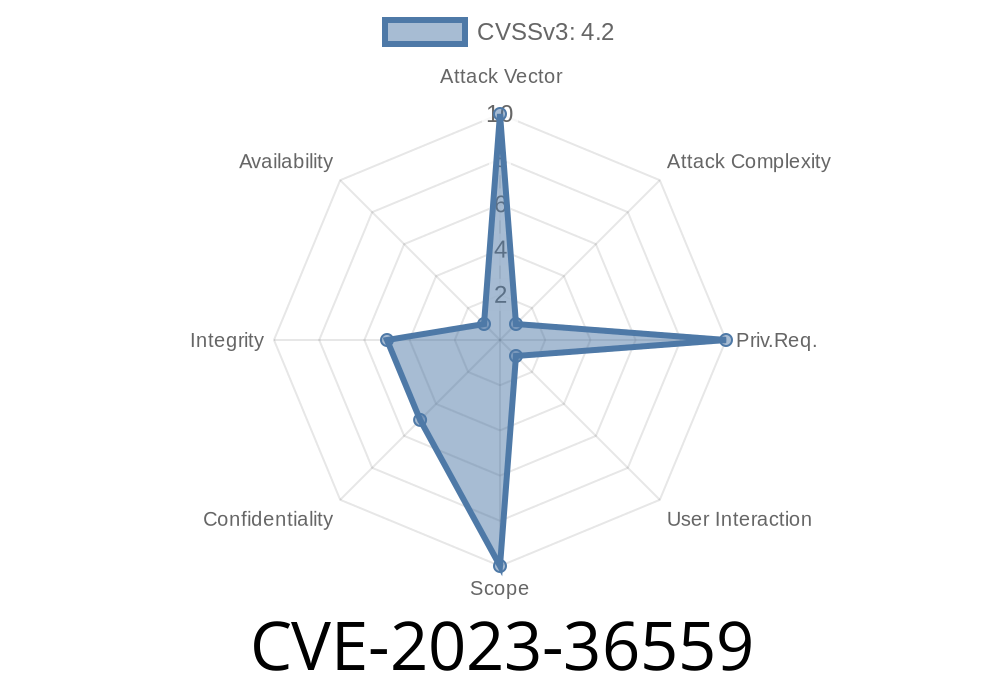
CVE-2023-36559 - Microsoft Edge (Chromium-based) Spoofing Vulnerability Explained With Code and Exploit Example
Cybersecurity vulnerabilities are often complex, technical, and hard to unpack for everyday users. CVE-2023-36559 is a spoofing vulnerability found in Microsoft Edge—the Chromium-based version
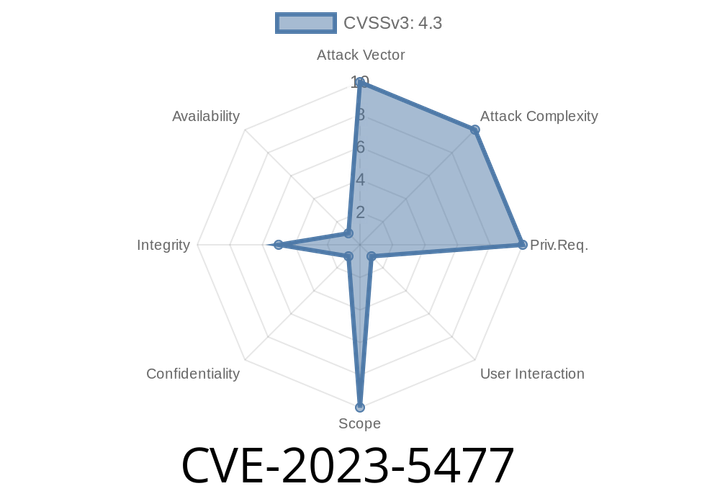
CVE-2023-5477 - How Insecure Chrome Installer Implementation Could Let Local Attackers Slip Through Checks
In October 2023, a security advisory was published for a low-severity vulnerability in Google Chrome's Windows installer, tracked as CVE-2023-5477. The flaw exists
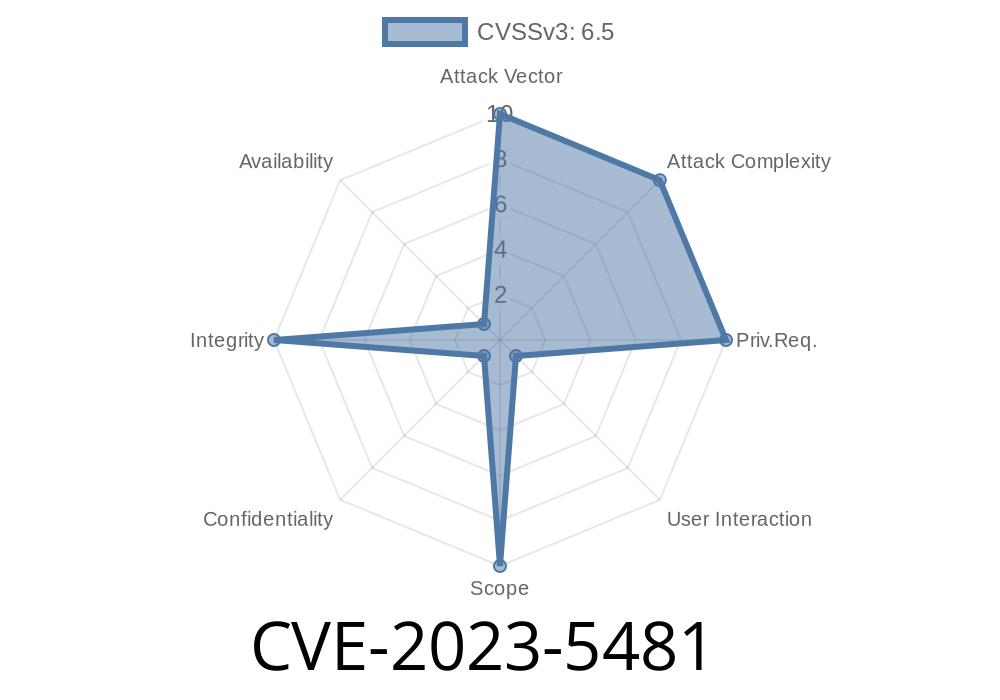
CVE-2023-5481 - How a Chrome Download UI Bug Made You Trust Dangerous Files (With Exploit Example)
