This can be exploited through a maliciously crafted email where the user is persuaded to open the message with the click of a link. If the link is clicked, the malicious code on the victim’s computer can exploit the permissions issue. A similar issue exists in Oracle VirtualBox. A guest operating system running on a virtual machine can exploit the missing permission check to access the virtual hard disk. Due to the virtual nature of the hard disk, this can be done without any additional privileges. Additionally, there is another unpatched vulnerability in Oracle VirtualBox that can be exploited as a privilege escalation. This can be done by running a malicious virtual machine and exploiting the unpatched vulnerability in Oracle VirtualBox.
Oracle VirtualBox Vulnerabilities
Oracle VirtualBox is a piece of software that allows users to create and run virtual machines on their computer. Oracle VirtualBox is an open source product, which means that there are many different people who are free to take the program and modify it for their own purposes. A flaw in the software was discovered by a security researcher named Will Dormann in July of 2016. The vulnerability is called CVE-2016-3620. The vulnerability exists within how Oracle VirtualBox handles memory allocation when running virtual machines under the Linux kernel’s KVM hypervisor. When this vulnerability manifests, it allows attackers to gain control over the host machine without any additional privileges needed.
IDEA Highlight:
Vulnerability and Threat
Vulnerabilities are security vulnerabilities in software or hardware, which can be exploited by malicious entities. This is a pretty standard definition of what we mean when we use the word "vulnerability." However, to provide context for our definition, we will give an example of how this vulnerability would be exploited.
In the case of the maliciously crafted email where the user is persuaded to open the message with the click of a link, there is an issue where permissions are not checked before executing code on the device. This allows for a malicious code to run on your system without any additional privileges. The location where this vulnerability exists is in Oracle VirtualBox and that vulnerability can be exploited as a privilege escalation. So basically, if you're running Oracle VirtualBox and you're using it to host virtual machines with guest operating systems on them, there's an unpatched vulnerability that can be exploited by those guest operating systems without any additional privileges.
Oracle VirtualBox – Privilege Escalation and File System Privilege escalation
There is a privilege escalation vulnerability in Oracle VirtualBox. This can be done by creating a malicious virtual machine and exploiting the unpatched vulnerability in Oracle VirtualBox. The result of this is that it allows an attacker with access to the host system to easily gain control of the whole machine.
Oracle VirtualBox has been patched for both privilege escalation vulnerabilities, but they are still not fixed. There is also another unpatched vulnerability in Oracle VirtualBox that can be exploited as a privilege escalation. This can be done by running a malicious virtual machine and exploiting the unpatched vulnerability in Oracle VirtualBox.
Oracle VirtualBox CVEs and How to Protect Yourself
Oracle VirtualBox is an open-source virtual machine for x86-64 and Itanium that runs on Windows, Linux, Mac OS X, Solaris, FreeBSD, and other Unixes. Oracle VirtualBox is vulnerable to a number of vulnerabilities that make it possible for an attacker to gain control of the affected system.
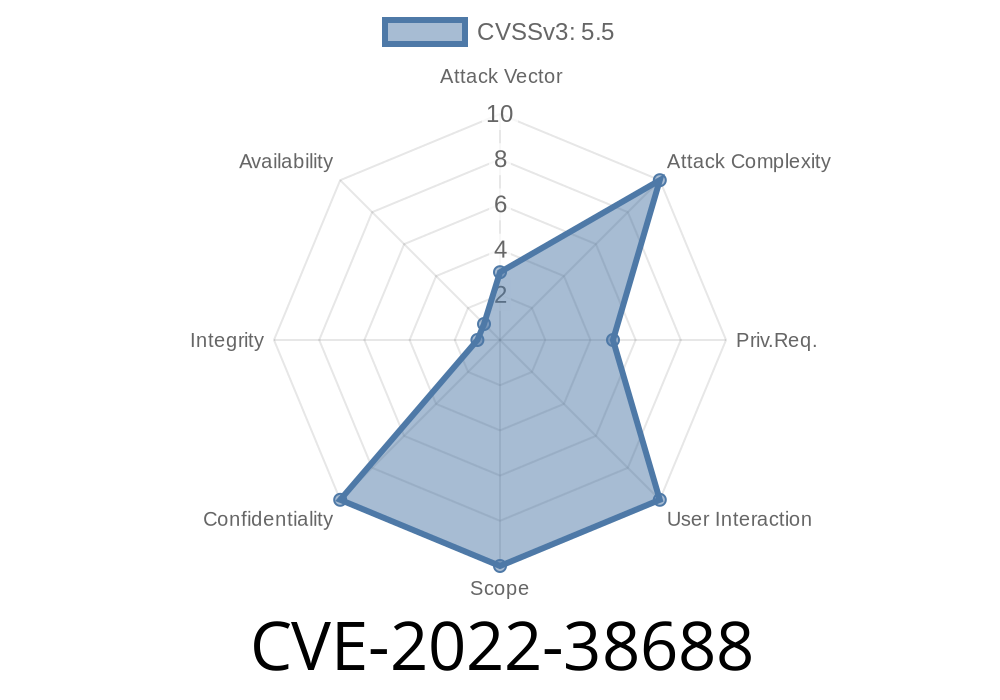
There are three CVEs (Common Vulnerabilities and Exposures numbers) that have been assigned to vulnerabilities in Oracle VirtualBox. CVE-2022-38688 is a vulnerability where maliciously crafted emails can cause the user to click a link in the email which executes code on the computer. The exploit creates a new virtual machine with administrator privileges running as the virtual machine’s root user.
Another vulnerability is CVE-2017-9071 which can be exploited by guests operating systems running on guest operating systems in a virtual machine which has a hard disk access permissions issue. Due to this lack of permissions checking within Oracle VirtualBox, an attacker could execute code with root privileges on the host operating system because they are running as a guest operating system. There is also another unpatched vulnerability in Oracle VirtualBox which can be exploited as privilege escalation if one maliciously created virtual machine runs inside another maliciously created virtual machine. The exploitation chain then allows all of the guest operating systems run their own set of commands without any restrictions from their normal host operating system.
Timeline
Published on: 10/14/2022 19:15:00 UTC
Last modified on: 10/17/2022 19:59:00 UTC