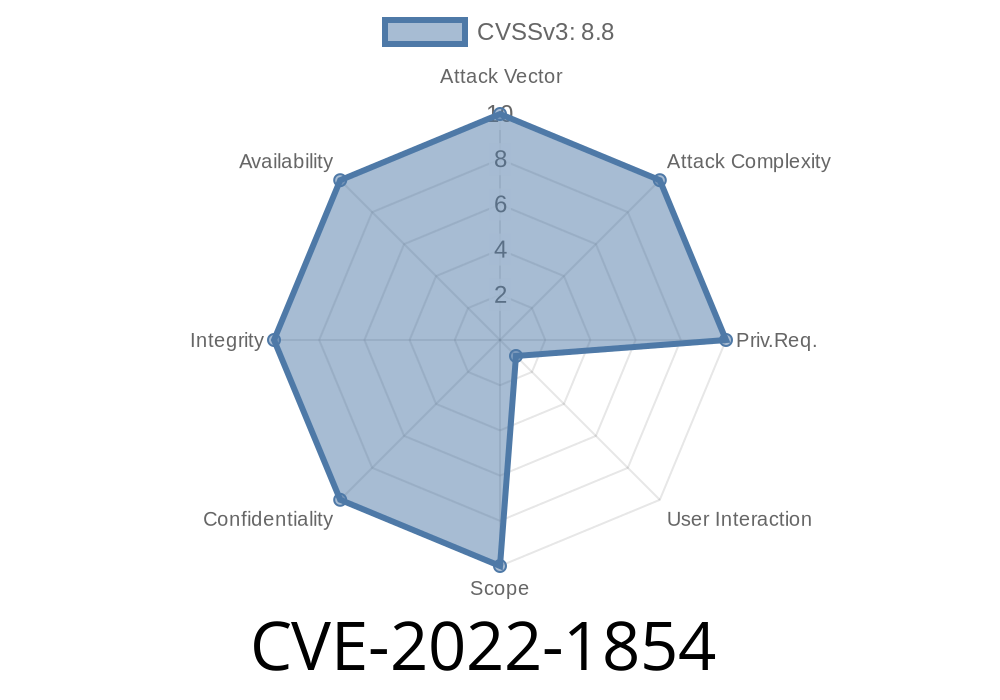
CVE-2022-1854 An attacker can exploit heap corruption in Google Chrome to hijack browser sessions.
CVE-2015-1240 was discovered in Google V8, a highly-optimized JavaScript engine. By crafting synthetic input and injecting code into the memory, an attacker could exploit the
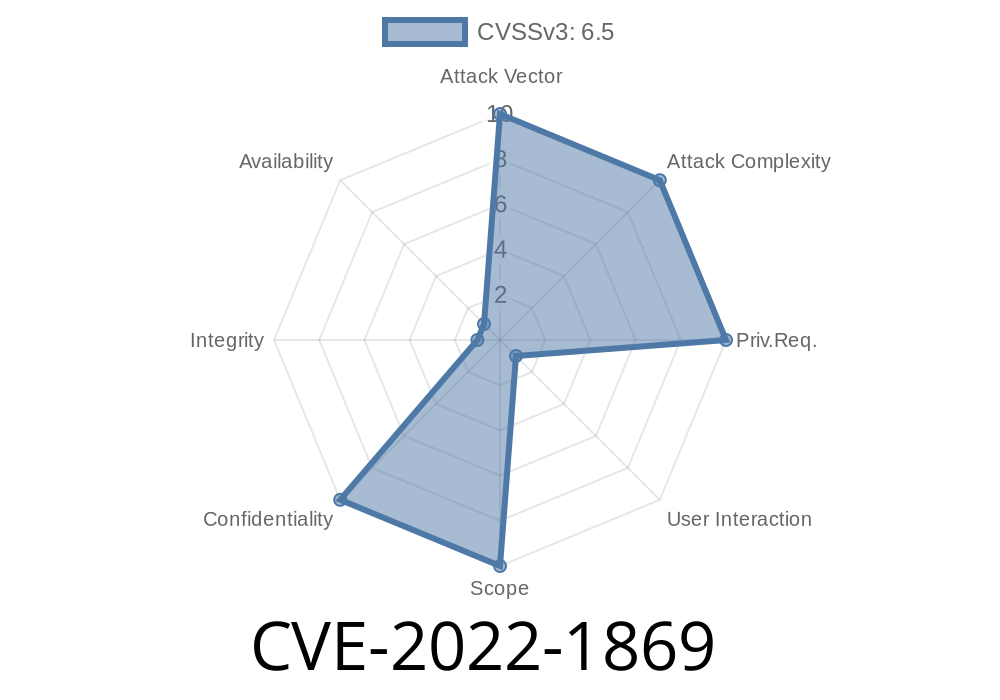
CVE-2022-1869 Confusion in V8 allowed a remote attacker to exploit heap corruption.
