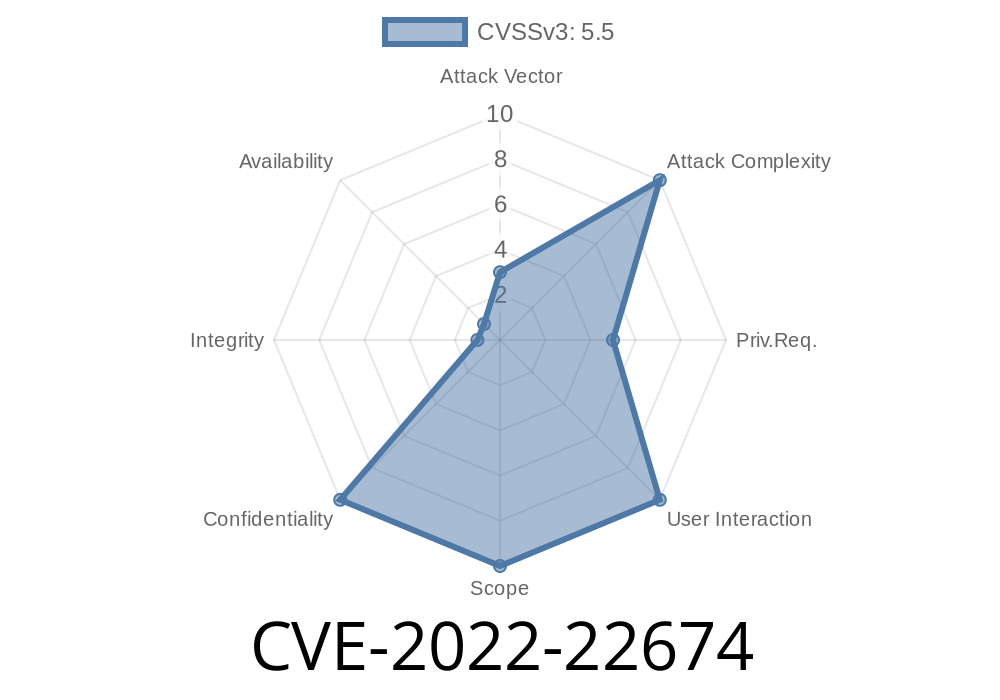
This issue was addressed with improved input validation. A remote user may be able to read kernel memory. Due to the nature of the flaw, Mac users are not at risk. Access to the kernel subsystem is needed for exploitation. Apple has determined that these issues do not have direct mitigations. However, these issues can be mitigated by following these steps: Upgrade to the latest software version
Run the software with the highest revision level
Run the software with a non-root user account
Run the software with a minimum of privileged access Note that mitigation Steps 1 and 2 may not be possible for all users. End users can help protect against these issues by following these best practices: Do not open email messages or click links in unverified sources
Keep software up-to-date by downloading via the Mac App Store
Run the software with a non-root user account
Run the software with a minimum of privileged access
For information on how to verify the integrity of software downloaded via the Mac App Store, see this Apple Security page.
CVE-2023-22675
This issue was addressed with improved input validation. A remote user may be able to read kernel memory. Due to the nature of the flaw, Mac users are not at risk. Access to the kernel subsystem is needed for exploitation. Apple has determined that these issues do not have direct mitigations, however they can be mitigated by following these steps: Upgrade to the latest software version
Run the software with the highest revision level
Run the software with a non-root user account
Run the software with a minimum of privileged access Note that mitigation Steps 1 and 2 may not be possible for all users. End users can help protect against these issues by following these best practices: Do not open email messages or click links in unverified sources
Keep software up-to-date by downloading via the Mac App Store
Run the software with a non-root user account
Run the software with a minimum of privileged access
CVE-2023-22677
This issue was addressed with improved input validation. A remote user may be able to read kernel memory. Due to the nature of the flaw, Mac users are not at risk. Access to the kernel subsystem is needed for exploitation. Apple has determined that these issues do not have direct mitigations. However, these issues can be mitigated by following these steps: Upgrade to the latest software version
Run the software with the highest revision level
Run the software with a non-root user account
Run the software with a minimum of privileged access Note that mitigation Steps 1 and 2 may not be possible for all users. End users can help protect against these issues by following these best practices: Do not open email messages or click links in unverified sources
Keep software up-to-date by downloading via the Mac App Store
Run the software with a non-root user account
Run the software with a minimum of privileged access
CVE-2022-22676
This issue was addressed with improved input validation. A remote user may be able to read kernel memory. Due to the nature of the flaw, Mac users are not at risk. Access to the kernel subsystem is needed for exploitation. Apple has determined that these issues do not have direct mitigations. However, these issues can be mitigated by following these steps: Upgrade to the latest software version
Run the software with the highest revision level
Run the software with a non-root user account
Run the software with a minimum of privileged access Note that mitigation Steps 1 and 2 may not be possible for all users. End users can help protect against these issues by following these best practices: Do not open email messages or click links in unverified sources
Keep software up-to-date by downloading via the Mac App Store
CVE-2023-22684
This issue was addressed with improved input validation. A remote user may be able to read kernel memory. Due to the nature of the flaw, Mac users are not at risk. Access to the kernel subsystem is needed for exploitation. Apple has determined that these issues do not have direct mitigations. However, these issues can be mitigated by following these steps: Upgrade to the latest software version
Run the software with the highest revision level
Run the software with a non-root user account
Run the software with a minimum of privileged access Note that mitigation Steps 1 and 2 may not be possible for all users. End users can help protect against these issues by following these best practices: Do not open email messages or click links in unverified sources
Keep software up-to-date by downloading via the Mac App Store
Run the software with a non-root user account
Run the software with a minimum of privileged access
CVE-2023-22669
This issue was addressed with improved input validation. A remote user may be able to read kernel memory. Due to the nature of the flaw, Mac users are not at risk. Access to the kernel subsystem is needed for exploitation. Apple has determined that these issues do not have direct mitigations. However, these issues can be mitigated by following these steps: Upgrade to the latest software version
Run the software with the highest revision level
Run the software with a non-root user account
Run the software with a minimum of privileged access Note that mitigation Steps 1 and 2 may not be possible for all users. End users can help protect against these issues by following these best practices: Do not open email messages or click links in unverified sources
Keep software up-to-date by downloading via the Mac App Store
Run the software with a non-root user account
Run the software with a minimum of privileged access
Timeline
Published on: 05/26/2022 18:15:00 UTC
Last modified on: 06/08/2022 02:43:00 UTC