CVE-2023-5481 is a security flaw found in Google Chrome’s downloads feature that existed before version 118..5993.70. This vulnerability allowed attackers to spoof
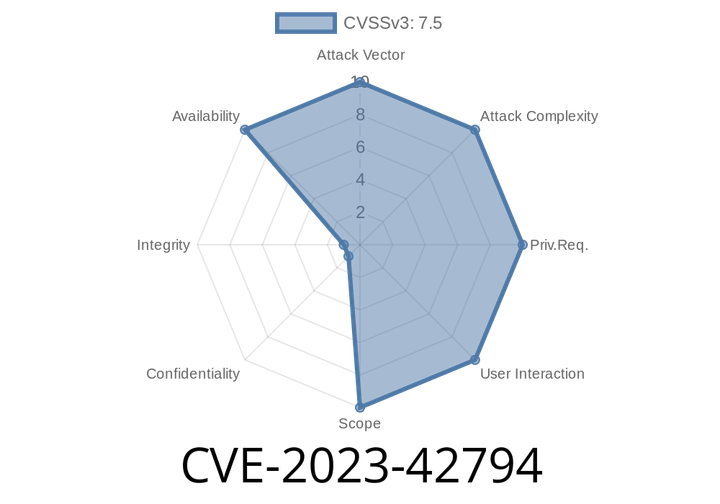
CVE-2023-42794 - Denial of Service in Apache Tomcat from Incomplete Cleanup Vulnerability
---
Apache Tomcat is one of the most popular open-source web servers used for deploying Java applications. In late 2023, a significant vulnerability was discovered—
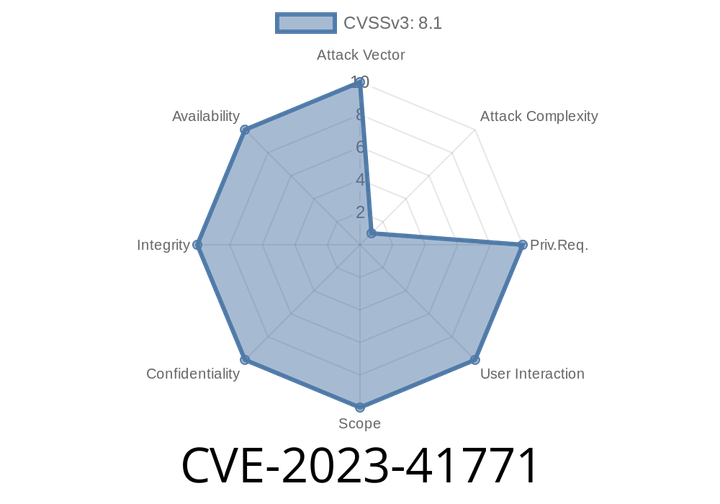
CVE-2023-41771 - Layer 2 Tunneling Protocol Remote Code Execution Vulnerability Explained
In late 2023, the cybersecurity community was rocked by CVE-2023-41771, a critical remote code execution (RCE) vulnerability in the Layer 2 Tunneling Protocol (L2TP) found
Episode
00:00:00
00:00:00