This issue did not affect most users, as the browser tried to prevent this by performing strict type enforcement. However, since the type system was
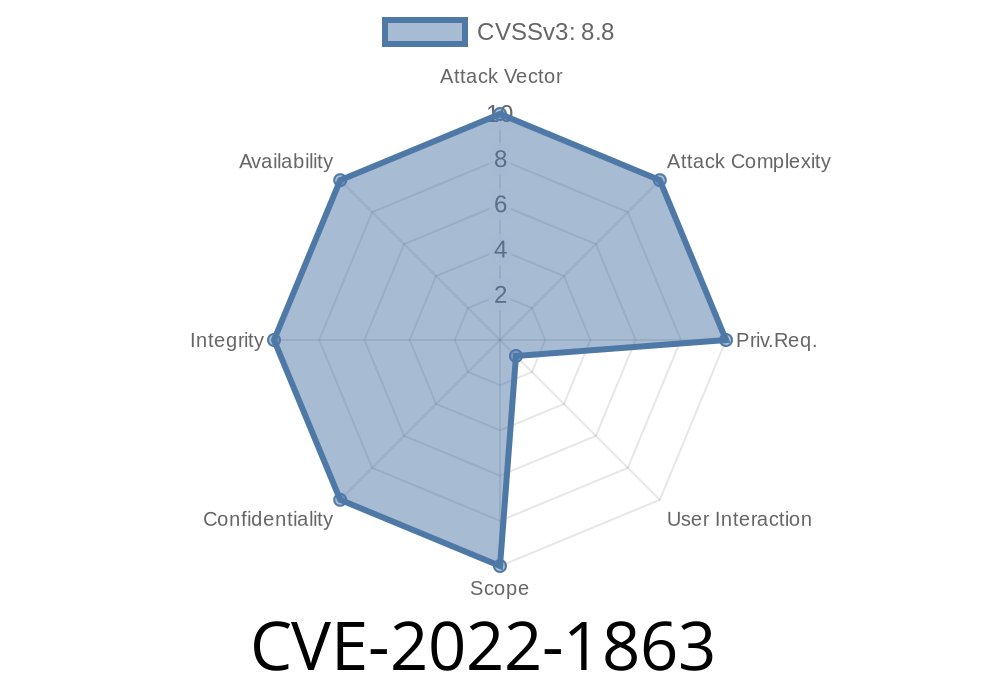
CVE-2022-1863 An attacker could exploit heap corruption in Google Chrome after 102.0.5005.61 to potentially exploit after free.
