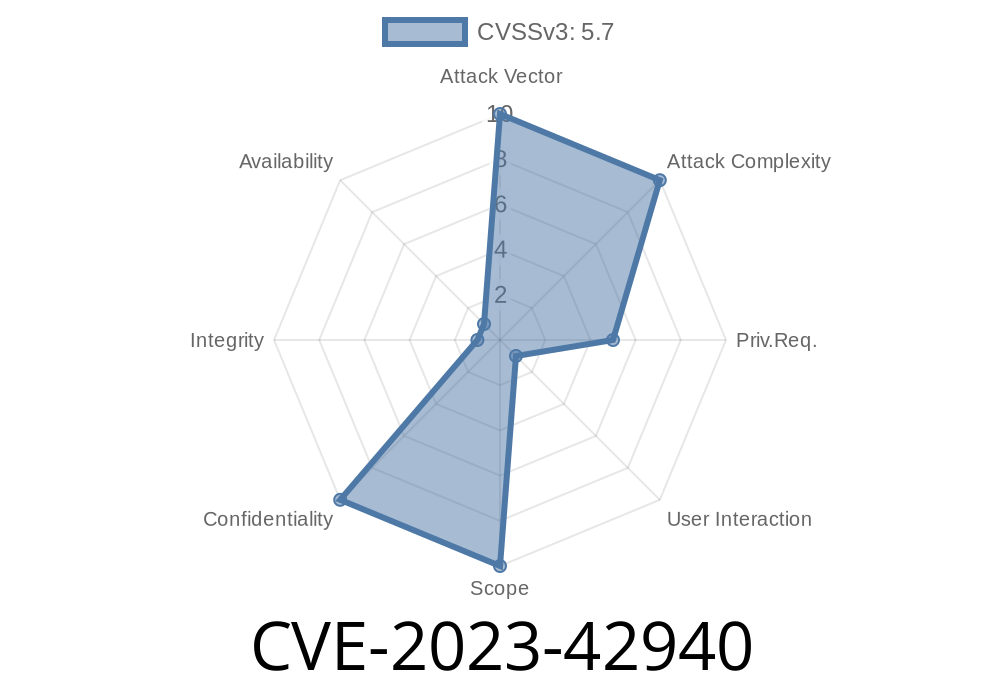
CVE-2023-42940 is a security vulnerability that drew attention in late 2023, affecting macOS Sonoma and potentially earlier versions. The bug lived in macOS’s built-in screen sharing routine, and it could cause a user to accidentally share their screen’s *wrong content* — that is, something they didn’t intend to show.
This post explains the issue in easy terms, explores how this bug works (with actual code hints and links), and walks through what Apple did in macOS Sonoma 14.2.1 to fix it.
What Went Wrong?
Whenever you share your screen — for instance, over FaceTime, Zoom, or macOS’s own Screen Sharing tool — the system tries to show only what you pick. If you select a particular window or desktop, the expectation is your privacy is protected. But under the hood, things can get tricky due to the way macOS managed *session tracking*.
With CVE-2023-42940, due to a session tracking failure, the content being transmitted may not match what you chose to share. Essentially, something from another workspace, desktop, or application could appear in the stream.
Real-World Consequences
If you had a confidential document or private message on your screen, and accidentally shared it to a colleague, manager, or even a stranger, you could suffer embarrassment—or worse.
Technical Details
While Apple didn’t open-source the full bug report, careful parsing of their public release notes and security updates gives us clues. The issue is tracked at Apple's Security Updates:
> A session rendering issue was addressed with improved session tracking.
> Impact: A user who shares their screen may unintentionally share the incorrect content.
Where Did the Bug Occur?
macOS manages multiple windows, spaces, and screens. When you start screen sharing, the system needs to “render” (collect and stream) the right graphical content.
Poor *session tracking* means the system may pass the context of the wrong user session to the rendering engine. For example, you might *think* you’re sharing Safari, but the actual video includes part of Messages or Notes from another desktop workspace.
Here's a conceptual code snippet (not Apple's actual code, which is proprietary)
// Pseudocode: old session render logic
func startScreenShare(selectedContent: Window) {
// Somewhere in old code:
let renderSession = getCurrentRenderSession()
renderSession.startStreaming(content: selectedContent)
// Bug: Incorrect session mapping!
}
The mistake? getCurrentRenderSession() may grab the *active* session, not the *user-selected* one.
Here's a basic workflow that demonstrates the conditions
# 1. Open several desktops (Spaces) with different apps in each.
# 2. Use a macOS screen sharing tool, select "Window" (not entire display).
# 3. While sharing, quickly switch to another Space.
# 4. The recipient may see flashes or persistent images from other apps.
Note: There’s no known public PoC for this bug since it relies on GUI interaction and session switching.
References & Official Links
- Apple Security Updates: macOS Sonoma 14.2.1
- NIST CVE Record for CVE-2023-42940
Remediation
Apple’s fix, described as “improved session tracking,” most likely involves strict mapping between user-chosen content and what’s rendered for remote viewers. Something like:
// Patched logic
func startScreenShare(selectedContent: Window) {
let trustedSession = mapSelectionToTrustedSession(selectedContent)
trustedSession.lock()
trustedSession.startStreaming(content: selectedContent)
}
How to protect yourself:
Summary
CVE-2023-42940 highlights how even mature operating systems slip up in subtle ways: session confusion can lead to privacy leaks. Thanks to quick action from Apple, the flaw was squashed in macOS Sonoma 14.2.1. If you use Apple devices for sensitive work, updating is your best defense.
If you want to learn more
- Apple Platform Security Guide
- How to use Screen Sharing on Mac (Apple)
Timeline
Published on: 12/19/2023 22:15:07 UTC
Last modified on: 01/04/2024 14:56:32 UTC