Exploitation resulted in a potentially exploitable crash and another potential vector for attack. Google Chrome prior to 102.0.5 prior to allowing insecure extensions
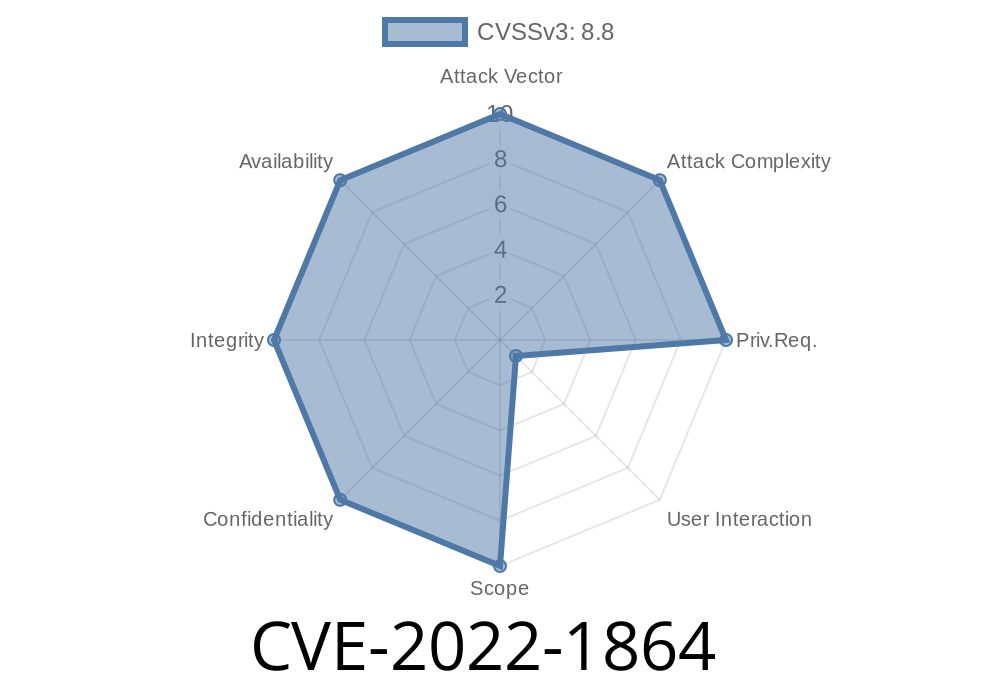
CVE-2022-1864 Attackers can exploit heap corruption in Google Chrome after an attack that leads a user to install a malicious extension.
Google Note: This vulnerability was disclosed by Tavis Ormandy of the Google Security Team on Dec 8, 2017. There is no active trust associated with
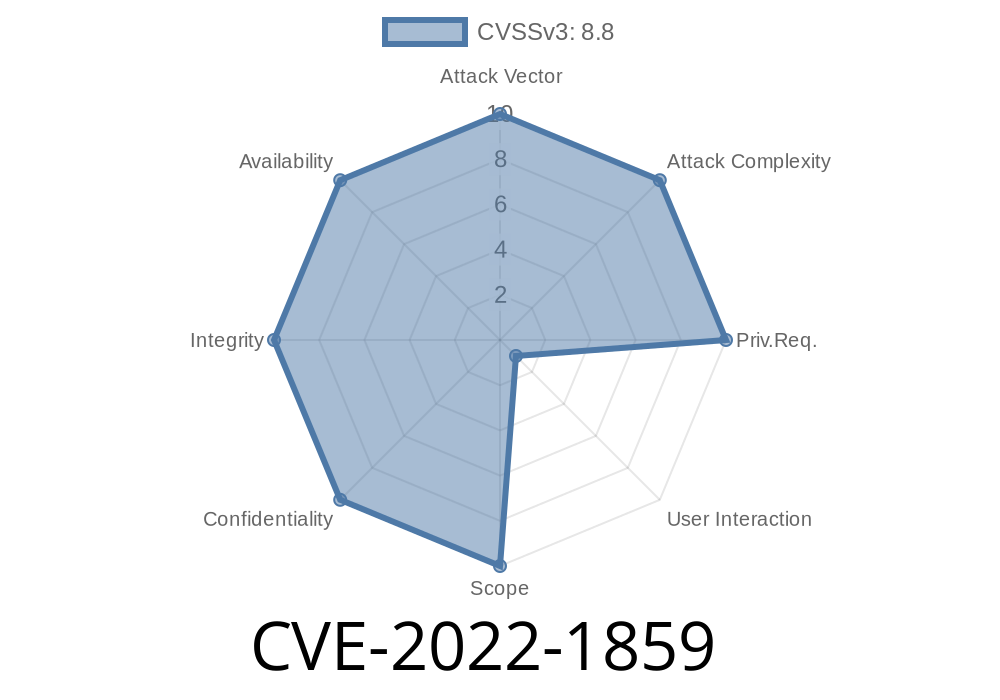
CVE-2022-1859 An attacker who convinced a user to perform specific actions could exploit heap corruption after an update.
CVE-2018-6040 was discovered by Dawid Wos of Critical Intelligence. In some circumstances, it was possible for remote attackers to bypass the Mixed Content Restriction (MCS)
Episode
00:00:00
00:00:00